| CATEGORII DOCUMENTE |
| Asp | Autocad | C | Dot net | Excel | Fox pro | Html | Java |
| Linux | Mathcad | Photoshop | Php | Sql | Visual studio | Windows | Xml |
![]()

Windows Server 2003 Service Pack 1
Product Overview
Abstract
Windows Server 2003 Service Pack 1 (SP1) delivers on Microsoft's Trustworthy Computing initiative and illustrates Microsoft's commitment to continually creating software products with enhanced security, increased reliability, and simplified administration. Windows Server 2003 SP1 builds upon the impressive track record of the award-winning Windows Server 2003 operating system by introducing numerous refinements in addition to supplying cumulative system updates. Deploying SP1 will help enterprises across all industries and segments enhance security, increase reliability, and simplify administration through guided attack surface reduction.
This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein.
The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.
This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT.
Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
2004 Microsoft Corporation. All rights reserved.
Microsoft, Active Directory, Outlook 2003, SharePoint Services, Windows Server 2003 Service Pack 1, Windows are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
Contents
Why Should Organizations Deploy Service Pack 1?
Getting Started with Windows Server 2003 Service Pack 1
Microsoft is committed to creating software solutions that enhance the security, reliability, and productivity of enterprise IT resources. In today's business environment, IT security is paramount-businesses and consumers share an increasing amount of sensitive data and rely upon the communication of those data for work and business. While robust IT security is intrinsically valuable, a well-secured infrastructure can also improve server reliability to meet the ever increasing demands of commerce and industry. Further, the reliability improvements resulting from a properly secured infrastructure adds to administrator productivity. Windows Server 2003 SP1 is a collection of updates and security enhancements to the Windows Server 2003 operating system that meets all three of these needs by addressing the primary challenge in ongoing customer security: update management.
The primary objective of SP1 is to reduce customer pain
centered on server security. Update management-the current, industry-standard
defense against evolving security threats-is too complex and too labor intensive.
Simultaneously, the time between identification and exploitation of security holes is shrinking. While customers had 331 days to implement the update for the Nimda worm, customers had only 25 days to update for DCOM vulnerabilities exploited by the Blaster worm. The current approach often delivers too little security too late for many Windows Server 2003 customers. This situation is simply untenable.
Service Pack 1 aggressively addresses these trends in Windows Server 2003 security. Security enhancements in this service pack use an intuitive, role-based approach to deliver flexibility to customers in terms of time to test and time to deploy new updates. Moreover, Service Pack 1 takes a preemptive approach to security with engineering enhancements such as Windows Firewall. (Formerly the Internet Connection Firewall, Windows Firewall was first introduced in Windows XP Service Pack 2.) Windows Firewall settings can be deployed in enterprises using Active Directory Group Policy.
Service Pack 1 is an augmentation and enhancement to Windows Server 2003. Besides bundling the latest security updates, Service Pack 1 shifts the paradigms underlying the current method of update management and delivers a new, proactive model of security evolution for Windows Server 2003 customers.
Traditionally, service packs were simply a means of distributing product updates. While they may have delivered incremental feature additions, service packs rarely contained significant new functionality; they typically contain updates for system reliability, program compatibility, security, and so forth. While service packs conveniently combined these updates for easy downloading, it was still primarily a consolidation of updates. In addition to updates, Windows Server 2003 Service Pack 1 contains value-added features to increase security and improve functionality.
The goals of Service Pack 1 are to increase the security, reliability, and productivity of Window Server 2003. A key component of achieving these goals hinges upon reducing the attack surface of Windows Server 2003 and bolstering its security. However, plugging old holes and incrementally tuning server performance is no longer enough to meet the challenges of increasingly aggressive attacks. Microsoft has created Service Pack 1 to dramatically change the security equation for Windows Server 2003. In addition to pivotal updates, Service Pack 1 delivers exciting enhancements and dynamic new functionality to Windows Server 2003. Service Pack 1 benefits customers who are currently running Windows Server 2003 and customers who perform new installations of and upgrades to the Windows Server 2003 operating system.
Windows Server 2003 Service Pack 1 can be applied to Windows Server 2003 Standard Edition, Windows Server 2003 Enterprise Edition, Windows Small Business Server 2003, Windows Server 2003 Web Edition, Windows Server 2003 Datacenter Edition, and Windows Server 2003 with the Server Appliance Kit operating systems.
Service Pack 1 provides convenient, comprehensive access to the latest updates, enhancements, and new features for Windows Server 2003. Each of these components allows customers to better leverage the enhanced security, reliability, and performance of Windows Server 2003.
Update management is one of the great challenges of computer security. Despite the challenges of update management, updates will continue to play a vital role in securing enterprise IT until security technology can anticipate every attack strategy and compensate for every vulnerability. While enhancements and new functionality delivered by Service Pack 1 make great strides towards more proactive security, reacting to known threats is still a core mission of Service Pack 1.
Frequent updating is a key to keeping up with exploits as they are discovered. By bundling these updates together in Service Pack 1, Microsoft provides customers, both new and old, with the latest protection for Windows Server 2003.
The updates disseminated by Service Pack 1 cover some of the most basic functionality-and thus remove some of the most important attack points-of Windows Server 2003. These updates include fixes for:
Internet Explorer-Updates to this application include those to prevent unintentional downloads of misrepresented, malicious code and the automatic resizing of browser windows as a ruse to extract sensitive data from employees.
Outlook Express-This update affords users the option of rendering email in plain text rather than HTML. Downloading email as plain text as opposed to HTML provides one more barrier against the spread of malicious code via email.
WebDAV Redirector-By Updating this behind-the-scenes program, customers can access Web-based Distributed Authoring Versioning (WebDAV) servers, such as Windows SharePoint Services and MSN Communities, as if they were standard file servers. Moreover, this update prevents customers' credentials (user name, password) from being transmitted over unencrypted channels during such exchanges.
While updates may be a business necessity, they need not be a business problem. Microsoft addresses update-related server down time with the Hot Patching feature in Service Pack 1. Updates that require restarts are a problem for business-critical servers, and they can pose a challenge to the service level agreements of an IT organization. Hot Patching allows customers to apply updates to drivers, DLLs, APIs, or any non-kernel level component of Windows Server 2003 without restarting the server.
In addition to finding and updating security holes before hackers can exploit them, Service Pack 1 includes improvements to functionality that originally shipped with Windows Server 2003. Such enhancements make a great product better and raise the security, reliability, and productivity of Windows Server 2003. Below are brief descriptions of some of the key enhancements included in Service Pack 1:
Stronger defaults and privilege reduction on services-Services such as RPC and DCOM are integral to Windows Server 2003, but they are also an alluring target for hackers. By requiring greater authentication for RPC and DCOM calls, Service Pack 1 establishes a minimum threshold of security for all applications that use these services, even if they possess little or no security themselves.
Support for "no execute" hardware-Service Pack 1 allows Windows Server 2003 to utilize functionality built in to computing hardware, from companies such as Intel and Advanced Micro Devices, to prevent malicious code from launching attacks from areas of computer memory that should have no code running in it. For both 32-bit and 64-bit systems, this enhancement closes the door on one of the broadest and most exploited avenues of information attack.
Network Access Quarantine Control components included-Windows Server 2003 SP1 now includes the Rqs.exe and Rqc.exe components to make deployment of Network Access Quarantine Control easier. For more information, see Network Access Quarantine Control in Windows Server 2003.
IIS 6.0 metabase auditing-The metabase is the XML-based, hierarchical store of configuration information for Internet Information Services (IIS) 6.0. The ability to audit this store allows network administrators to see which user accessed the metabase in case it becomes corrupted.
Microsoft is taking the opportunity afforded by the release of Service Pack 1 to introduce powerful new functionality to Windows Server 2003.
Windows Firewall-Also released with Windows XP Service Pack 2, Windows Firewall is the successor of the Internet Connection Firewall. Windows Firewall is a host (software) firewall, a firewall around each client and server computer on a customer's network. Unlike Windows XP Service Pack 2, the Windows Firewall is off by default on Server 2003 Service Pack 1, and must be turned on to begin protecting systems. The Windows Firewall is enabled for a brief time during Service Pack 1 clean installs for the duration of the new Post-Setup Security Updates portion of setup.
Post-Setup Security Updates (PSSU)-Servers are vulnerable in the time between initial installation and having the latest security updates applied. To counter this, Windows Server 2003 with Service Pack 1 uses Windows Firewall to block all inbound connections to the server after installation until Windows Update delivers the latest security updates to the new computer. After updating, Windows Firewall is turned off until it is configured for server roles. PSSU also guides users through immediate configuration of Automatic Updates.
Security Configuration Wizard (SCW)-SCW is a wizard that configures server security based upon existing server roles. SCW asks questions about server roles and then stops all services not necessary to perform those roles. SCW will not add roles, but will configure the server around the roles it performs. Like boarding-up unused doors, this new feature helps reduce the attack surface of Windows Server 2003.
Service Pack 1 is a no-cost means for enterprises to enhance Windows Server 2003. Service Pack 1 updates known vulnerabilities in Windows Server 2003 and adds to its capabilities to meet the complementary features to enhance its security, reliability, and performance.
Enhanced security-Service Pack 1 dramatically shrinks the attack surface of Windows Server 2003. Not only does it reactively address known security holes via updates, it sets up customers to proactively face future security threats. By shifting security into a role-based paradigm, Service Pack 1 allows customers to run no more services than they need, eliminating potential toeholds for hackers and malicious code. Moreover, role-based security eases the deployment of future updates, reducing the time it takes for IT professionals to prepare for attempted exploitation of newly discovered vulnerabilities.
Enhanced reliability-Security is at the heart of IT reliability: a system plagued by external attack is by definition not reliable for any who that depend upon it. By updating against past threats and anticipating future threats, Service Pack 1 increases the reliability of Windows Server 2003.
Enhanced productivity-Resources spent dealing with the aftermath of an attack or maintaining cumbersome security arrangements are resources siphoned away from the customer's core business. Service Pack 1 addresses this intersection of security and productivity. By aggressively countering security threats, Service Pack 1 obviates organizations' need to clean up after attacks; by simplifying and rationalizing update management, Service Pack 1 frees up organizations resources from the security front for better use in their core businesses.
Service Pack 1 is an especially attractive incentive for organizations that have not yet adopted Windows Server 2003. Not only is Windows Server 2003 with Service Pack 1 already inoculated with all current updates, it includes new functionality to meet real-world needs discovered since the launch of Windows Server 2003. Service Pack 1 marks a large step in Windows Server 2003's maturity as a powerful tool for businesses.
In general, system requirement for Service Pack 1 are the same as the general Windows Server 2003 system requirements listed below.
|
Windows Server 2003 System Requirements |
||||
|
Requirement |
Standard Edition |
|
Datacenter Edition |
Web Edition |
|
Minimum CPU Speed |
133 MHz |
. 133 MHz for x86-based computers . 733 MHz for Itanium-based computers* |
. 400 MHz for x86-based computers . 733 MHz for Itanium-based computers* |
133 MHz |
|
Recommended CPU Speed |
550 MHz |
733 MHz |
733 MHz |
550 MHz |
|
Minimum RAM |
128 MB |
128 MB |
512 MB |
128 MB |
|
Recommended Minimum RAM |
256 MB |
256 MB |
1 GB |
256 MB |
|
Maximum RAM |
4 GB |
. 32 GB for x86-based computers . 64 GB for Itanium-based computers* |
. 64 GB for x86-based computers . 512 GB for Itanium-based computers* |
2 GB |
|
Multiprocessor Support ** |
Up to 4 |
. Up to 8 |
. Minimum 8-way capable machine required . Maximum 64 |
Up to 2 |
|
Disk Space for Setup |
1.5 GB |
. 1.5 GB for x86-based computers . 2.0 GB for Itanium-based computers* |
. 1.5 GB for x86-based computers . 2.0 GB for Itanium-based computers* |
1.5 GB |
System requirements shown are for prerelease code. Final system requirements are subject to change.
This section provides a walk-through of the screens that appear during the setup of Windows Server 2003 Service Pack 1. Installation of Service Pack 1 is a straight-forward task that requires no pre-configuration of the server operating system.
Information about Service Pack 1 is presented for review prior to installation.
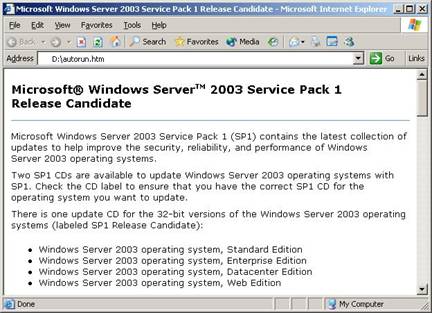
Figure 1. Service Pack 1 download screen
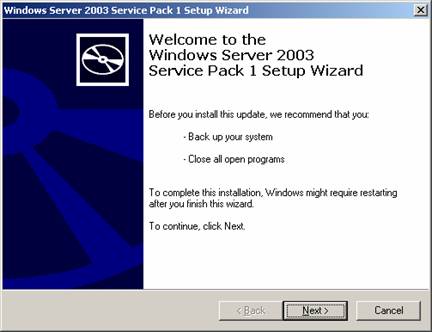
Installation of Service Pack 1 for Windows Server 2003 guides customers through
the installation process with a familiar, easy-to-follow wizard. The following
images show this installation process, as it appears to users.
Figure 2. Service Pack 1 installation: initial screen.
After accepting the license agreement, setup creates a backup of system files so you can uninstall the service pack if necessary.
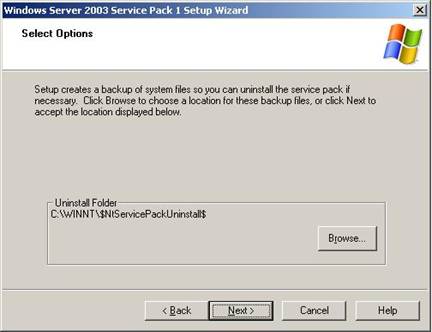
Figure 3. Service Pack 1 installation: backup.
Service Pack 1 Installation Wizard displays its progress through the installation process. At this stage the installation wizard inspects the server configuration and installs files. Restart is required upon completion of installation. The installation wizard concludes by giving customers the option to restart their computer later, if needed.
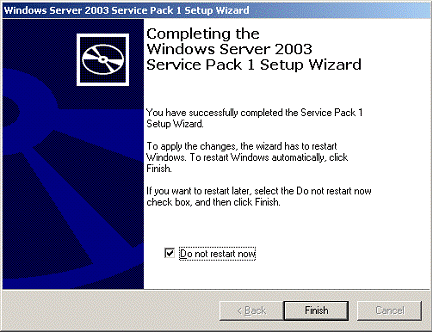
Figure 4. Completing Service Pack 1 installation.
Windows Server 2003 Service Pack 1 is an exciting combination of product updates and new features and functionality. Following is a table summarizing the changes to Windows Server 2003 affected by Service Pack 1. Following the table are two sections discussing the key enhancements and new features of Service Pack 1 in greater technical detail.
Service Pack 1 changes to Windows Server 2003 functionality
|
Change |
Description |
|
Administrative Tools |
The administrative tools are a set of Microsoft Management Console (MMC) snap-ins that customers can use to administer users, computers, services, and other system components on local and remote computers. If Windows Firewall is activated, port 445 must be opened to allow the administrative tools to work as expected for remote computer administration. |
|
Data Execution Prevention |
Service Pack 1 utilizes both built-in hardware capabilities and novel software to prevent malicious code from launch attacks from areas of computer memory that should have no code running in it. (See the Enhancements section below for a detailed description.) |
|
DCOM Security Enhancements |
Service Pack 1 changes COM to provide computer-wide access controls that govern access to all call, activation, or launch requests on the computer. In essence, these access controls are an additional AccessCheck call that is done against a computer-wide access control list (ACL) on each call, activation, or launch of any COM server on the computer. (See the Enhancements section below for a detailed description.) |
|
Download, Attachment, and Authenticode Enhancements |
In Windows Server 2003 with Service Pack 1, the prompts that are used for file downloads, mail attachments, shell process execution, and program installation have been modified to be more consistent and clearer than in previous versions of Windows Server. In addition, the publisher information is shown before a file type that is signable and can potentially harm a customer's machine is opened. (Common examples of signable file types that can potentially harm the user's machine are .exe, .dll, .ocx, .msi, and .cab.) |
|
Filter for Add or Remove Programs |
The filter for Add or Remove Programs provides a means for the user to select whether or not updates, such as security updates downloaded from the Microsoft Web site, are displayed in the Currently installed programs list. |
|
Internet Explorer Add-on Management and Crash Detection |
Internet Explorer Add-on Management allows users to view and control the list of add-ons that can be loaded by Internet Explorer with more detailed control than before. It also shows the presence of some add-ons that were previously not shown and could be very difficult to detect. Internet Explorer Add-on Crash Detection attempts to detect crashes in Internet Explorer that are related to an add-on. When the add-on is successfully identified, this information is presented to the user. The user has the option of disabling add-ons to diagnose crashes and improve the overall stability of Internet Explorer. |
|
Internet Explorer Binary Behaviors Security Setting |
Internet Explorer contains dynamic binary behaviors: components that encapsulate specific functionality for HTML elements to which they were attached. These binary behaviors were not previously controlled by any Internet Explorer security setting, which allowed them to work on Web pages in the Restricted Sites zone. Service Pack 1 has a new Internet Explorer security setting for binary behaviors; this new setting disables binary behaviors in the Restricted Sites zone by default. This new binary behaviors security setting provides a general mitigation to vulnerabilities in Internet Explorer binary behaviors. |
|
Internet Explorer BindToObject Mitigation |
With Service Pack 1, the ActiveX security model is applied in all cases where URL binding is used to instantiate and initialize an object. The ActiveX security model allows controls to be marked as "safe for scripting" and "safe for initialization" and provides users with the ability to block or allow ActiveX controls by security zone, based on those settings. This allows greater flexibility and control of active content in Internet Explorer. |
|
Internet Explorer Feature Control Settings in Group Policy |
Service Pack 1 incorporates the new registry keys and values for Internet Explorer security features, called Feature Control, first introduced with Windows XP Service Pack 2. A modified Inetres.adm file contains the feature control settings as policies. Administrators can manage the feature control policies by using Group Policy objects (GPOs). When Internet Explorer is installed, the default preferences settings for these feature controls are registered on the computer in HKEY_LOCAL_MACHINE. In Group Policy, the Administrator can set them in either HKEY_LOCAL_MACHINE (Computer Configuration) or HKEY_CURRENT_USER (User Configuration). |
|
Internet Explorer Information Bar |
The Internet Explorer Information Bar in Windows Server 2003 Service Pack 1 replaces many of the common dialog boxes that prompted users for information in previous versions and provides a prominent area for displaying information that users may want to view or act upon. Examples of dialog boxes that have been replaced by Information Bar notifications include blocked ActiveX installs, pop-ups, downloads and active content. The Information Bar will provide information similar to the notification area in Microsoft Outlook 2003, which informs users of blocked content. |
|
Internet Explorer Local Machine Zone Lockdown |
When Internet Explorer opens a Web page, it places restrictions on what the page can do, based on the page's Internet Explorer security zone. Pages that are located on the Internet will normally be in the more restrictive Internet security zone (and thus might not be allowed to perform some operations, such as accessing the local hard drive); pages that are located on a customer's corporate network would normally be in the intranet security zone, and have fewer restrictions. With Service Pack 1 Internet Explorer further protects customers by locking down the Local Machine zone by default. Local HTML hosted in other applications will run under the less restrictive settings of the Local Machine zone used in previous version of Internet Explorer unless that application makes use of Local Machine Zone Lockdown. |
|
Internet Explorer MIME Handling Enforcement |
Internet Explorer uses Multipurpose Internet Mail Extensions (MIME) type information to decide how to handle files that have been sent by a Web server. For example, when there is a Hypertext Transfer Protocol (HTTP) request for .jpg files, when they are received, they will generally be displayed to the user in an Internet Explorer window. If Internet Explorer receives an executable file, Internet Explorer generally prompts the user for a decision on how to handle the file. With Service Pack 1 Internet will follow stricter rules than in previous version of Windows Server 2003. These rules are designed to protect users from accidentally downloading or executing a dangerous file due to misleading MIME or file name extension information. |
|
Internet Explorer Network Protocol Lockdown |
Internet Explorer can be configured to lock down HTML content from particular network protocols in additional zones besides the local machine zone. This feature allows an administrator to extend the same restrictions of the Local Machine Zone Lockdown (see above) to apply to any content on any arbitrary protocol in any security zone. Example: An administrator can configure Internet Explorer to lock down HTML content hosted on the Shell: protocol if it is in the Internet zone. Since the Shell: protocol's most common use is for local content and not Internet content, this mitigation can reduce the attack surface of the browser against possible vulnerabilities in protocols less commonly used than HTTP. |
|
Internet Explorer Object Caching |
In Internet Explorer in previous versions of Windows Server 2003, some Web pages could access objects cached from another Web site. With Service Pack 1 a reference to an object is no longer accessible when the user navigates to a new domain. |
|
Internet Explorer Pop-up Blocker |
Pop-up Blocker blocks most unwanted pop-up windows from appearing. Pop-up windows that are opened when the end user clicks a link will not be blocked. End users and IT administrators can let specific domains open programmatic pop-up windows. Developers will be able to use or extend the pop-up functionality in Internet Explorer for applications hosting Internet Explorer. |
|
Internet Explorer Untrusted Publishers Mitigations |
This feature allows the user to block all signed content from a given publisher without showing the Authenticode dialog box to the user while doing so. This prevents code from the blocked publisher from being installed. This feature also blocks installation of code with invalid signatures. |
|
Internet Explorer URL Action Security Settings in Group Policy |
Service Pack 1 incorporates the true policies for the configurable actions in the Internet Explorer Security tab settings first introduced with Windows XP Service Pack 2. These actions can be set to allow less secure behavior within a security zone. In this release, these security settings are managed using the Group Policy Management Console and, if set, can be changed only by a Group Policy object (GPO) or by an administrator. An updated Inetres.adm file contains the same list of URL Action settings as policies that are found in the Internet Explorer user interface as preferences. Administrators can manage the new feature control policies by using Group Policy objects (GPOs). When Internet Explorer is installed, the default HKEY_CURRENT_USER preferences settings for these URL Action settings are registered on the computer as they were in previous versions. The Administrator has to use the Group Policy Management Console (GPMC) snap-in to add URL Actions as policies. |
|
Internet Explorer Using Feature Control Registry Settings with Security Zone Settings |
Feature Control registry settings are provided for Internet Explorer so a specific process can be configured to opt-in to a particular security feature. Once a process has been configured to use a security feature, that feature is running and security zone settings can be applied for more precision. Using security zone settings for a feature provides additional precision in control for security features in Internet Explorer and can help manage application compatibility for organizational intranet applications |
|
Internet Explorer Window Restrictions |
Internet Explorer provides the capability for scripts to programmatically open additional windows of various types, and to resize and reposition existing windows. The Window Restrictions security feature, formerly called UI Spoofing Mitigation, restricts two types of script-initiated windows that have been used by malicious persons to deceive users: pop-up windows (which do not have components such as the address bar, title bar, status bar, and toolbars) and windows that include the title bar and status bar. |
|
Internet Explorer Zone Elevation Blocks |
When Internet Explorer opens a Web page, it puts restrictions on what the page can do based on where that Web page came from: the Internet, a local intranet server, a trusted site, etc. For example, pages on the Internet have stricter security restrictions than pages on a user's local intranet. Web pages on a user's computer are in the Local Machine security zone, where they have the fewest security restrictions. This makes the Local Machine security zone a prime target for malicious users. Zone Elevation Blocks makes it harder to get code to run in this zone. This, coupled with Local Machine Zone Lockdown (see above), makes this zone less vulnerable to malicious users by changing its security settings. |
|
Outlook Express |
Plain Text Mode-This feature provides users with the option to render incoming mail messages in plain text instead of HTML. When Outlook Express is running in plain text mode, the rich edit control is used instead of the MSHTML control, helping avoid some security issues that result from MSHTML's ability to execute malicious code. Limit External HTML Content Downloads-This feature helps users avoid getting repeated spam mailings by preventing users from unknowingly validating their e-mail addresses to spam originators. When the Don't Download External HTML Content feature is enabled, the default behavior of Outlook Express changes so it does not contact the Web server to download external content, which helps prevent the verification of the e-mail address with the spam originator. Attachment Manager API Integration-Outlook Express now integrates a new set of application programming interfaces (APIs), called the Attachment Manager, to check e-mail attachments. This allows applications to eliminate custom code that performs similar safety checks and instead to rely on this centrally managed API set. The use of Attachment Manager provides a consistent user experience across all applications that checks the security of an attachment. |
|
Post-Setup Security Updates |
Post-Setup Security Updates are designed to protect the server from risk of infection between the time the server is first started and the application of the most recent security updates from Windows Update. To protect the server, Windows Firewall is enabled during a new installation of any version of Windows Server 2003 that includes a service pack. Inbound connections to the server are blocked until the administrator has clicked the Finish button on the Post-Setup Security Updates dialog box, allowing the administrator to securely download and install updates from Windows Update. (see below in the New features section for a detailed description) |
|
Resultant Set of Policy |
Group Policy Resultant Set of Policy (RSoP) reports Group Policy settings that are applied to a user or computer. Group Policy Results in Group Policy Management Console (GPMC) requests RSoP data from a target computer and presents this in a report in HTML format. With Service Pack 1, installation of Windows Firewall on a computer prohibits remote access to RSoP data from that target computer. Also, if Windows Firewall is enabled, when GPMC is run for the purpose of using Group Policy Results or Group Policy Modeling to retrieve RSoP data it will be unable to retrieve this data. Windows Firewall exceptions can be used to allow retrieval of data in both of these cases. |
|
RPC Interface Restriction |
Service Pack 1 makes the significant change to the Remote Procedure Call (RPC) service in Windows Server 2003 with the addition of the RestrictRemoteClients registry key. This key enables users to modify the behavior of all RPC interfaces on the system and can be used to eliminate remote anonymous access to RPC interfaces on the system (with some exceptions). Additional changes include the EnableAuthEpResolution registry key and three new interface registration flags. |
|
Security Configuration Wizard |
Security Configuration Wizard (SCW) provides guided attack surface reduction for Windows Server 2003. SCW asks a series of questions to determine the functional requirements of customers' servers. SCW uses a roles-based metaphor driven by an extensible XML knowledge base that defines the services, ports, and other functional requirements for over 50 different server roles, including roles for Windows Server System applications such as Microsoft Exchange Server and SQL Server. Any functionality not by that particular server is then disabled. (See the New features section below for a detailed description.) |
|
Transmission Control Protocol/Internet Protocol (TCP/IP) |
Winsock self-healing- Winsock, the Windows network socket facility for applications, is extensible by a mechanism known as a Layered Service Provider (LSP). Winsock LSPs are available for a wide range of useful purposes, including internet parental controls and Web content filtering. In previous versions of Windows Server 2003, removing a malformed (also known as "buggy") LSP could result in corruption of the Winsock catalog in the registry, potentially resulting in a loss of all network connectivity. Winsock now has the ability to self-heal after a user uninstalls such an LSP. New Winsock Netsh commands- Two new Netsh commands are available in Windows Server 2003 Service Pack 1. netsh winsock reset catalog This command resets the Winsock catalog to the default configuration. This can be useful if a malformed LSP is installed that results in loss of network connectivity. While use of this command can restore network connectivity, it should be used with care because any previously-installed LSPs will need to be re-installed. netsh winsock show catalog This command displays the list of Winsock LSPs that are installed on the computer. SYN attack protection is enabled by default- To mitigate the impact on a host experiencing a SYN attack, TCP/IP minimizes the amount of resources devoted to incomplete TCP connections and reduces the amount of time before abandoning half-open connections. When a SYN attack is detected, TCP/IP in Windows Server 2003 and Windows XP lowers the number of retransmissions of the SYN-ACK segment and does not allocate memory or table entry resources for the connection until the TCP three-way handshake has been completed. New SYN attack notification IP Helper APIs- To allow an application to notify network administrators that a SYN attack is taking place, the IP Helper API supports new SYN attack notification APIs named NotifySecurityHealthChange and CancelSecurityHealthChangeNotify. Smart TCP port allocation- To prevent an application from creating a connection with the same set of socket addresses of a connection that is in a TIME WAIT state, TCP/IP in Windows Server 2003 SP1 has implemented a smart TCP port allocation algorithm. When an application requests any available TCP port, TCP/IP first attempts to find an available port that does not correspond to a connection in the TIME WAIT state. If a port cannot be found, then it picks any available port. This new behavior makes it much more unlikely that an application will be assigned a TCP port that is in the TIME WAIT state when connecting to the same destination. |
|
WebDAVRedirector |
The WebDAV Redirector (DAVRdr) allows computers running Windows Server 2003 to use WebDAV (Web-based Distributed Authoring and Versioning) servers, such as Windows SharePoint Services and MSN Communities, as if they were standard file servers. It consists of a kernel component that connects to a Windows NT remote file system stack, and a user-level component (Web client service) that translates file system requests into WebDAV requests. |
|
Windows Firewall |
Windows Firewall (previously called Internet Connection Firewall) is a software-based, stateful host firewall for Windows Server 2003. Windows Firewall provides protection for computers connected to a network by dropping incoming Internet Protocol version 4 (IPv4) and Internet Protocol version 6 (IPv6) traffic that does not correspond to either traffic sent in response to a request of the computer (solicited traffic) or unsolicited traffic that has been specified as allowed (excepted traffic).. (See the New features section below for a detailed description.) |
|
Windows Media Player |
Windows Media Player 10 is installed as part of Windows Server 2003 Service Pack 1. This version of Windows Media Player includes security fixes and new functionality. |
|
Wireless Networking |
Wireless Provisioning Services (WPS) provides wireless users with a consistent experience and seamless connectivity to public Wi-Fi hotspots through automatic provisioning of the client and seamless roaming. WPS enables Wireless Internet Service Providers (WISPs) to use a standards-based and integrated platform to provide enhanced security to Wi-Fi hotspots, making them easy to use and manage. In addition, WPS enables enterprises to easily provide guest access with enhanced security to private wireless networks. |
Microsoft Windows operating systems built on the Windows NT kernel-including both the Windows XP and Windows Server operating system families-rely upon Remote Procedure Call (RPC) services to run. The Distributed Component Object Model (DCOM) in turn leverages Windows' integral usage of RPC to enable customers to distribute applications across their networks in any manner they desire.
Service Pack 1 improves security around DCOM and RPC. RPC (with DCOM built upon it) is fundamentally a means to remotely call, activate, or launch a program on another computer-naturally a desirable ability for hackers! SP1 defends against this avenue of attack by checking every activation or launch of a program against a computer-wide access control list (ACL). This usage of the computer-wide ACL provides a minimum authorization standard for all program calls on a computer, discriminating between who has and who does not have permission to access a system service.
Many COM applications include some security-specific code (for example, calling CoInitializeSecurity), but use weak settings, often allowing unauthenticated access to the process. There is currently no way for an administrator to override these settings to force stronger security in earlier versions of Windows Server 2003.
COM infrastructure includes the RPCSS, a system service that runs during system startup and always runs after that. It manages activation of COM objects and the running object table and provides helper services to DCOM remoting. It exposes RPC interfaces that can be called remotely. Because some COM servers allow unauthenticated remote access (as explained in the previous section), these interfaces can be called by anyone, including unauthenticated users. As a result, RPCSS can be attacked by malicious users using remote, unauthenticated computers.
In earlier versions of Windows, there was no way for an administrator to understand the exposure level of the COM servers on a computer. An administrator could get an idea of the exposure level by systematically checking the configured security settings for all the registered COM applications on the computer, but given that there are about 150 COM servers in a default installation of Windows, that task was daunting. There was no way to view the settings for a server that incorporates security in the software, short of reviewing the source code for that software.
DCOM computer wide restrictions mitigates these three problems. It also enables an administrator to disable incoming DCOM activation, launch, and calls.
Data execution prevention (DEP) is a set of hardware and software technologies that perform additional checks on memory to help protect against malicious code exploits. Windows Server 2003 Service Pack 1 enforces DEP using both hardware and software.
Hardware-enforced DEP marks all memory locations in a process as non-executable unless the location explicitly contains executable code. There is a class of attacks that attempt to insert and execute code from non-executable memory locations. DEP helps prevent these attacks by intercepting them and raising an exception. Both Advanced Micro DevicesT (AMD) and Intel Corporation have defined and shipped Windows-compatible architectures that are compatible with DEP. Service Pack 1 utilizes the no-execute page-protection (NX) processor feature as defined by AMD or the Execute Disable bit (XD) feature as defined by Intel. (Note: 32-bit processors must be running in Physical Address Extension mode to make use of this function.)
An additional set of DEP security checks have been added to Windows Server 2003 with Service Pack 1. These checks, known as software-enforced DEP, are designed to mitigate exploits of exception handling mechanisms in Windows. Software-enforced DEP runs on any processor that can run Windows Server 2003 with Service Pack 1. By default, software-enforced DEP protects only limited system binaries, regardless of the hardware-enforced DEP capabilities of the processor.
Software-enforced DEP performs additional checks on exception handling mechanisms in Windows. If the program's image files are built with Safe Structured Exception Handling (SafeSEH), software-enforced DEP ensures that before an exception is dispatched, the exception handler is registered in the function table located within the image file. If the program's image files are not built with SafeSEH, software-enforced DEP ensures that before an exception is dispatched, the exception handler is located within a memory region marked as executable.
The primary benefit of DEP is that it helps prevent code execution from data pages such as the default heap, various stacks, and memory pools. In normal operations of the system, code is not typically executed from the default heap and stack. Hardware-enforced DEP detects code that is running from these locations and raises an exception when execution occurs. If the exception is unhandled, the process will be terminated. Execution of code from protected memory in kernel mode results in an error.
Although terminating a process or causing the system to fail with an error do not appear to be ideal experiences, this helps prevent malicious code from executing. Preventing malicious code from executing on the system may prevent damage to a customer's system or propagation of malicious code whose harmful effects could easily exceed those of a terminated process or system error.
DEP can help mitigate a class of security exploits. Specifically, DEP can prevent the exploit in which a virus or other attack has injected a process with additional code and then attempts to execute the injected code. On a system with DEP, execution of the injected code would result in an exception. Software-enforced DEP can help mitigate exploits of exception--handling mechanisms within Windows.
A secondary benefit of DEP relates to good engineering and best practices for application and driver developers. DEP forces developers to avoid executing code out of data pages without explicitly marking the pages as executable.
Windows Firewall is a software-based, stateful host firewall for Microsoft Windows XP Service Pack 2 and Microsoft Windows ServerT 2003 Service Pack 1. Windows Firewall provides additional protection for computers that are connected to a network by dropping unsolicited incoming IPv4 and IPv6 traffic that does not correspond to an enabled exception.
Configuration options include:
An additional operating mode: On, but no exceptions are allowed
Enabling static exceptions for ports
Enabling exceptions for programs (applications and services)
Enabling specific types of ICMP traffic
Logging dropped packets and successful connections to a log file
Windows Firewall is off by default when Windows Server 2003 with Service Pack 1 is installed, except when the Post-Setup Security Updates portion of setup is running. Having Windows Firewall on during the initial installation affords computers more protection from many network-based attacks while they are being set up and configured. After installation, the recommendation is to enable Windows Firewall with the appropriate exceptions for the roles that the server is playing as configured through the Security Configuration Wizard. For example, if Windows Firewall had been enabled, the recent MSBlaster attack would have been greatly reduced in impact, regardless of whether the computers had the current updates installed.
The table below summarizes the features and enhancements in Windows Firewall.
Windows Firewall features and enhancements
|
Feature |
Description |
|
Boot-time security |
In earlier versions of Windows, there was a period of time between when the network stack loaded and when Internet Connection Firewall provided protection. This resulted in the ability for a packet to be received and delivered to a service without Internet Connection Firewall providing filtering, potentially exposing the computer to vulnerabilities. This was due to the Internet Connection Firewall driver not starting to filter packets until the firewall user-mode service was loaded and had applied appropriate policy settings. The Internet Connection Firewall service has a number of dependencies, which causes the service to wait until those dependencies are cleared before it pushes the policy down to the driver. This time period is based upon the speed of the computer. In Windows Server 2003 Service Pack 1, the IPv4 and IPv6 firewall drivers have a static rule to perform stateful filtering. This static rule is called a boot-time policy. This allows the computer to perform basic networking tasks such as using DHCP to obtain an address configuration and DNS and associated protocols to communicate with a domain controller to obtain policy settings. After the Windows Firewall service is running, it loads and applies the run-time policy settings and removes the boot-time filters. The boot-time policy cannot be configured. Expanding the protection of the host firewall to boot-time makes server computers vulnerable to fewer attacks during startup. |
|
Global configuration |
Another feature of Windows Firewall is its allowance for global configuration. In earlier versions of Windows, Internet Connection Firewall was configured on a per-interface basis. This meant that each network connection had its own set of firewall settings, for example, one set of settings for wireless and another set of settings for Ethernet. This made it difficult to synchronize settings between connections. Additionally, new connections would not have any of the configuration changes that had been applied to the existing connections. Non-standard network connections, such as those created by proprietary dialers (for instance, ISP-configured dial-up networking connections) could not be protected. With global configuration, whenever a configuration change occurs, it automatically applies to all network connections in the Network Connections folder, including any non-Microsoft dialers. When new connections are created, the configuration is applied to them as well. Configuration can still be performed on a per-interface basis. Non-standard network connections will only have global configuration. Configuration changes also apply to both IPv4 and IPv6. Having global configuration makes it easier for users to manage their firewall settings across all network connections and enables configuration through Group Policy. It also allows you to configure program exceptions to work on any connection with a single configuration option. |
|
Audit logging |
Audit logging enables customers to track changes made to Windows Firewall settings and to see which applications and services asked the customer's computer to listen on a port. After audit logging is enabled, audit events will be logged in the security event log. Audit logging can be enabled on client computers running Windows XP Service Pack 2 and servers running Windows Server 2003 Service Pack 1. Auditing the activity of Windows Firewall is part of a defense-in-depth strategy that allows customers to quickly react to attacks on their systems. |
|
Scope restrictions for excepted traffic |
For Internet Connection Firewall, when you configure a port exception, it is open with a global scope - incoming traffic can come from any network location, such as a local network or the Internet. With Windows Firewall, you can also configure port and program-based exceptions to only receive network traffic with a source address that is directly reachable based on the contents of the IPv4 and IPv6 routing tables (the My network (subnet) only scope), or from specific IPv4 addresses and address ranges (the Custom scope). When the file sharing ports are opened with the NetShare application programming interface (API), with the Network Setup Wizard, or through the Windows Firewall user interface, the directly reachable scope restriction is applied. For computers in a workgroup, some ports are restricted to directly reachable addresses by default. These ports are those needed for file and printer sharing and the Universal Plug and Play (UPnPT) framework. Additionally, when these ports are opened for directly reachable addresses on an Internet Connection Sharing (ICS) host, the ports will not be opened on the ICS public interface. If a customer opens these ports with the global scope, they will be opened on the ICS public interface, which is not recommended. Some applications only need to communicate with other hosts on the local network and not hosts on the Internet. Allowing a port to receive traffic from only directly reachable addresses restricts the scope of who can access a port. This mitigates attacks that occur because ports are open to computers that connect from any location. |
|
Command-line support |
Windows Server 2003 Service Pack 1 includes a Netsh Windows Firewall helper so that you can fully configure Windows Firewall using Netsh commands at a command line, including: Configure the default state of Windows Firewall (Off, On, On with no exceptions). Configure which exceptions should be enabled, including the scope of each exception (global, directly reachable addresses, specific IPv4 addresses or address ranges) and whether exceptions are enabled on all interfaces or per-interface. Configure the logging options. Configure the Internet Control Message Protocol (ICMP) handling options. Add or remove exceptions from the exceptions list. Providing a command-line interface provides administrators with a method to configure Windows Firewall without going through the graphical user interface. The command-line interface can be used in scripts. |
|
"On with no exceptions" operational mode |
Windows Firewall can be configured for exceptions to allow specific types of unsolicited incoming traffic during normal use. Typically, this is because key scenarios, like file and printer sharing, must be enabled. If a security issue is discovered in one or more of the listening services or applications that are running on the computer, it may be necessary for the computer to switch into a client-only mode, which is called "On with no exceptions." Switching into this client-only mode configures Windows Firewall to drop all unsolicited inbound traffic, regardless of the configured and enabled exceptions, without having to reconfigure the firewall. When in this mode, all static ports are closed and any existing connections are dropped. Any API call to Windows Firewall to open up a static port is allowed and the requested firewall configuration is stored, but it is not applied until the operational mode switches back to normal operation. All listen requests by applications are also ignored. Viruses, worms, and attackers look for services to exploit. When in this operational mode, Windows Firewall helps to prevent these types of attacks from succeeding. |
|
Program-based exceptions |
Some applications act as both network clients and servers. When they act as servers, they must allow unsolicited inbound traffic to come in, because they do not know in advance who the peer will be. In earlier versions of Windows, an application needed to call the firewall APIs to enable the necessary listening ports to be open. This proved difficult in peer-to-peer situations when the port was not known in advance. It was up to the application to close the port again after communication was completed. Without this, there would be unnecessary holes in the firewall if the application terminated unexpectedly. Additionally, these ports could be opened only if applications were running in the security context of a local administrator. This violated the principle of least privilege by requiring applications to run in an administrative context. In Windows Server 2003 with Service Pack 1, a program (an application or a service) that needs to listen to the network can be added to the Windows Firewall exceptions list. If a program is on the Windows Firewall exceptions list, Windows opens and closes the necessary listening ports automatically, regardless of the application's security context. Programs that work with stateful filtering do not need to be placed on the Windows Firewall exceptions list. Only administrators can add a program to the Windows Firewall exceptions list. When a program is on the Windows Firewall exceptions list, only the necessary ports are opened, and they are opened only for the duration that the program is listening on those ports. A program cannot open a port that it is not using, which might deliberately or inadvertently expose another application or service to network traffic from that port. This also allows programs that are listening to the network to run using an account with lesser privileges. In previous versions of Windows, the user had to run these programs with Administrator rights. |
|
Multiple profiles |
Multiple profile support in Windows Firewall allows customers to create two sets of firewall policy settings: one for when the computer is connected to a managed organization network (known as the Domain profile) and one for when the computer is not (known as the Standard profile). Customers can specify policy settings that are less strict when the computer is connected to a managed organization network to enable line-of-business applications to work. Customers may also have more restrictive security policy settings that will be enforced when the computer leaves the corporate network, which helps to protect mobile users. For a mobile computer, it is desirable to have more than one firewall configuration. Often, a configuration that is safe on a private network is likely to be susceptible to attack on the Internet. Therefore, being able to have ports opened on the private network and not on other networks is critical to ensuring that only the necessary ports are exposed at any given time. |
|
RPC support for System Services |
In earlier versions of Windows, Internet Connection Firewall blocked remote procedure call (RPC) communication. While Internet Connection Firewall could be configured to allow network traffic to the RPC Endpoint Mapper, the port that RPC used was unknown and the application would still fail. Many enterprise applications and components fail if RPC is not allowed to communicate over the network. Some examples include, but are not limited to, the following: Remote administration, such as the Computer Management feature and the Select User, Computers, and Groups dialog box, which is used by many applications Remote Windows Management Instrumentation (WMI) configuration Scripts that manage remote clients and servers RPC opens several ports and then exposes many different servers on those ports. Because so many RPC servers are included with Windows XP and Windows Server 2003, Windows Firewall takes a different approach for system services using RPC. Windows Firewall will accept this claim only if the caller is running in the local system, network service, or local service security context. To enable remote administration scenarios, many enterprise-wide deployments require that the system services that use RPC work with Windows Firewall by default. By using more precision, customers can control which RPC services are exposed to the network. |
|
Restore defaults |
Previously, there was no way for a user to reset the configuration of the Internet Connection Firewall. Over time, Windows Firewall might be configured with multiple exceptions, making it difficult for the user to easily and quickly go back to a default configuration. The restore defaults option enables the user to restore Windows Firewall settings to their original defaults. In addition, the Windows Firewall defaults can be modified by original equipment manufacturers (OEMs) and businesses to provide custom default configuration options. |
|
Unattended setup support |
In earlier versions of Windows, it was not possible to configure Internet Connection Firewall during installation. This made it difficult for OEMs and businesses to preconfigure Internet Connection Firewall before distributing the computer to their end users. In Windows Server 2003 with Service Pack 1, customers can configure the following options of Windows Firewall through unattended setup: Operational mode Program-based exceptions Port-based exceptions ICMP options Logging options A method to preconfigure Windows Firewall allows Windows resellers and large enterprises more flexibility and customization options for Windows Firewall. |
|
Enhanced multicast and broadcast support |
Multicast and broadcast network traffic differs from unicast traffic because the response comes from an unknown host. As such, stateful filtering prevents the response from being accepted. This stops a number of scenarios from working, ranging from streaming media to discovery. To enable these scenarios, Windows Firewall will allow a unicast response for three seconds from any source address on the same port from which the multicast or broadcast traffic originated. This support allows applications and services that use multicast and broadcast for communicating to work without either the user or application/service to alter the firewall policy. This is important for things like NETBIOS over TCP/IP, so that sensitive ports such as port 135 are not exposed. This option can be configured through the Windows Firewall Group Policy settings. |
|
IPv6 support |
In earlier versions of Windows, Internet Connection Firewall only filtered IPv4 traffic. IPv6 support is included with the Windows Firewall and automatically enabled on all IPv6 connections. Both IPv4 and IPv6 share the same settings for excepted traffic. For example, if you except file and print sharing traffic, then both IPv4 and IPv6-based unsolicited incoming file and print sharing traffic is allowed. Windows Firewall does not support the configuration of specific IPv6 addresses or address ranges when configuring a custom scope for an exception. |
|
Updated user interface |
The Windows Firewall user interface is updated in Windows Server 2003 Service Pack 1 to accommodate the new configuration options. It provides the user with the ability to change the operational states, program and port-based exception, and advanced settings such as logging and ICMP options. The primary entry to the Windows Firewall user interface is now the Windows Firewall component of Control Panel. A link from the old location is still provided. Additionally, Windows Server 2003 Service Pack 1 includes a link from the Network Connections folder. |
|
New Group Policy Support |
In earlier versions of Windows, Internet Connection Firewall had a single Group Policy Object (GPO): Prohibit use of Internet Connection Firewall on your DNS domain network. With Windows Server 2003 Service Pack 1, most configuration options available through the Windows Firewall component of Control Panel can be set through new Windows Firewall Group Policy settings located at Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows Firewall. Examples of the new configuration options available include: Define program exceptions Allow local program exceptions Define port exceptions Allow local port exceptions Allow ICMP exceptions Prohibit notifications Allow file and printer sharing exception Allow logging Each of these objects can be set for both a domain profile (for when the computer is connected to a managed organization network) and a standard profile (for when the computer is not connected to a managed organization network). |
For more information about Windows Firewall, see the following resources:
Deploying Windows Firewall Settings for Microsoft Windows XP with Service Pack 2
Manually Configuring Windows Firewall in Windows XP Service Pack 2
Troubleshooting Windows Firewall in Microsoft Windows XP Service Pack 2
Although these resources describe Windows Firewall in Windows XP Service Pack 2, most of the same information applies to Windows Firewall in Windows Server 2003 SP1.
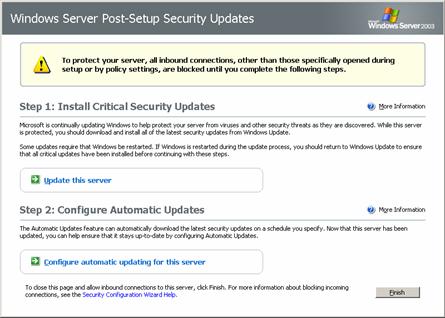
Post-Setup Security Updates is designed to protect the server from risk of infection between the time the server is first started and the application of the most recent security updates from Windows Update. To protect the server, Windows Firewall is enabled during a new installation of any version of Windows Server 2003 that includes a service pack. If Windows Firewall is enabled and the administrator did not explicitly enable it using an unattended-setup script or Group Policy, Post-Setup Security Updates opens the first time an administrator logs on. Inbound connections to the server are blocked until the administrator has clicked the Finish button on the Post-Setup Security Updates dialog box; this allows the administrator to securely download and install updates from Windows Update. If the administrator set exceptions to the firewall through Group Policy or by enabling Remote Desktop during installation, inbound connections assigned to these exceptions remain open.
Post-Setup Security Updates is not available from the Start menu; PSSU applies to full installations of Windows Server 2003 that includes a service pack (such as a slip-stream version of Windows Server 2003 with Service Pack 1). PSSU does not appear when the server is being upgraded from the following operating systems:
Windows 2000 to Windows Server 2003 with Service Pack 1
Windows Server 2003 to Windows Server 2003 with Service Pack 1
It will, however, be displayed when the server is being upgrade from Windows NT
4.0 to Windows Server 2003 with Service Pack 1. In addition, PSSU does not
apply to installations of Windows Server 2003 that use either an unattended
setup script or an application of a Group Policy that enables or disables
Windows Firewall.
Figure 5. Post-Setup Security Updates: user interface.
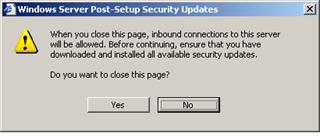
Figure 6. Post-Setup Security Updates: closing warning.
IT security is an ongoing, organic struggle. Microsoft may have released security updates that mitigate virus threats since the release of the operating system files being installed. If the new server is connected to the network and a firewall is not enabled, the server may be infected with a virus before the security updates can be downloaded and installed. Post-Setup Security Updates uses the Windows Firewall to mitigate this risk.
Security Configuration Wizard (SCW) provides guided attack surface reduction for customers' servers. SCW asks a series of questions to determine the functional requirements of-in short, the role played by-customers' servers. SCW uses a roles-based metaphor driven by an extensible XML knowledge base that defines the services, ports, and other functional requirements for over 50 different server roles including roles for Windows Server System applications such as Microsoft Exchange Server and SQL Server. Any functionality that is not required by the roles the server is performing will be disabled.
SCW uses this extensible XML knowledge base to perform role discovery, solicit user input, and author security policies that disable services, block ports, modify registry values, and configure audit settings. Even ports that are left open can be restricted to specific populations or secured using Internet Protocol security (IPSec). SCW also allows customers to roll back previously applied policy settings and includes a command line tool with which administrators use administrative scripts and other administrative utilities to apply a security configuration and compliance analysis to groups of servers in customers' organizations. SCW also integrates with Active Directory to support deployment of SCW-generated policy settings through Group Policy.
SCW security coverage
SCW allows users to easily:
Disable unnecessary services
Disable unnecessary IIS Web extensions
Block unused ports, including support for multi-homed scenarios
Secure ports that are left open using IPSec
Reduce protocol exposure for Lightweight Directory Access Protocol (LDAP), LAN Manager, and server message block (SMB)
Configure audit settings with a high signal-to-noise ratio
Import Windows security templates for coverage of settings that are not configured by the wizard
SCW operational features
In addition to roles-based, guided security policy authoring, SCW also supports:
Rollback-Enables customers to return their server to the state it was in before they applied the SCW security policy, which can be useful when applied policies disrupt service expectations
Analysis-Enables customers to check that servers are in compliance with expected policies
Remote access-Supports remote access for configuration and analysis operations
Command line support-Enables remote configuration and analysis of groups of servers
Active Directory integration-Supports deploying SCW policies using Group Policy
Editing-Enables modification of a security policy created using SCW necessary, such as when server roles are redefined
XSL views-Provides the ability to view the data stored in the knowledge base, policies, and analysis results XML files
Attack surface reduction is a fundamental security best practice, yet it is often difficult for server administrators to find the time to properly secure, test, and deploy a Windows server without breaking required functionality, which can lead to vulnerable servers within an organization. SCW automates the lockdown process and is fully tested and supported by Microsoft. Reducing the attack surface of Windows servers can minimize the number of servers that need to be immediately updateed when a vulnerability is exploited, as a given vulnerability will not necessarily be present in all configurations.
Currently, Windows administrators typically define security policies using the Security Template snap-in on their own, in conjunction with documented guidance, or with existing security templates designed for specific scenarios. In contrast, SCW is an authoring tool that allows customers to create a custom security policy by answering a series of questions. For settings that are not configured by the wizard, SCW allows the administrator to import existing security templates.
SCW user interface
The SCW is not installed by default. It appears in Windows Components for easy installation. Once installed, the SCW can be accessed through the server Administrative Tools from the Start menu.
The SCW uses a standard Microsoft wizard interface to provide customers with a consistent, intuitive experience. The SCW uses this same wizard interface to walk customers through creating new security policies or editing existing policies. The SCW also allows customers to apply existing policies repeatedly to other servers, as well as undo a previously applied policy.
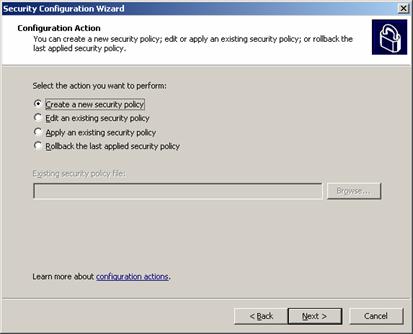
Figure 7. Security Configuration Wizard: select a course of action.
Customers who create a new policy start by selecting a
server to use as a baseline on which
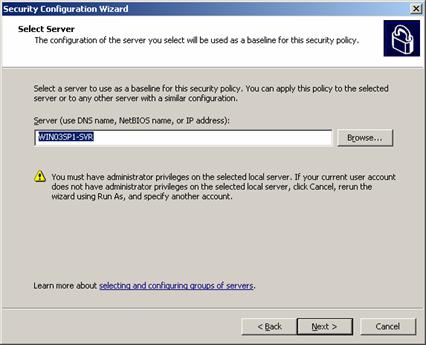
to base their new policy. Once created, the security policy can be applied to
other similarly configured servers saving administrator time.
Figure 8. Security Configuration Wizard: select baseline.
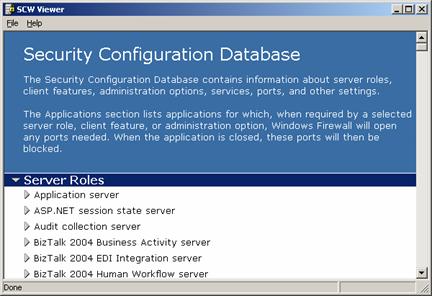
The SCW creates the Security Configuration Database to store information about
the customer policy settings. Once SCW compiles the Security Configuration
Database, the customer can view the database entries.
Figure 9. Security Configuration Wizard: Security Configuration Database.
The SCW creates security policies based on operational
roles-what the customer expects a particular server to do. In similar fashion,
customers also indicate the client roles they expect a particular server to
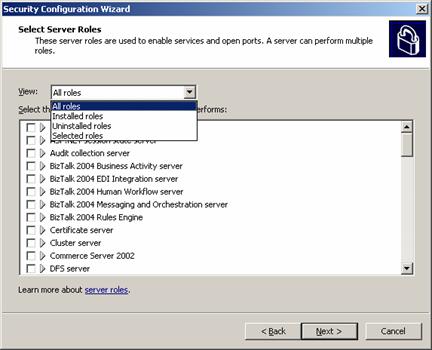
perform. Customers also customize audit policy and registry settings.
Figure 10. Security Configuration Wizard: select server roles.
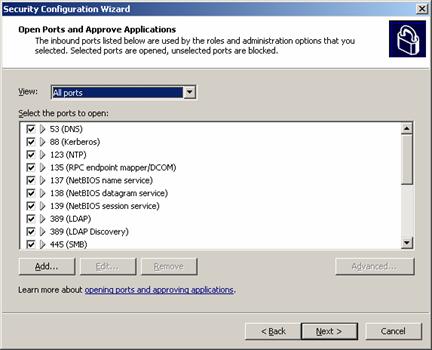
SCW guides customers through handling services unspecified in the wizard,
additional administration tasks handled by the server and the handling of
ports. Customers explicitly select which network ports to keep open and to
close.
Figure 11. Security Configuration Wizard: open ports.
Windows Server 2003 Service Pack 1 is another deliverable on Microsoft's Trustworthy Computing initiative, and it illustrates Microsoft's commitment to continually creating software products with enhanced security, increased reliability and simplified administration. Service Pack 1 delivers the cumulative system updates in one simple package and it introduces numerous refinements and new functionality including Windows Firewall, Post Setup Security Updates, and the Security Configuration Wizard. Customers performing new installations and those with existing deployments of Windows Server 2003 will benefit from these new features. Deploying Service Pack 1 will help enterprises across all industries and segments enhance security and simplify administration through guided attack surface reduction.
See the following resources for further information:
Supporting information also can be found for:
Microsoft .NET at https://www.microsoft.com/net
Windows XP Professional Operating System at https://www.microsoft.com/windowsxp/pro
Microsoft .NET Enterprise Servers at https://www.microsoft.com/servers
MSDN at https://www.microsoft.com/msdn
TechNet at www.microsoft.com/technet
For the latest information about Windows Server 2003, see
the Windows Server 2003
Web site at https://www.microsoft.com/windowsserver2003. Among the resources on the site are numerous technical articles describing
technologies and features in Windows Server 2003. Link directly to the
Technical Overviews page at https://www.microsoft.com/windowsserver2003/techinfo/overview.
Among the resources on the site are numerous technical articles describing
technologies and features in Windows Server 2003. Link directly to the
Technical Overviews page at https://www.microsoft.com/windowsserver2003/techinfo/overview.

|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 2222
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved