| CATEGORII DOCUMENTE |
| Bulgara | Ceha slovaca | Croata | Engleza | Estona | Finlandeza | Franceza |
| Germana | Italiana | Letona | Lituaniana | Maghiara | Olandeza | Poloneza |
| Sarba | Slovena | Spaniola | Suedeza | Turca | Ucraineana |
Theories and methods of Code-caves
Intro
Since many has read my tutorial on basic memory hacking and got stuck on the creation of code-caves, Ive decided to make a short follow-up on code-cave techniques where Ill explain the WHYs and the HOWs.
Note: In order to fully understand this tutorial it is suggested that you read my previous tutorial on basic memory hacking.
Index:
1. In theory
1.1 RAM, the temporary buffer
1.2 Code-caves in general
2. The methods
2.1 Tools:
2.2 Changing values
2.2.1 Changing values theory
2.2.2 Changing values method
3. Problems with your code-cave?
4. Other tutorials by Faldo
1. In theory
1.1 RAM, the temporary buffer
Before youll be able to understand code-caves youll need to understand how your RAM (Random Access Memory) works.
Everything running on a computer (even the operative system) uses your RAM as a temporary buffer to store information. This information is then either forwarded to be stored on a drive unit (hard drive, CD/DVD-burner, floppy), or it will remain in the RAM as long as the process is running.
Whenever a program runs, it either uses your hardware memory modules or a page-file created by windows (virtual memory). In any case, the program 'injects' code into the memory to be processed (read from and written to) since the program itself is already compiled* and cannot change.
The manner of which the program reads and writes code in the memory is fairly simple. Think of it as a list where numbers (hexadecimal addresses) defines the location of the rows. When you start a program, it injects (writes) code into a certain number of rows and then executes one predefined row called entry point. Once the entry point is executed, the program reads the following addresses in chronicle order.
*Compiled: A process where sourcecode is gathered by a compiler program and produces an executable file (.exe in windows).
1.2 Code-caves in general
A code-cave is a name designated to a method where you assemble (write to) an unused portion of your memory in order to change the behavior of the original operations.
A code-cave normally consists of 2 parts:
- The Cave, located at a free portion of your memory. The cave itself consists of a copy of the original code, the changes you wish to make to the original code and a jump back to the original code.
- The Jump-gate, located in the original code. You can compare a jump-gate with a crossroad. Instead of letting traffic (dataflow) use the highway, you put up a roadblock (the jump-gate), diverting traffic to a road you control (whatever changes you wish).
1.3 Why use a code-cave?
There are many reasons why you might need a code-cave. In the methods section of this tutorial, Ive chosen to explain some areas of usage:
- Changing values
- Changing jumps or references
- Adding or subtracting operations
2. The methods
2.1 Tools
To be able to use and follow the methods of this tutorial you will need no knowledge of any programming language, however, if you know the basics of ASM you will probably understand it the first time you read it.
The only tool you will need is Ollydbg 1.10 (search for it on google).
2.2 Changing values
2.2.1 Changing values theory
Since this tutorial will only cover code-caves, you should already know how to gather the right addresses in T-search.
The effects you could get by changing values are almost unlimited since many functions in a program rely on values.
Example: Money, health or gun damage value in a game,
2.2.2 Changing values method
From the list, select the program you want to make a code-cave in and click Attach.
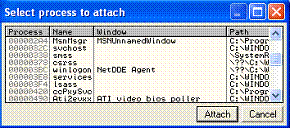
Enter the address you are going to change click OK.
Lets use 0053E58E as an example and call it Moneyaddress.

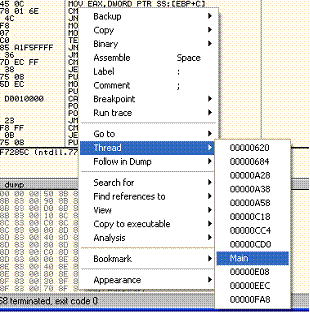
Ollydbg will go to the address you entered and select it.
![]()
What we need to do, is create an operation telling the game to change the value and keep this operation static. If wed destroy the current operation and enter our own modification, the game will most likely crash. The better way to do this is by inserting another address containing our modification.
We could insert our modification at the line coming after the moneyaddress but that would destroy the TEST AL,AL operation and still crash the game.
No, this is a case where we need a code-cave to solve our problem. By copying the relevant addresses to a free portion of the memory we can insert an operation between the MOV operation and the TEST operation, without destroying any lines.
So even if the game gets the value of money from the DMA, we will insert a static address containing another value which will overwrite the previous value.
*DMA: Read Theories and methods of memory hacking-tutorial to understand DMA addresses better.
examples of other MOVs
2.4 Finding the right address
2.4.1 Minimap-hack theory
3. Problems with your code-cave?
4. Other trainers by Faldo
-Theories and methods of memory hacking (https://www.mpcforum.com/showthread.php?t=61024)
Outro:
I know this tutorial contains a lot of information; some may be harder to understand than other. A good trick is to always keep in mind what you are trying to accomplish. If you want to become a good hacker, my suggestion is you learn ASM and Visual Basic that are not very hard to learn.
Many thanx to:
Captain Cox, Max Powers and MPC.de
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1104
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved