| CATEGORII DOCUMENTE |
| Asp | Autocad | C | Dot net | Excel | Fox pro | Html | Java |
| Linux | Mathcad | Photoshop | Php | Sql | Visual studio | Windows | Xml |
You are the administrator for your Windows 2000 domain. You currently have three Windows Internet Name Service (WINS) servers configured for replication. Your network is connected to the Internet by a T1 line and is protected by a firewall.
On your WINS servers, you change the default system settings for dynamic port allocation to a fixed port by editing the HKEY_LOCAL_MACHINESoftwareMicrosoftRPCInternet registry key.
What does this do?
a. Allows you to replicate through the firewall
b. Allows you to deploy WINS through the firewall
c. Allows you to use the WINS servers for NetBIOS name resolution through the firewall
d. Allows you to remotely administer the WINS replication servers through the firewall
You are the administrator for your company's Windows 2000 domain. You have a Windows 2000 Server computer that is your Domain Name System (DNS) server.
You have configured the DNS server to create a log file.
Where is this file located by default?
a. In the %SystemRoot% folder
b. In the %SystemRoot%System32 folder
c. In the %SystemRoot%System32dns folder
d. In the %SystemRoot%System32dnslog folder
You administer your company's Windows 2000 network. You are configuring your Windows 2000 network for dial-up access. The users need to access computers from home.
To increase security, your company issues smart cards to all users who dial in. You need to configure the Routing and Remote Access server.
What should you do? (Choose two.)
a. Select Extensible Authentication Protocol (EAP)
b. Select Microsoft Challenge Handshake Authentication Protocol version 1 or 2 (MS-CHAP v1 or 2)
c. Install computer certificates on the Routing and Remote Access server
d. Install smart card logon certificates on the Routing and Remote Access server
e. Install computer certificates on the dial-up access client computers
You are the administrator for a company's Windows 2000 network. You are planning to implement a new group of Windows 2000 Professional client computers on the network. You add a second adapter card to support the new group of client computers.
While testing the new adapter card, you discover that the adapter card and the driver for the card are configured incorrectly.
Which type of problem did you most likely encounter to come to this conclusion?
a. The new client group could not open the router ports
b. The server could not connect to the existing client group
c. The existing client group could not connect to the new client group
d. The server could not enumerate the Remote Access Connection Manager ports
You administer your company's Windows 2000 network. Your network uses TCP/IP exclusively and is not connected to the Internet. You use the 190.30.0.0 address range. You want to improve performance and accommodate network growth by developing a plan to segregate portions of the network.
The initial plan for your network is 20 subnets with 250 hosts per subnet. The projected growth of the network is 60 subnets with 750 hosts per subnet.
Which subnet mask should you use?
a.
b.
c.
d.
You administer a Windows 2000 Server network that contains a Routing and Remote Access server. You want to remotely monitor a Windows 2000 server from within the routing IP context. The server has an IP address of 160.20.22.4.
What can you use to accomplish this task?
a. Nbstat
b. Netsh
c. Netstat
d. Arp
You are the administrator for your company's Windows 2000 network. Your company has three offices: on in Dallas,
TX, one in Houston, TX, and one in Galveston, TX.
You have implemented WINS replication between the WINS
servers. You view the WINS database on
the WINS server in
Which records will be replicated to the WINS server in
a. All the records, regardless of their state
b. Only records in the active state
c. Both the records in the active state and the records in the released state
d. Both the records in the active state and the records in the tombstoned state
e. Both the records in the released state and the records in the tombstoned state
You are the administrator for your company's Windows 2000 domain. The domain consists of 5 Windows 2000 Server computers and 50 Windows 2000 Professional client computers.
The network currently has a single public IP address. You install Network Address Translation (NAT) on one of your Windows 2000 Server computers. From the properties page of the Internet interface, you ensure the Translate TCP/UDP headers option is enabled.
What does enabling this option say about your network?
a. Your network uses DHCP
b. Your network has a single public IP address
c. Your network must share an Internet connection
d. Your network must use only one public interface
You are the administrator for your company's Windows 2000 network. The network contains a Windows 2000 Server computer, named Dimsvr, configured as the network's Enterprise Certificate Authority (CA). You decide to configure another Windows 2000 Server computer, named Dimenrl, to host the Web Enrollment Support pages.
You complete the configuration for Dimenrl, and you want to test the server from a client computer named Dimcl1. You open the client's Web browser to test the Web Enrollment support pages.
Which URL will the browser open?
a. https://Dimsvr/certsrv
b. https://Dimcl1/certsrv
c. https://Dimenrl/certsrv
d. https://Dimsvr/webenroll
You are the administrator for a Windows 2000 Server network. You have a Dynamic Host Configuration Protocol (DHCP) Server which is configured to give DHCP clients all appropriate TCP/IP settings. You also have a Domain Name System (DNS) / Windows Internet Name Service (WINS) server. You set up a Windows 2000 Server computer to be the dial-up connection server and want to configure the security for the dial-up connections. You want to accomplish the following goals:
Require the entry of a password upon connection.
Use the Windows logon and password for authentication.
Require the use of data encryption.
Automatically run a script named logon.scp upon connection.
You perform the following actions:
From the dial-up connection properties on the Security tab in the Security options section, select Typical (recommended settings) radio button.
For the Validate my identity as follows box, select Allow unsecured password.
Check the Automatically use my Windows logon name and password (and domain if any) box.
Check the Require data encryption (disconnect if none) box.
In the Interactive logon scripting section, check the Run script box and type in filename logon.scp.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Require the entry of a password upon connection
b. Use the Windows logon and password for authentication
c. Require the use of data encryption
d. Automatically run a script named logon.scp upon connection
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your primary Windows Internet Name Service (WINS) server. Another Windows 2000 Server computer is your secondary WINS server. You have 4000 clients that use the WINS servers for NetBIOS name resolution.
You add a Windows 2000 Professional computer to your network and share several resources from it. When other clients attempt to contact this new computer, they are unsuccessful. You are concerned that the new computer is not configured to use WINS properly.
Which command could you run to check this?
a. netstat -e
b. netstat -s
c. netstat -r
d. netdiag /test:WINS
You are the administrator for your company's Windows 2000 Server
network. You company has a main office
in
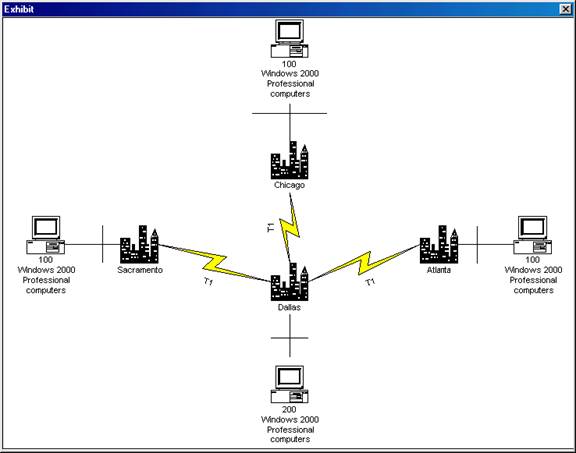
The routers between the offices supports the forwarding of BOOTP messages. At each branch office, you have a local user who is responsible for all administrative duties. Currently the local administrator is responsible for configuring the TCP/IP settings for all the Windows 2000 Professional computers at his/her local branch.
You have been experiencing network communication problems which were the direct result of configuration errors. You want to prevent this from happening again.
What should you do? (Choose two.)
a.
Install and configure a Dynamic Host
Configuration Protocol (DHCP) Server in
b. Install and configure a Windows Internet Name Service (WINS) Server in
c.
Install and configure a Domain Name
System (DNS) Server in
d. On each Windows 2000 Professional computer, change the TCP/IP properties to Obtain an IP address automatically.
e. On each Windows 2000 Professional computer, change the TCP/IP properties to Obtain an IP address automatically.
f. On each Windows 2000 Professional computer, change the TCP/IP properties to Obtain DNS server address automatically.
You are the administrator for your company's Windows 2000 domain. You have a Windows 2000 Server computer that is your Domain Name System (DNS) server, named DNS1. You add a second DNS server, named DNS2 to your domain.
A client computer is having trouble contacting the second DNS server. You suspect that it is because it has an old negative response for the host name in its cache.
What could you use to remove the negative response? (Choose two.)
a. At the client computer, run the nslookup command
b. At the client computer, run the ipconfig /flushdns command*
c. At DNS2, run the net stop dns command. Then run the net start dns command
d. At the client computer, run the net stop dns command. Then run the net start dns command*
You are the administrator for your company's Windows 2000 domain. You have a Windows 2000 Server computer that is your Domain Name System (DNS) server. The DNS server contains the following types of resource records:
Start of Authority (SOA)
Name Server (NS)
Address (A)
Point (PTR)
Mail Exchange (MX)
Service (SRV).
You update a host resource record.
Which type of record may be associated with this record and need to be updated also?
a. The associated SOA resource record
b. The associated NS resource record
c. The associated A resource record
d. The associated PTR resource record
You are the administrator for a network. The network contains 6 Windows 2000 Server computers, one of which is configured to be the stand-alone EFS recovery operations server.
The stand-alone recovery server is not meeting your needs. You decide to implement a smart card to store the recovery agent certificate and private key.
You want to ensure proper recover operations procedures. What should you do after implementing the smart card?
a. Implement a recovery policy for the smart card
b. Implement a recovery agent account for the smart card
c. Map the certificate on the smart card to the EFS server computer
d. Map the certificate on the smart card to the designated recovery account
You are the administrator for your Windows 2000 network that uses the Network Address Translation (NAT) routing protocol to connect to the Internet.
Which component reacts with NAT through port allocation and packet translation?
a. TCP/IP
b. FTP Editor
c. ICMP Editor
d. IP Router Manager
You work for a local state agency that does not use Windows Internet Name Service (WINS) for NetBIOS name resolution. Instead, each client on the network copies a master LMHOSTS file from a central server during the logon process.
After experiencing a number of problems with the current Primary Domain Controller (PDC) named MIS4 of the HR domain, you decide to promote one of the Backup Domain Controllers (BDCs) named Payroll2 to PDC status and take the former PDC offline.
In the master LMHOSTS file, you take off the listing for the former PDC.
What is the other change you must make?
a. 128.131.24.122 Payroll2 #DOM:HR
b. 128.131.24.122 Payroll2 #DOMAIN:HR
c. 128.131.24.122 #PRE Payroll2 #DOM:HR
d. 128.131.24.122 Payroll #PRE #DOM:HR
You are the administrator for a Windows 2000 network. The network uses the Network Address Translation (NAT) routing protocol to connect to the Internet.
On a server on the network, you create a static mapping for the server that maps the Public IP Address of the server and TCP port 80 to the Private IP Address of the server and TCP port 80.
What did you accomplish by creating this mapping?
a. You properly configured a VPN server on the network
b. You properly configured a Web server on the network
c. You properly configured a RAS server on the network
d. You properly configured an FTP server on the network
You are an administrator for Windows 2000 Server network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. Another Windows 2000 Server computer has just been added to your network to act as your Windows Internet Name Service (WINS) server.
You want all the client computers on your network to use the WINS server for NetBIOS name resolution. You want to accomplish this with the least amount of administrative effort.
What should you do?
a. Use DHCP option 44
b. Use DHCP option 46
c. Use DHCP option 44 and 46
d. Configure WINS server settings in the LMHOSTS file
Your company's employees work from their home office. The employees have small Windows 2000 networks set up in their home office. You administer the Windows 2000 network at the corporate office.
The users have enabled Internet connection sharing on their networks to connect to the corporate office network. Users have set the following Internet Explorer options:
From the Connections tab, select the Never dial a connection option.
From LAN Settings on the Connections tab, clear the Automatically detect settings option.
From LAN Settings on the Connections tab, clear the Use automatic configuration script option.
From the Proxy Server tab, clear the Use a proxy server option.
What is the purpose for the above Internet Explorer configuration?
a. To allow inbound traffic to the user's network
b. To allow the user's network to use static IP addresses
c. To allow users to use the network's Internet connection
d. To allow the server on the network to be a proxy server
Your home office network contains 2 Windows 2000 Server computers, 1 Windows 2000 Professional client computer, and 1 Windows 98 second edition client computer.
You want to accomplish the following goals:
Provide one Internet connection for the entire network.
Provide network address translation.
Provide name resolution.
Provide IP address configurations for the entire network.
You perform the following tasks:
You enable Internet Connection Sharing.
You create a connection between the network and the Internet.
You install and configure LAN adapters connecting the client computers to the network.
Which goal is accomplished from these tasks?
a. Provide one Internet connection for the entire network
b. Provide network address translation
c. Provide name resolution
d. Provide IP address configurations for the entire network
You are the administrator for your company's network. Your network has three Windows 2000 Server computers, named Srvr1, Srvr2, and Srvr3. Each employee has his own Windows 2000 Professional computer. Also there is one Windows 2000 Professional computer, named Prof1, that is used by the general public.
Recently several files have been written to Srvr1 and Srvr2 that could have possibly caused great harm to your company's network. You suspect that the files came from Prof1. You want to monitor the traffic between these three computers.
Srvr3 is located in your office so you decide to capture the data there. You want to accomplish these goals with the least amount of administrative overhead.
What should you do?
a. On Srvr3, install the Network Monitor Tools. Then start Network Monitor and configure the capture data for Prof1, Srvr1, and Srvr2.
b. On Prof1, install the Network Monitor driver.
On Srvr1 and Srvr2, install the Network Monitor driver.
On Srvr3, install the Network Monitor Tools. Then start Network Monitor and configure the capture data for Prof1, Srvr1, and Srvr2.
c. On Prof1, install the Network Monitor Tools. Then start Network Monitor and configure capture data for Prof1.
On Srvr1 and Srvr2, install the Network Monitor driver.
On Srvr3, install the Network Monitor Tools. Then start Network Monitor and configure the capture data for Srvr1 and Srvr2.
d. On Prof1, install the Network Monitor driver
On Srvr1 and Srvr2, install the Network Monitor Tools. Then start Network Monitor and configure the capture data for Srvr1 and Srvr2, respectively.
On Srvr3, install Network Monitor Tools. Then start Network Monitor and configure the capture data for Prof1.
You administer a private Windows 2000 network that uses network address translation. You are testing to ensure that the network is protected from malicious Internet users. You are confirming that no unauthorized inbound traffic can access the network.
What are the only two ways that inbound Internet traffic can access the network? (Choose two.)
a. Through a dynamic mapping created at the time of access to the network
b. Through a dynamic tunneling mapping requested at the time of access to the network
c. Through a static mapping for Internet users to access specific resources on the network
d. In response to traffic initiated by a private network user that created a dynamic mapping
You are a Windows 2000 network administrator for your company. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers.
You are attempting to determine whether or not you need to install Internet connection sharing or network address translation. What are two of the situations for which you should NOT use these services?
a. When wanting to connect networks within an intranet
b. When wanting to connect all computers on the network to the Internet
c. When wanting to connect branch office networks to the corporate network over the Internet
d. When wanting to connect all computers on the network to the Internet through a translated connection
You have just been promoted by your company to network administrator. The network contains 3 Windows 2000 Server computers and 45 Windows 2000 Professional client computers.
Your supervisors want you to implement a Certificate Authority (CA) on one of the servers. You need to define the certificate policies and certificate practice statements for your company before you deploy the CAs.
What are three types of information that certificate policies can include? (Choose three.)
a. Certificate lifetime
b. Whether the private key can be exported
c. Certificate enrollment and renewal requirements
d. Physical, network, and procedural security of the CA
You have just installed a DNS server, created the necessary zones, and added the host records you need. From your network, you can resolve domain names with the ping utility and you can access several Web servers on the Internet by domain name. Users at another company who are not on your network, however, cannot resolve the domain names that you registered and set up on the DNS server. What could be the cause of this?
a. The DNS server is not granting authority to outside requests
b. You have not registered your DNS server with Network Solutions or any other similar service
c. The DNS server does not have a login with sufficient rights to fulfill requests over the Internet
d. Client computers who are trying to resolve the domain names must add the DNS server name to their TCP/IP settings
You are the administrator for your company's network. All network clients use Windows 2000 Professional. All network servers use Windows 2000 Server.
Your file server, named File1, has a shared folder named INFO on its C: drive. The C: drive is an NTFS partition. INFO contains sensitive company information.
You have been asked to encrypt the folder, all its subfolders, and all the files contained therein. You want the encryption process to continue if any error occurs.
You go to a command prompt on File1. Which command should you type?
a. cipher /e /s
b. cipher /d /s
c. cipher /e /s:info
d. cipher /e /s:info /I
You are the administrator for your Windows 2000 network. You have a Windows Internet Name Service (WINS) server, named WINS1, and have established a performance baseline for it. Every week you monitor performance and compare the new results with the performance baseline on file.
Recently you have noticed dramatic increases in the MemoryPages/sec counter accompanied by decreases in ServerBytes Total/sec. There are not any significant changes in any other counters you monitor.
You want to prevent these increases and decreases from happening again and want to return WINS1 performance to normal levels. You want to accomplish this with the least amount of administrative effort.
What should you do?
a. Expand the size of the paging file
b. Upgrade the physical memory in the server
c. Move the page file to a different volume than the boot volume
d. Install a second WINS server to act as a backup for all WINS traffic
You are the administrator for your company's domain, which currently contains 200 NetWare clients, 75 TCP/IP clients, and 50 NetBEUI clients. You have a domain controller running Windows 2000 Server.
You want to configure the domain controller for optimal network protocol performance. You want to accomplish this goal with the least amount of administrative overhead possible.
At the domain controller, you check the Advanced setting of your Local Area Network and view the bindings order as shown below:
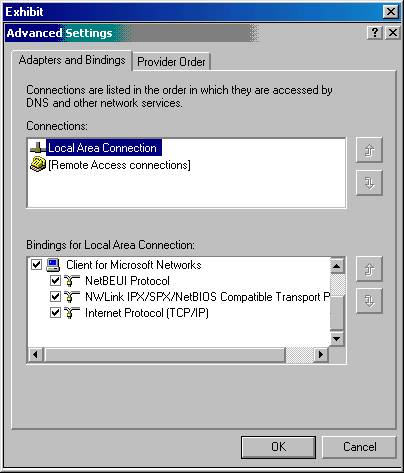
Which actions should you take?
a. Do nothing. The current binding list is properly configured.
b. Rearrange the protocols so that they are listed in this order: NWLink IPX/SPX, Internet Protocol (TCP/IP), and NetBEUI.*
c. Delete all three protocols. Restart the computer. Reinstall the protocols in this order: NWLink, TCP/IP, NetBEUI.
d. Delete all three protocols. Restart the computer. Reinstall the protocols in this order: NetBEUI, TCP/IP, NWLink.
You are the administrator for a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers. One of the servers on the network is configured to be the enterprise certificate authority (CA).
You are determining the necessary certificate types you will need to implement on the CA. One of the certificate types you decide on is a certificate that is used as a certificate request agent. The certificate will be issued to computers, as opposed to people or routers.
Which certificate template will you use for this type of certificate?
a. CEP encryption
b. EnrollmentAgent
c. MachineEnrollmentAgent
d. IPSECIntermediateOnline
You are the administrator for your company's network. Recently you have begun upgrading all your Windows NT 4.0 Server computers to Windows 2000 Server. It is now time to upgrade your Windows Internet Name Service (WINS) server.
You upgrade the operating system.
Which step must you do to complete the upgrade of the WINS server?
a. Restore the database from backup. Restart WINS.
b. Run the edbutil.exe utility from the winntsystem32 folder. Restart WINS.
c. Compact the database. Restart WINS.
d. Scavenge the database. Restart WINS.
You administer your company's network. You have 20 Windows 2000 Professional computers operating in a switched network environment running TCP/IP. Ten of the Windows 2000 Professional computers are on subnet A. The other ten Windows 2000 Professional computers are on subnet B.
The company uses a Windows 2000 Server computer running Internet Authentication Service (IAS) to connect to the Internet. The IAS server is on subnet B.
You decide to set up Network Monitor to monitor all traffic on your network.
You install Network Monitor on the IAS server. You configure Network Monitor properly to monitor all TCP/IP traffic.
Which packets will you be able to monitor?
a. All packets
b. Only packets sent from the IAS server
c. Only packets addressed to the IAS server
d. All packets addressed to and sent from the IAS computer
You are the administrator for a Windows 2000 Server network. The network is a native mode domain, which contains a remote access enabled server.
The users attempt to connect to the remote access server. All connection attempts are rejected. How are the dial-in permissions set for the user accounts?
a. Deny access
b. Allow access
c. Deny remote access permission policy
d. Control access through Remote Access Policy
You are the administrator for your Windows 2000 network. You have a Windows 2000 Server computer that is your Windows Internet Name Service (WINS) server.
While doing routine maintenance, you notice that the WINS database is 50 MB and decide to compact it using the Jetpack.exe utility.
Which steps must be completed before you do this? (Choose all that apply.)
a. Stop the WINS service
b. Start the WINS service
c. Change to the %SystemRoot% directory
d. Change to the %SystemRoot%System32Wins directory
You are installing and configuring Certificate Authorities (CAs) on your Windows 2000 network. You are currently configuring the public key Group Policy for the domain.
You configure the Group Policy to specify automatic enrollment and renewal for certificates. You attempt to test this configuration, but the enrollment is not working properly.
What may be the cause of the problem?
a. An enterprise CA is not online
b. The Group Policy is not enabled for the domain
c. Certificate enrollment and renewal is not enabled for the Group Policy
d. You failed to add the CA certificate to the trusted root certification authorities container
You have a DNS server and Internet Information server on the same computer. The DNS server is resolving all domain names for the Web sites that are hosted by Internet Information server. You have leased 32 IP addresses but the DNS server and Internet Information server are reporting errors when you try to use them. What could be the problem?
a. A reverse lookup zone has not been created
b. The IP addresses may not be bound to the network card
c. The DNS server may not have the capacity for all 32 IP addresses
d. The server may not have enough memory for an IP pool of 32 addresses
You are the administrator for a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers.
You want to configure the network with a remote access server that is also a RADIUS client. Which steps should you take to accomplish this task? (Choose all that apply.)
a. Configure the remote access server
b. Configure the remote access server for RADIUS accounting
c. Configure the remote access server for IAS authentication
d. Configure the remote access server for RADIUS authentication
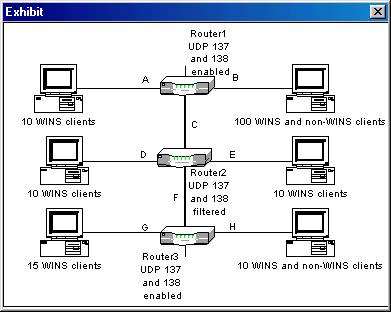
You are part of a team of network administrators for a Windows 2000 network. The network uses Windows 2000 Server computers and Windows 2000 Professional client computers. The network consists of 16 subnets and 15 routers. All subnets are named beginning with the letter A through P. All routers are named beginning with R1 through R15.
You and the other team members decide to add an additional subnet and router. You install Routing and Remote Access on a Windows 2000 server. You then set up Routing Information Protocol (RIP) for Internet Protocol (IP) version 2 and make the computer the router R16. After adding the subnet and router, the network is configured as shown below:
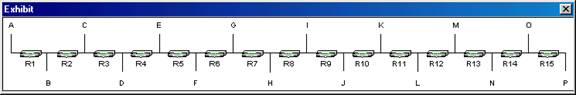
During the testing phase of the new network addition, you discover that the
maximum hop count for RIP for IP is 15.
What problem will this cause as a result?
a. The users on subnet P will not be able to reach the users on subnet A, and the users on subnet A will not be able to reach the users on subnet P.*
b. The users on subnet O will not be able to reach the users on subnet A, and the users on subnet A will not be able to reach the users on subnet O.
c. The users on subnet O will not be able to reach the users on subnet P, and the users on subnet P will not be able to reach the users on subnet O.
d. The users on subnet B will not be able to reach the users on subnet A, and the users on subnet A will not be able to reach the users on subnet B.
You are the administrator for your company's Windows 2000 network. Your company has many locations and operates in an OSPF-routed environment. It consists of Windows 2000 Server computers and Windows 2000 Professional client computers.
From the External Routing tab in the OSPF Routing Protocol Properties dialog box, you make configuration changes.
Which type of changes did you make?
a. You set areas for the internal and border routers on the network
b. You set virtual interfaces for the internal border routers on the network
c. You made routing identification and event logging configurations for the internal and border routers on the network
d. You made changes to the external and route filtering configuration for the internal and border routers on the network
You are the administrator for your company's network. Recently you have begun upgrading all your Windows NT 3.51 Server computers to Windows 2000 Server. It is now time to upgrade your Windows Internet Name Service (WINS) server.
You upgrade the operating system.
Which step must you do to complete the upgrade of the WINS server?
a. Compact the database. Restart WINS.
b. Scavenge the database. Restart WINS.
c. Restore the database from backup. Restart WINS.
d. Run the upg351db.exe utility from the winntsystem32 folder. Then run the ebutil.exe utility from the winntsystem32 folder. Restart WINS.
You administer your company's Windows 2000 network. Your company employs a sales force that needs access to the latest company data when traveling. You want to ensure that the company will establish a network connection for your salespeople regardless of where the call originates.
Your company also allows customers access to the network using Routing and Remote Access to view and track orders. To ensure network and data security, your company wants to specify the location from which customers can connect to your network.
You want to configure your company's Routing and Remote Access server (RRAS) to facilitate access for salespeople and for customers. You want both the salespeople and the customers to use mutual authentication to provide protection against remote server impersonation.
Which settings should you configure? (Choose three.)
a. Set Callback option to Always Callback To for salespeople
b. Set Callback option to Set by Caller for salespeople
c. Set Callback option to No Callback for customers
d. Set Callback option to Always Callback to for customers
e. Enable Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2)
You are the administrator for your company's network. You have several NetWare servers running on your network and want to synchronize the user accounts between your Windows 2000 Server domain and your NetWare Servers.
You select all the NetWare servers and use the Directory Service Manager for NetWare (DSMN) to synchronize the user accounts.
You receive the following error message: 'NWC is a NetWare 4.x server. It cannot be added to the domain.'
What should you do?
a. Remove the bindery emulation mode option from NWC. Reboot NWC. Rerun DSMN, selecting only NWC for synchronization
b. Do nothing. NetWare 4.x servers running in bindery emulation mode cannot be added to Windows 2000 Server domains under any circumstances.
c. Using REGEDT32.exe on the Windows 2000 Server domain controller, go to the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesMSSYNCParameters key. Choose Add Value option for Edit menu. In Value Name, type Allow4X. In Type, enter REG_DWORD. In Data, enter 1. Close the Registry. Restart the Windows 2000 Server.
d. Using REGEDT32.exe on the Windows 2000 Server domain controller, go to the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesMSSYNCParameters key. Choose Add Value option for Edit menu. In Value Name, type Allow4X. In Type, enter REG_DWORD. In Data, enter 0. Close the Registry. Restart the Windows 2000 Server.
Your company has a network with two subnets spanning one DNS zone. You must install a DNS server to resolve domain names, and management has instructed you to install a secondary DNS server. Of the following strategies, which has the most merit?
a. Install both primary and secondary servers for the zone on both subnets. This way each subnet will have complete fault tolerance.
b. Install the primary and secondary DNS servers for the zone on the same subnet. This will provide for the best performance and occupy the least amount of bandwidth.
c. Install the primary and secondary DNS servers for the zone on different subnets. If connectivity to one subnet is lost, DNS clients can still direct queries to the name server on the other subnet
d. Install both primary and secondary servers for the zone on both subnets. Use IP Forwarding to enable a push-pull relationship between the servers on the subnets. This way each subnet will have complete fault tolerance and the bandwidth requirements will be minimal
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer with Windows Internet Name Service (WINS) installed.
You notice that you are experiencing long delays when resolving NetBIOS names. You go to the WINS server and open Event Viewer. A WINS error message appears as shown below:
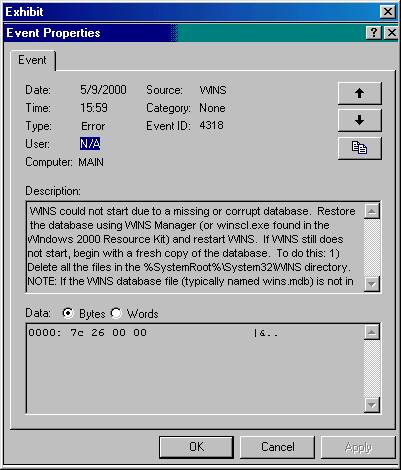
First you restore the database using the WINS Manager and restart WINS. That does not fix the problem.
What should you do next?
a. Open the %SystemRoot%System32WINS folder. Delete the *.mdb file. At the Command Prompt, type net start wins, and then press enter.
b. Open the %SystemRoot%System32WINS folder. Delete the *.log files. At the Command Prompt, type net start wins, and then press enter.
c. Open the %SystemRoot%System32WINS folder. Delete the *.mdb file and the .log files. At the Command Prompt, type net start wins, and then press enter.
d. Open the %SystemRoot%System32WINS folder. Delete the *.mdb file. At the Command Prompt, type the net stop wins, and then press enter. Then type net start wins, and then press enter.
Your company has a limited bandwidth when accessing the Internet. A number of suggestions related to DNS have been recommended. Of the following suggestions, which makes the most sense?
a. Make sure that the DNS service on your company server resolves only domain names queries
b. Make sure that the DNS service on your company server resolves only NetBIOS name queries
c. From the DNS console, disable forwarding by deselecting the Enable Forwarder(s) check box
d. From the DNS console, configure forwarding by selecting the Enable Forwarder(s) check box
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. You have 50 client computers on your network. You have been assigned 200 IP addresses.
You want to reduce network traffic due to lease renewal queries. You want to accomplish this with the least amount of administrative overhead.
What should you do?
a. Increase the lease duration
b. Decrease the lease duration
c. Assign static IP addresses
d. Create client reservations for all your client computers
You are the administrator for your Windows 2000 domain. You have been asked to configure Windows Internet Name Service (WINS) name resolution for all the computers on your network.
You have a total of six subnets, connected by routers that do not forward NetBIOS name broadcasts. Each subnet contains both WINS and non-WINS clients and one Windows 2000 Server computer, as shown below:
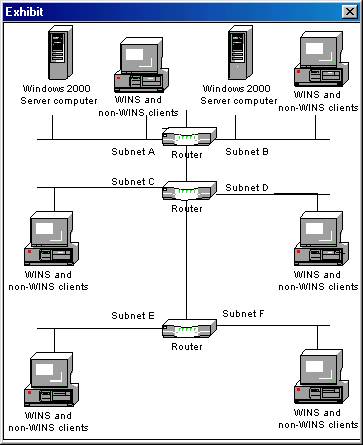
You want to accomplish the following goals:
All computers must be able to register their NetBIOS names with WINS.
Broadcast traffic must be kept to a minimum.
WINS clients must have a level of fault tolerance for NetBIOS name resolution.
Hardware purchases must be kept to a minimum.
You perform the following actions:
On the Windows 2000 Server computer on subnet A, install the Windows Internet Name Service (WINS). Make it the primary WINS server for all WINS clients. On the Windows 2000 Server computer on subnet B, install WINS. Make it the secondary WINS server for all WINS clients.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. All computers must be able to register their NetBIOS names with WINS.
b. Broadcast traffic must be kept to a minimum.
c. WINS clients must have a level of fault tolerance for NetBIOS name resolution.
d. Hardware purchases must be kept to a minimum.
You are the administrator for a Windows 2000 Server network. The network contains three Windows 2000 Server computers and 35 Windows 2000 Professional client computers.
You want to accomplish the following goals:
Install and enable Network Address Translation (NAT) on the network.
Allow Internet users to access resources from the network.
Install and enable Internet Connection Sharing.
Configure dynamic IP addresses on the network.
You perform the following actions:
You configure a static IP address configuration on the resource server.
You exclude the IP address used by the resource computer from the range of IP addresses allocated by the NAT computer.
Configure a special port with a dynamic mapping of a public address and port number to a private address and port number.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Configure dynamic IP addresses on the network
b. Install and enable Internet Connection Sharing
c. Allow Internet users to access resources from the network
d. Install and enable Network Address Translation (NAT) on the network
You are performing maintenance on your DNS Server service. You need the following tasks performed:
The primary zone is deleted.
The primary zone is removed from the registry.
The primary zone is removed from Active Directory.
The zone is to reappear as an Active Directory integrated primary zone after deletion.
The following actions are performed:
From the Advanced Tab on the DNS server properties page in DNS Console, you set the Load Data on Startup field equal to Registry.
You delete the zone.
You answer Yes to the Delete from Active Directory question.
From the Advanced Tab on the DNS server properties page in DNS Console, you set the Load Data on Startup field equal to Active Directory and registry.
DNS server polls the directory for changes.
Which task or tasks are performed from these actions? (Choose all that apply.)
a. The primary zone is deleted
b. The primary zone is removed from the registry
c. The primary zone is removed from Active Directory
d. The zone is to reappear as an Active Directory integrated primary zone after deletion
You are the administrator for your company's Windows 2000 domain. On this domain, you have a Windows 2000 Server computer acting as your company's Internet interface.
This morning when you came to work, you noticed that you had an unusually long wait time to access resources on your network. You run several tests but cannot seem to find any problems although the access times are incredibly long.
When the users come in for work, they immediately start complaining about network performance. You then decide to start checking packets on the network.
After investigating the problem, you notice that a denial of service attack has flooded your Internet server with 'Destination Unreachable' packets.
You want to prevent this from happening again with the least amount of administrative overhead possible. You do not want to prevent legitimate packets from being forwarded.
What should you do?
a. Configure input filters on the Internet server to accept all packets except IP Address 10.0.0.0 with Subnet Mask 255.0.0.0 and IP Address 192.168.0.0 with Subnet Mask 255.255.0.0.
b. Configure input filters on the Internet server to accept all packets except IP Address 10.0.0.0 with Subnet Mask 255.0.0.0 and IP Address 172.16.0.0 with Subnet Mask 255.240.0.0.
c. Configure input filters on the Internet server to accept all packets except IP Address 10.0.0.0 with Subnet Mask 255.0.0.0, IP Address 172.16.0.0 with Subnet Mask 255.240.0.0, and IP Address 192.168.0.0 with Subnet Mask 255.255.0.0.
d. Configure input filters on the Internet server to accept all packets except IP Address 10.0.0.0 with Subnet Mask 255.0.0.0, IP Address 127.0.0.1 with Subnet Mask 255.0.0.0, IP Address 172.16.0.0 with Subnet Mask 255.240.0.0, and IP Address 192.168.0.0 with Subnet Mask 255.255.0.0.
Your company recently hired you as the administrator for a Windows 2000 network. The network uses Windows 2000 Server and Professional computers.
After researching the network for necessary improvements, you decide to implement demand-dial routing. You implement the feature and begin testing the network. You discover that an on-demand connection is not made automatically.
What may be the cause of the problem?
a. IP routing is not enabled
b. Dial-out hours is not enabled
c. The demand-dial interface is not properly configured
d. Static routes are not properly configured on the network
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server.
The current DHCP server is no longer sufficient to service your company's needs. It has been decided that it will be completely replaced.
A new Windows 2000 Server computer is purchased. You stop the DHCP service on the current DHCP server. You set up the new server and install the DHCP service. You copy the contents of the %SystemRoot%System32DHCP folder from the original DHCP server and place it on the new DHCP server. You then start the DHCP service on the new computer.
What final step is necessary for the new DHCP server to function properly?
a. Use the Jetpack.exe command
b. Restore the DHCP database from backup
c. Use the Reconcile command in the DHCP Manager
d. Run the ipconfig /renew command at all client computers
What information is required by a client to use DNS?
a. Domain name
b. In-addr.arpa
c. IP address of a DNS server
d. Optional subdomain names
You are the administrator of your company's Windows 2000 domain. Your company has three locations:
You are experiencing problems managing remote access policies across the WAN. In addition, because of the distance between the sites and the low bandwidth available, users have been complaining about delays with authentication.
You decide to set up the Windows 2000 Routing and Remote Access servers at each site to use Internet Authentication Service (IAS). What will this configuration provide for the company?
a. Centralized authentication and centralized accounting methods
b. Decentralized authentication and centralized accounting methods
c. Centralized authentication and decentralized accounting methods
d. Decentralized authentication and decentralized accounting methods
You are the administrator for a Windows 2000 Server network. The network is a medium-sized network with 15 subnets. You have a Windows Internet Name Service (WINS) server. One of the subnets is currently configured to use NetBIOS broadcasts to resolve names.
You need to configure the clients on this subnet to resolve names across subnets. You want to accomplish this with the least amount of administrative effort.
What should you do?
a. Change the node type on all computers on this subnet to P-node
b. Change the node type on all computers on this subnet to M-node
c. Change the node type on all computers on this subnet to H-node
d. Create and configure the LMHOSTS. Place this file on all computers on the subnet
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. Another Windows 2000 Server computer is your Domain Name System (DNS) server.
You want to enable the return of a client's Fully Qualified Domain Name (FQDN) to the DHCP server.
What should you do?
a. Use DHCP option code 6
b. Use DHCP option code 81
c. Create an address (A) DNS resource record (RR) for the DHCP server
d. Create a pointer (PTR) DNS RR for the DHCP server
Recently your company had hackers break into your network, which consists of a Windows 2000 domain and a stand-alone remote access server.
Realizing the need for tighter security, your CEO has come to you for suggestions. You need to prevent incidents like this from happening again.
You decide to implement the Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2). What did the hackers do when breaking into your network that would cause you to implement this protocol?
a. They replaced the packets sent between the remote access server and the remote access client
b. They created a new remote access client that was able to access the remote access server of your organization
c. They created a remote access server that impersonated the stand-alone remote access server of your organization
d. They determined the client's password by filtering the packets sent between the remote access server and the remote access client
You are the administrator for your Windows 2000 domain. Your network contains a domain controller named R1 with remote access enabled and a domain member named D1. D1 is a Windows 2000 Professional computer. R1 has an outbound connection configured for all users needing access to a Virtual Private Network (VPN).
You want to create inbound connection to D1. You want to create 4 inbound connections, but find that you are only able to create up to 3 inbound connections. Why are you limited to this number of connections?
a. Windows 2000 Professional is limited to creating three inbound connections for VPNs only
b. Windows 2000 Professional is limited to creating inbound connections for dial-up, VPN, and direct only
c. Windows 2000 Professional is limited to creating three inbound connections for direct connections only
d. Windows 2000 Professional is limited to creating three inbound connections for dial-up connections only
You are the administrator for a Windows 2000 Server network. The network contains two Windows 2000 servers, one NetWare server running NetWare version 3.12, and one NetWare server running NetWare version 3.11.
You have installed the NWLink IPX/SPX/NetBIOS Compatible Transport Protocol on the Windows 2000 servers. To which setting will the frame type default for the Windows 2000 servers?
a. Ethernet II
b. Auto Detect
c. Ethernet 802.2
d. Ethernet 802.3
e. Ethernet SNAP
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Windows Internet Name Service (WINS) server.
You have several places where you would like backups of the WINS database to be placed:
C:WINNTSystem32WINS (an NTFS drive)
D:backup (a FAT drive)
MAINbackup (an NTFS partition)
G:WINS (a tape drive).
You use the WINS management console to set up the WINS database backups.
Which one of the locations will not be a valid option?
a. G:WINS (a tape drive)
b. D:backup (a FAT drive)
c. MAINbackup (an NTFS partition)
d. C:WINNTSytem32WINS (an NTFS drive)
You administer a Windows 2000 network. The network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers. The network uses DHCP and Network Address Translation.
You have recently been allocated multiple IP addresses from your company's ISP. What must you do to complete the configuration for your network?
a. You must configure DHCP with the range of IP addresses
b. You must register the range in the Static Routes component
c. You must register the range of IP addresses in the IGMP component
d. You must configure the network address translation interface with the range of IP addresses
You are the administrator for a Windows 2000 domain with Remote Access enabled. You want to implement a Virtual Private Network (VPN) so clients can connect to your network through the Internet.
You select a Windows 2000 Server computer to act as your VPN server. You configure the server to use the Layer Two Tunneling Protocol (L2TP) and the Point-to-Point Tunneling Protocol (PPTP).
What is a reason for implementing these protocols?
a. You wanted protocols that use MPPE encryption
b. You wanted protocols that will replace the VPN
c. You wanted protocols that will encapsulate PPP frames
d. You wanted protocols that are challenge-response authentication protocols
You have just taken a job with a company that would like to convert its current network operating system to Windows 2000. The company has four subnets on its TCP/IP network, each of which will have its own Backup Domain Controller (BDC), except for the subnet on which the Primary Domain Controller (PDC) will reside.
The company would like to allow browsing across the entire network without needing the implement Windows Internet Name Service (WINS) on a Windows 2000 Server computer.
What should you do?
a. Create an LMHOSTS file. Create entries in the LMHOSTS file for the PDC and all BDCs using the #DOM keyword. Place this file on the PDC.
b. Create an LMHOSTS file. Create entries in the LMHOSTS file for the PDC and all PDCs using the #DOM keyword. Place this file on the PDC and all BDCs.
c. Create an LMHOSTS file. Create an entry in the LMHOSTS file for the PDC and all BDCs using the #MH keyworkd. Place this file on the PDC.
d. Create an LMHOSTS file. Create an entry in the LMHOSTS file for the PDC and all BDCs using the #MH keyword. Place this file on the PDC and all BDCs.
64. You are the administrator for a Windows 2000 network. Your network contains two DHCP servers named D1 and D2. You set up a Remote Access Server, named R1, for dial-up access. You want to accomplish the following goals:
Use a static IP address pool.
Prevent the allocation of APIPA addresses in the event of a failure.
Use 40-bit MPPE encryption.
Implement a RADIUS server.
You take the following actions:
On R1, you configure the DHCP Relay Agent with the IP address of the D1 DHCP server.
You set up MS-CHAP as the authentication protocol on R1.
You implement Internet Authentication Service on R1.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Implement a RADIUS server
b. Use 40-bit MPPE encryption
c. Use a static IP address pool
d. Prevent the allocation of APIPA addresses
Your company has promoted you to the position of Network Administrator for a Windows 2000 network. The network contains a dedicated WINS server for name resolution.
You are currently monitoring the different services enabled on the network. From the WINS Server statistics, you view the Total registrations statistic. The value for this statistic is 15,000.
What should you do?
a. Add a second WINS server
b. Add a second processor in your WINS server
c. Add a high-performance disk subsystem to your WINS server
d. Add more RAM to your current WINS server
You are the administrator for your company's Windows 2000 network. Your network is configured as shown below:
You have been asked to use Windows Internet Name Service (WINS) to provide NetBIOS name resolution for your entire network. You want to complete this task with as little administrative overhead as possible.
You set up a Windows 2000 Server computer on segment A and install the Windows Internet Name Service (WINS) on the computer.
What do you accomplish?
a. Only clients on segment A are able to resolve NetBIOS names.
b. Only clients on segment A and B are able to resolve NetBIOS names.
c. All clients except the non-WINS clients on segments B and H are able to resolve NetBIOS names.
d. All clients except the non-WINS clients on segment H are able to use WINS resolve NetBIOS names.
You are the administrator for your company's Windows 2000 Server
network. You company has a main office
in
The routers between the offices supports the forwarding of BOOTP messages. At each branch office, you have a local user who is responsible for all administrative duties. Currently the local administrator is responsible for configuring the TCP/IP settings for all the Windows 2000 Professional computers at his/her local branch.
You have been experiencing network communication problems which were the direct result of configuration errors. You want to prevent this from happening again.
What should you do? (Choose two.)
a.
Install and configure a DHCP server in
b. Install and configure a WINS server in
c.
Install and configure a DNS server in
d. On each Windows 2000 Professional computer, change the TCP/IP properties to Obtain an IP address automatically
You administer a Windows 2000 network. The network consists of 5 subnets and 7 routers. The routers are configured to use Open Shortest Path First (OSPF). The network also consists of Windows 2000 Professional client computers and Windows 2000 Server computers.
You decide to implement external route filters on the autonomous system boundary routers (ASBRs). Which statement is true about these filters?
a. External route filters are used to filter routes from any source
b. External route filters are only used to filter routes from OSPF sources
c. External route filters are used to filter routes from a Multilink server
d. External route filters are only used to filter routes from non-OSPF sources
You are the administrator for your company's Windows 2000 network. Certificate Services are installed on a Windows 2000 Server computer, and the computer is configured to be the Enterprise Certificate Authority (CA) for the network.
The CA is properly issuing licenses. You now need to view the CA's publication and certificate revocation lists (CRLs).
What can you use to accomplish this task?
a. The Active Directory
b. The CA snap-in of Performance Monitor
c. The CA snap-in of the Microsoft Management Console (MMC)
d. The HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesCertSrv registry key
You have just installed Windows 2000. When you first open the DNS console, the DNS Server Configuration wizard allows you to set up the DNS server as a root name server to host the zone. In which situation would this be the correct choice?
a. When your intranet will be connected to the Internet
b. When your intranet will not be connected to the Internet
c. When the DNS server needs to operate as the primary DNS server
d. When the DNS server needs to operate as the secondary DNS server
You are the administrator for a Windows 2000 network. Your network contains 5 Windows 2000 Server computers on which you wish to set up Internet Protocol Security (IPSec).
One of the Windows 2000 Server computers, named BERT, stores and exchanges highly sensitive data. BERT must be configured to secure all outgoing traffic.
Another Windows 2000 Server computer, named ERNIE, needs to be able to exchange data with secure computers but will also need to communicate with non-secure clients.
The other 3 Windows 2000 Server computers should reply to requests for secure communication appropriately.
You install IPSec on all 5 Windows 2000 Server computers using the default settings. You want the policy settings on the 5 computers to be correct.
What should you do?
a. On BERT, remove the Client (Respond Only) and Server (Request Security) options, leaving the Secure Server (Require Security) option.
On ERNIE, remove the Client (Respond Only) option, leaving the Server (Request Security) and Secure Server (Require Security) options.
On the other 3 Windows 2000 Server computers, remove the Server (Request Security) and Secure Server (Require Security) options, leaving the Client (Respond Only) option.
b. On BERT, remove the Client (Respond Only) and Server (Request Security) options, leaving the Secure Server (Require Security) option.
On ERNIE, remove the Client (Respond Only) and the Secure Server (Require Security) options, leaving the Server (Request Security) option.
On the other 3 Windows 2000 Server computers, remove Secure Server (Require Security) option, leaving the Client (Respond Only) and Server (Request Security) options.
c. On BERT, remove the Client (Respond Only)option, leaving the Server (Request Security) and Secure Server (Require Security) options.
On ERNIE, remove the Client (Respond Only) and the Secure Server (Require Security) options, leaving the Server (Request Security) option.
On the other 3 Windows 2000 Server computers, remove the Server (Request Security) and Secure Server (Require Security) options, leaving the Client (Respond Only) option.
d. On BERT, remove the Client (Respond Only) and Server (Request Security) options, leaving the Secure Server (Require Security) option.
On ERNIE, remove the Client (Respond Only) and the Secure Server (Require Security) options, leaving the Server (Request Security) option.
On the other 3 Windows 2000 Server computers, remove the Server (Request Security) and Secure Server (Require Security) options, leaving the Client (Respond Only) option.
You are the administrator for a Windows 2000 network. The network contains 4 subnets and 5 routers. The network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers.
You configure the Windows 2000 routers to use demand-dial routing. You also decide to use demand-dial filters.
Which type of functionality will this provide?
a. The filtering of traffic types allowed to cross routers
b. The filtering of traffic types allowed to create a connection
c. The filtering of traffic types allowed to access a data server
d. The filtering of traffic types allowed into and out of an interface
You are the administrator for your company's Windows 2000 Server network. You perform the following actions on the network:
Enable Password Authentication Protocol (PAP) as an authentication protocol on the remote access server.
Enable PAP on the appropriate remote access policy.
Enable PAP on the remote access client running Windows 2000.
Using this network configuration, which statement is true?
a. Remote access clients will be able to tunnel to the remote access server
b. Remote access clients will be able to access a remote access MS-DOS 5.0 server
c. Remote access clients will be able to utilize encryption while connecting to the remote access server
d. Remote access clients will be able to utilize data compression while connecting to the remote access server
You are the administrator for your company's Windows 2000 Server network. Your company currently has three Windows 2000 Server computers. One of the servers is the domain controller and processes all authentication requests. The second server is the Domain Name System (DNS) / Windows Internet Name Service (WINS) server. The third server currently acts as your print and file server.
Your supervisor informs you that the company wants to set up a Web site. She asks you to set up the current print and file server as the Internet Information Services (IIS) server. You are concerned that the IIS requests will prevent the computer from servicing printer and file requests. You want the server to equally service these requests.
What can you do?
a. Edit the master properties of the WWW Service in the Internet Information Services properties dialog box. On the Performance tab, set Process Throttling to 50%.
b. Edit the master properties of the WWW Service in the Internet Information Services properties dialog box. On the Performance tab, set Process Throttling to 75%.
c. Edit the master properties of the WWW Service in the Internet Information Services properties dialog box. On the Performance tab, set Performance Tuning to More than 100,000.
d. Edit the master properties of the WWW Service in the Internet Information Services properties dialog box. On the Performance tab, set Performance Tuning to Fewer than 100,000.
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server.
You have been experiencing trouble with the DHCP server so you decide to turn on DHCP logging. Later you view the log and notice several events of Event ID Code 02.
What does this Event Message signify?
a. The log was started
b. The log was stopped
c. The log was temporarily paused due to low disk space
d. A lease was renewed by a client
You are implementing a Certificate Authority (CA) on a Windows 2000 Server computer for your network. You decide to use a CA hierarchy model. You plan to implement a root CA on one Windows 2000 Server computer, and the intermediate and issuing CAs on separate Windows 2000 Server computers.
You want to ensure the tightest security for all CAs, but especially for the root CA computer. What is one way to improve security on this computer?
a. Install the root CA in a secure data center
b. Move the recovery keys to a separate computer
c. Nightly remote the RSA folder to removable media
d. Ensure the computer does not have a network adapter
You administer your company's network. Your company has offices in
On AtlSrvr you have implemented Internet Protocol Security
(IPSec) with the default configuration. You have not implemented IPSec in
You want to protect the highly sensitive data on
AtlSrvr. You want TokSrvr to use secure
communications most of the time. However,
What should you do?
a. On AtlSrvr, remove all policies except the Secure Server (Require Security) option.
On TokSrvr, enable IPSec and remove all policies except the Server (Request Security) option.
On both servers enable all transmissions to use IPSec Triple Data Encryption Standard (TripleDES).
b. On AtlSrvr, remove all policies except the Secure Server (Require Security) option..
On TokSrvr, enable IPSec and remove all policies except the Client (Respond Only) option.
On both servers, enable all transmissions to use IPSec Data Encryption Standard (DES).
c. On AtlSrvr, remove the Client (Respond Only) option.
On TokSrvr, enable IPSec and remove all policies except the Client (Respond Only) option.
On both servers, enable all transmissions to use IPSec TripleDES.
d. On AtlSrvr, remove all policies except the Secure Server (Require Security) option.
On TokSrvr, enable IPSec and remove all polices except the Server (Request Security) option.
On both servers, enable all transmissions to use IPSec DES.
You administer a Windows 2000 Server network. The network contains a dedicated FTP server that is using the default ports. Your network also contains a Web server using the default ports.
You want to configure a filter to prevent malicious attacks on other services running on the FTP server. Which filters should you configure?
a. Input filter for the Source IP Address of FTP Server and the TCP Source Port 20.
Input filter for the Source IP Address of FTP Server and the TCP Source Port 21.
Output filter for the Destination IP Address of FTP Server and the TCP Destination Port 20.
Output filter for the Destination IP Address of FTP Server and the TCP Destination Port 21.
b. Output filter for the Source IP Address of FTP Server and the TCP Source Port 20.
Output filter for the Source IP Address of FTP Server and the TCP Source Port 21.
Input filter for the Destination IP Address of FTP Server and the TCP Destination Port 20.
Input filter for the Destination IP Address of FTP Server and the TCP Destination Port 21.
c. Input filter for the Source IP Address of Web Server and the TCP Source Port 20.
Input filter for the Source IP Address of Web Server and the TCP Source Port 21.
Output filter for the Destination IP Address of Web Server and the TCP Destination Port 20.
Output filter for the Destination IP Address of Web Server and the TCP Destination Port 21.
d. Output filter for the Source IP Address of Web Server and the TCP Source Port 20.
Output filter for the Source IP Address of Web Server and the TCP Source Port 21.
Input filter for the Destination IP Address of Web Server and the TCP Destination Port 20.
Input filter for the Destination IP Address of Web Server and the TCP Destination Port 21.
You are the administrator for a Windows 2000 network for your company. The network contains three Windows 2000 Server computers and 25 Windows 2000 Professional client computers.
You configure Network Address Translation (NAT) on one of the servers on the network. While testing NAT, you find that the TCP/UDP port translation is not enabled.
Which problem might this have caused?
a. The private interface on the computer might be lost
b. The NAT computer might not properly translate packets
c. The PPTP protocol might not properly translate packets
d. The range of private addresses on the computer might be lost
You have created an Active Directory-integrated forward lookup zone. You cannot locate the zone database file that is associated with that zone on the hard disk of the your Active Directory server. Where is the zone database information stored? (Choose two.)
a. On the DNS server
b. On the DHCP server
c. On the WINS server
d. In Active Directory
e. On each client computer
You are the administrator for your Windows 2000 domain. You have been asked to configure Windows Internet Name Service (WINS) name resolution for all the computers on your network.
You have a total of six subnets, connected by routers that do not forward NetBIOS name broadcasts. Each subnet contains both WINS and non-WINS clients and one Windows 2000 Server computer.
You want to accomplish the following goals:
All computers must be able to register their NetBIOS names with WINS.
Broadcast traffic must be kept to a minimum.
WINS clients must have a level of fault tolerance for NetBIOS name resolution.
Hardware purchases must be kept to a minimum.
You perform the following actions:
On the Windows 2000 Server computer on subnet A, install the Windows Internet Name Service (WINS). Make it the primary WINS server for all WINS clients. On the Windows 2000 Server computer on subnet B, install WINS. Make it the secondary WINS server for all WINS clients.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. All computers must be able to to register their NetBIOS names with WINS
b. Broadcast traffic must be kept to a minimum
c. WINS clients must have a level of fault tolerance for NetBIOS name resolution
d. Hardware purchases must be kept to a minimum
You administer your company's network. You have 20 Windows 2000 Professional computers operating in a switched network environment running TCP/IP. Ten of the Windows 2000 Professional computers are on subnet A. The other ten Windows 2000 Professional computers are on subnet B.
The company uses a Windows 2000 Server computer running Internet Authentication Service (IAS) to connect to the Internet. The IAS server is on subnet B. The network configuration is shown below:
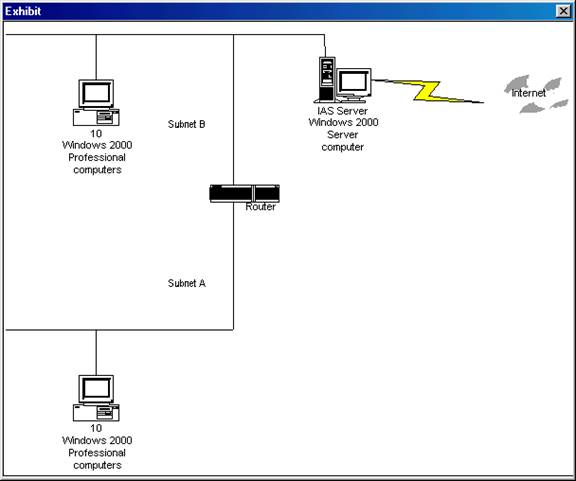
You decide to set up Network Monitor to monitor all traffic on your network.
You install Network Monitor on the IAS server. You configure Network Monitor properly to monitor all TCP/IP traffic.
Which packets will you be able to monitor?
a. All packets on your network
b. None of the packets on your network
c. Only packets sent from the IAS server
d. Only packets addressed to the IAS server
You are the administrator for your Windows 2000 network, which uses the TCP/IP protocol solely.
One of your Windows 2000 Professional computers has suddenly started having communication problems. From a command prompt, you type the netstat -a command.
What information will this command provide?
a. Ethernet stats
b. The contents of the routing table
c. Addresses and port numbers in numerical form
d. The status of all activity on the TCP and UDP ports on the computer
You are the administrator for a Windows 2000 network. The network uses the Network Address Translation (NAT) routing protocol to communicate with the Internet.
You are attempting to resolve an adjacency problem. To aid in finding the problem, you ensure that event logging in the Event Viewer is set to Log the maximum amount of information.
After locating and resolving the problem, how should you set event logging in the Event Viewer?
a. To the default of Log errors only
b. To the default of Disable event logging
c. To the default of Log errors and warnings
d. Leave as the default of Log the maximum amount of information
You are the administrator for an international company's Windows 2000
network. Your company has locations in
You configure a Windows 2000 Server computer as your Certificate Authority (CA). You need to implement a CSP.
Which CSP or CSPs can you use? (Choose all that apply.)
a. Schannel Cryptographic Provider
b. Microsoft DSS Cryptographic Provider
c. Microsoft Basic Cryptographic Provider
d. Microsoft Enhanced Cryptographic Provider
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is the Dynamic Host Configuration Protocol (DHCP) server.
At the DHCP server, you receive the following error message: 'This scope has an internal data conflict error.'
What should you do?
a. Run the Jetpack.exe utility
b. Stop and restart the DHCP service
c. Delete the scope and reconfigure it
d. Restore the DHCP database from backup
You are the administrator for your company's Windows 2000 Server network. The network contains 7 Windows 2000 Server computers and 60 Windows 2000 Professional client computers. Two server computers are configured to be Silent Routing Information Protocol (RIP) hosts.
While running tests on the network after implementing the Silent RIP hosts, you discover a problem. You verify the version of RIP that the Silent RIP hosts support.
What problem did you encounter?
a. You discovered that the RIP hosts were not receiving routes
b. You discovered that the host routes are not being propagated
c. You discovered that the RIP routers are not receiving expected routes
d. You discovered that the improper routes are being sent to the RIP routers
You administer a Windows 2000 network. Your network has three Windows 2000-based Windows Internet Name Service (WINS) servers. You want periodic backups of the WINS database on all WINS servers to occur automatically.
What should you do?
a. In the WINS console on all three WINS servers, right-click to select the server name, then select the Backup Database option
b. In the WINS console on all three WINS servers, configure the General properties of each WINS server to specify the default backup path
c. On all three WINS servers, use Windows Backup to schedule a regular backup of the contents of the System32WINS subdirectory
d. On all three WINS servers, configure the File Replication Service to copy the contents of the System32WINS subdirectory to another location on the disk
89. You are the administrator for a Windows 2000 network. The network contains 5 Windows 2000 Server computers and 45 Windows 2000 Professional client computers.
You are implementing a Certificate Authority (CA) hierarchy. While installing the subordinate CAs, you make an offline CA certificate request. You find that the CA is not certified.
What should you do?
a. Reissue all certificates in the hierarchy
b. Install a smart card reader on the CA computer
c. Reinstall the hierarchy CA by first installing the Root CA, and then Intermediate CAs, and finally the issuing Cas
d. Manually import the certificate using the Certification Authority MMC snap-in. After the certification authority's certificate has been issued by the parent CA, you can complete the installation
The Windows 2000 network you administer is configured to use demand-dial routing. The network uses all Windows 2000 Server computers and Windows 2000 Professional client computers. The network is configured to use Routing and Remote Access and static IP addresses.
You decide to implement a new router on the network with the same configurations as the current network routers. After the implementation, you test the new router. You discover that a demand-dial connection cannot be made.
What may be the cause of the problem?
a. The network is using MS-CHAP v2
b. The network is using IPX auto-static updates
c. There are not enough addresses in the static IP address pool
d. The calling router has been configured for certificate-based demand-dial routing
You are the administrator for your company's weconsult.com domain. Your network consists of a main office and two branch offices. The branches are connected to the main office by 256 Kbps leased lines. You have a single Domain Name System (DNS) zone. All DNS servers are at the main office. All servers are Windows 2000 Server computers. Your network is not connected to the Internet.
Users report that response times are extremely slow when they attempt to access resources on the intranet. When you monitor the network, you discover that DNS name resolution queries are generating heavy traffic across the Wide Area Network (WAN).
You want to accomplish the following goals:
Name resolution traffic across the WAN will be reduced.
Response times for name resolution queries will be reduced.
Administrative overhead for DNS maintenance will be minimized.
Current DNS namespace design will be maintained.
You take the following actions:
Create a new secondary DNS zone at each branch.
Use the primary zone at the main office as the primary zone for the secondary DNS server.
Configure the client computers to query the local DNS servers.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Name resolution traffic across the WAN will be reduced
b. Response times for name resolution queries will be reduced
c. Administrative overhead for DNS maintenance will be minimized
d. Current DNS namespace design will be maintained
You are the administrator for your company's Windows 2000 Server network. The network contains two Windows 2000 servers and 40 Windows 2000 Professional client computers that access the servers through a WAN. In addition to the 40 client computers, the company has a branch office in the same town with 10 Windows 2000 Professional client computers that access the servers through a dial-up connection. The company's domain is weconsult.com.
You need to configure the dial-up connection authentication methods for the 10 client computers. You want to configure the authentication methods for the dial-up connection to accomplish the following goals:
Use a certificate that is registered in the certificate store.
Verify expiration, signature, and root certificate authority of the certificate presented to your computer.
Only connect to servers in the domain weconsult.com.
Only allow certificates from the authority DST (UPS) RootCA.
Disconnect the connection if the server declines encryption.
You perform the following actions:
On the Security tab of the Properties dialog box for the connection, select Advanced (custom settings) and click the Settings button.
Select Optional encryption option.
Select Use Extensible Authentication Protocol (EAP), select Use Smart Card or other Certificate (encryption enabled), and click Properties.
Select Use certificate on this computer.
Check the Validate server certificate box.
Check the Connect only if server name ends with: box and type in weconsult.com.
Select DST (UPS) RootCA from the drop-down list of the Trusted root certificate authority box.
Which goal or goals are accomplished by these actions? (Choose all that apply.)
a. Use a certificate that is registered n the certificate store
b. Verify expiration, signature, and root certificate authority of the certificate presented to your computer
c. Only connect to servers in the domain weconsult.com
d. Only allow certificates from the authority DST (UPS) RootCA
e. Disconnect the connection if the server declines encryption
You are the administrator for a large dynamic IP internetwork that uses the Open Shortest Path First (OSPF) protocol. All servers on the network are running Windows 2000 Advanced Server.
You want to better manage the internal routers and Area Border Routers (ABRs) of the network. One of the steps you take in managing the areas and routers is to ensure that the ABRs are physically or logically connected to the backbone.
Which additional verification will this process include?
a. It will verify that there are not backdoor routers
b. It will verify that there are proper hop counts to the other areas
c. It will verify that the client computers within the area can communicate
d. It will verify that the servers within the backbone area can communicate
You administer your company's Windows 2000 domain. The company's network contains a Windows 2000 Server computer, named CertSvc, that is configured as the Enterprise Certificate Authority (CA).
You need to examine the life expectancy of issued certificates on CertSvc. Using the registry editor, you view the settings in the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesCertSvcConfigurationMAIN key, as shown below:
What is the lifetime of the issued certificates on CertSvc?
a. 1 year
b. 1 week
c. 3 years
d. 2 years
You must set up your company's DNS server so that it performs reverse DNS lookups. What is the best way to start?
a. Create a Forward Lookup Zone
b. Create a Reverse Lookup Zone
c. Create a Forward Lookup Zone with an in-addr.arpa domain suffix
d. Create a Reverse Lookup Zone without the in-addr.arpa domain suffix
Your company has a primary Domain Name System (DNS) server, DNS1.weconsult.com, that is heavily used. CPU utilization is consistently high. There are a lot of records stored on DNS1.
You suspect that some DNS queries are resulting in answers that exceed the limit for a single User Datagram Protocol (UDP) packets and want to find out if this is true.
What should you do?
a. Start System Monitor. On DNS1, monitor DNS:UDPMessageMemory counter
b. Start System Monitor. On DNS1, monitor coutners DNS:TCPResponsesSent and DNS:TCPResponsesSent/Sec
c. Use Network Monitor to analyze network traffic. Use nslookup on a separate computer to query for NS records on DNS1. Compare the number of UDP packets returned to DNS in response to your queries with the number you issued.
d. Use Network Monitor to analyze network traffic. From a client machine, ping host records that are stored on DNS1. Compare the number of UDP packets returned from DNS1 in response to your queries with the number of queries issued.
You are the administrator for your company's Windows 2000 Server network. The network contains two Windows 2000 servers and 40 Windows 2000 Professional client computers that access the servers through a WAN. In addition to the 40 client computers, the company has a branch office in the same town with 10 Windows 2000 Professional client computers that access the servers through a dial-up connection. The company's domain is weconsult.com.
You need to configure the dial-up connection authentication methods for the 10 client computers. You want to configure the authentication methods for the dial-up connection to accomplish the following goals:
Use a certificate that is registered in the certificate store.
Verify expiration, signature, and root certificate authority of the certificate presented to your computer.
Only connect to servers in the domain weconsult.com.
Only allow certificates from the authority DST (UPS) RootCA.
Disconnect the connection if the server declines encryption.
You perform the following actions:
On the Security tab of the Properties dialog box for the connection, select Advanced (custom settings) and click the Settings button.
Select Require encryption option.
Select Use Extensible Authentication Protocol (EAP), select Use Smart Card or other Certificate (encryption enabled), and click Properties.
Select Use certificate on this computer.
Check the Validate server certificate box.
Select DST (UPS) RootCA from the drop-down list of the Trusted root certificate authority box.
Which goal or goals are accomplished by these actions? (Choose all that apply.)
a. Use a certificate that is registered in the certificate store
b. Verify expiration, signature, and root certificate authority of the certificate presented to your computer
c. Only connect to servers in the domain weconsult.com
d. Only allow certificates from the authority DST (UPS) RootCA
e. Disconnect the connection if the server declines encryption
Your network has a requirement that zones in various DNS servers throughout are updated from a master DNS server. How can you configure a DNS server to provide such zone updates dynamically?
a. Enable TCP/IP filtering
b. Choose the Dynamic Update tab in the DNS console and select the Notify Button
c. Choose the Zone Transfers tab in the DNS console and select the Notify button
d. Choose the Zone Transfers tab in the DNS console and select the Dynamic Updates checkbox
You administer a small office Windows 2000 network. The network contains 3 Windows 2000 Server computers and 4 Windows 2000 Professional client computers. This network uses a single network interface, and uses DNS for name resolution.
Which network configuration is best for this small office network?
a. Use ICS, with a private IP address range of 192.168.0.0/24
b. Use NAT configured with an appropriate private IP address range
c. Use Microsoft Proxy Server to connect to the Internet, and use DHCP to allocate IP addresses. Use a separate VPN server to permit PPTP tunnel traffic.
d. Use Microsoft Proxy Server to connect to the Internet, and use DHCP to allocate IP addresses. Use a separate VPN server to permit L2TP/IPSec tunnel traffic.
You are the administrator for a Windows 2000 network. After researching connection types, you
decide to implement demand-dial routing from a branch office in
Why did you implement these protocols?
a. The two protocols can only be used with a PSTN
b. The two protocols allow for better user management
c. The two protocols can only be used with a RADIUS server
d. The two protocols can be used on a remote access server
You administer your company's Windows 2000 network. Your company has 5 branch offices and is continually growing. You want to properly manage your Internet connection's authentication and encryption processes.
You deploy a Public Key Infrastructure (PKI), and do not use Active Directory. You are only concerned with protecting requests to your network from the Internet. You want to install Certificate Services on a Windows 2000 Server computer.
Which Certificate Authority (CA) should you use?
a.
b. Stand-alone root CA
c.
d. Stand-alone subordinate CA
You are the administrator for a Windows 2000 Server network. You have a Dynamic Host Configuration Protocol (DHCP) Server which is configured to give DHCP clients all appropriate TCP/IP settings. You also have a Domain Name System (DNS) / Windows Internet Name Service (WINS) server.
You set up a Windows 2000 Server computer to be the dial-up connection server and want to configure the security for the dial-up connections. You want to accomplish the following goals:
Require the entry of a password upon connection.
Use the Windows logon and password for authentication.
Require the use of data encryption.
Automatically run a script upon connection.
You perform the following actions:
From the dial-up connection properties on the Security tab in the Security options section, select Typical (recommended settings) radio button.
For the Validate my identity as follows box, select Allow unsecured password.
Check the Require data encryption (disconnect if none) box.
In the Interactive logon scripting section, check the Show terminal windows box.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Require the entry of a password upon connection
b. Use the Windows logon and password for authentication
c. Require the use of data encryption
d. Automatically run a script upon connection
You are the administrator for your Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. You have Windows 2000 Professional clients, Windows NT Workstation 4.0 clients, and Windows 95 clients.
The IP address 200.10.20.20 is currently leased to one of your Windows 95 computers. You want to create a reservation for a Windows 2000 Professional computer to use this IP address.
What must you do first?
a. At the Windows 95 computer, run the ipconfig /release command
b. At the Windows 95 computer, run the winipcfg.exe command. Click the Release All button.
c. At the Windows 2000 Professional computer, run the ipconfig /release command
d. At the Windows 2000 Professional computer, run the winipcfg.exe command. Click the Release All button.
You are the administrator for your domain. Your domain contains Windows 2000 Server computers, Windows 2000 Professional computers, Windows NT 4.0 Workstation computers, Windows NT 3.5 Workstation computers, Windows 95 computers, Windows for Workgroups 3.11 computers, Windows 3.1 computers, LAN Manager 2.1 computers, and LAN Manager 1.0 computers.
You have installed the Windows Internet Name Service (WINS) on one of your Windows 2000 Server computers. You know that non-WINS clients must use a WINS Proxy Agent to participate in registering and resolving NetBIOS names. You set up a segment on your network, named segment Z, to place all your non-WINS clients.
Which computers should be placed on segment Z? (Choose all that apply.)
a. All Windows NT 4.0 Workstation computers
b. All Windows 3.1 computers
c. All Windows 95 computers
d. All LAN Manager 2.1 computers
e. All LAN Manager 1.0 computers
You administer your company's network. Your company wants to analyze ISO and TP4 communications on the MS Exchange Server computer on your network.
To analyze these communication types, you install Network Monitor on a Windows 2000 Server computer located on the same segment as the Exchange server.
How should you configure Network Monitor? (Choose two.)
a. Copy the ISO.dll and the TP4.dll files to the Netmon subdirectory
b. Copy the ISO.dll and the TP4.dll files to the Netmon Parsers subdirectory
c. Modify the parsers.ini file
d. Modify the netmon.ini file
e. Change the Temporary Capture directory
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Windows Internet Name Service (WINS) server. The WINS server has 2000 clients that register their names with it.
You use Network Monitor to monitor network traffic. Two WINS counters, Unique Registrations/sec and Queries/sec, are included in your captured data. You have noticed over the last few weeks that both of these counters have dramatically decreased. You have not added or removed any client computers.
What should you do?
a. Compact the WINS database
b. Scavenge the WINS database
c. Add a secondary WINS server
d. Add more RAM to the existing WINS server
e. Add a second processor to the existing WINS server
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. Currently you have two scopes configured on your DHCP server. These scopes contains global options, scope options, class options, and reserved options.
Which of these take precedence?
a. Global options
b. Scope options
c. Class options
d. Reserved options
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Windows Internet Name Service (WINS) server. All of your client computers use the WINS server for NetBIOS name registration.
You install a second WINS server at a branch office and set up replication between it and the main WINS server. You have a central computer that you use to monitor all network traffic using Network Monitor version 2. You want to be able to monitor WINS replication.
You install the wins.dll file on the computer you use for monitoring network traffic.
Which two files must you edit to support this? (Choose two.)
a. win.ini
b. wins.ini
c. tcpip.ini
d. parser.ini
You are the administrator for your company's Windows 2000 network. Your company has a main office and a branch office. You want to connect the branch office to the main office using demand-dial routing.
You set up the demand-dial router at both the branch office and the main office. While testing the router, you discover that the demand-dial interface has not been added to the protocol being routed.
How did you make this discovery?
a. The Auto-static updates were not working properly
b. The on-demand connection was not made automatically
c. From the branch office network, you were unable to reach any location at the main office network beyond the demand-dial router
d. From the branch office network, you received an error message when attempting to reach the demand-dial router at the main office
You are the administrator for a Windows 2000 network. The company consists of the corporate office
located in
From the
What may be the problem?
a.
The servers at the Daytona and
b. The servers at the Daytona and
c.
The PPP conversations are not configured
to access the servers at the Daytona and
d. The PPP conversations do not support conversations with the operating
systems on the servers at the Daytona and
What purpose would you have in enabling reverse DNS lookups?
a. Anyone with access to the DNS server can find a host name based on a subdomain
b. Anyone with access to the Web server can find a host name based on a subdomain
c. Anyone with access to the DNS server can find a host name based on an IP address
d. Anyone with access to the Web server can find a host name based on an IP address
Your company consists of a single Windows 2000 domain that spans multiple locations. The locations are connected over the Internet by using Routing and Remote Access. Resources are located on TCP/IP hosts on your network.
You implement Windows 2000 DNS servers on your network to facilitate name resolution for client access to the resources. You want to ensure that only secure dynamic updates are allowed when a zone transfer takes place.
What should you do?
a. Edit the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersUpdateSecurityLevel key. Change the value to 256.
b. Edit the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersUpdateSecurityLevel key. Change the value to 16.
c. Edit the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersUpdateSecurityLevel key. Change the value to 1.
d. Edit the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersUpdateSecurityLevel key. Change the value to 0.
You are the administrator for your company's Windows 2000 domain. The domain's network contains a Windows 2000 Server computer designated as the Enterprise Certificate Authority (CA).
Security is configured so that three groups have permissions: Authenticated Users, Domain Admins, and Enterprise Admins.
You want to limit the groups allowed to enroll for code signing certificates to a group of developers. The developers are a member of a special code signers group named CDSGN. You want to minimize the amount of administrative overhead with this task.
What should you do?
a. Add the CDSGN group, assigning the appropriate permissions
b. Add the CDSGN group, assigning the appropriate permissions. Delete all other groups from this template.
c. Add the CDSGN group, assigning the appropriate permissions. Remove any permissions given to all other groups.
d. Add the CDSGN group, assigning the appropriate permissions. Change any Allow permissions given to the other groups to Deny permissions.
You are the administrator for a Windows 2000 Server network. You have a Dynamic Host Configuration Protocol (DHCP) Server which is configured to give DHCP clients all appropriate TCP/IP settings. You also have a Domain Name System (DNS) / Windows Internet Name Service (WINS) server. You set up a Windows 2000 Server computer to be the dial-up connection server and want to configure the security for the dial-up connections. You want to accomplish the following goals:
Require the entry of a password upon connection.
Use the Windows logon and password for authentication.
Require the use of data encryption.
Automatically run a script named logon.scp upon connection.
You perform the following actions:
From the dial-up connection properties on the Security tab in the Security options section, select Typical (recommended settings) radio button.
For the Validate my identity as follows box, select Allow unsecured password.
Check the Require data encryption (disconnect if none) box.
In the Interactive logon scripting section, check the Run script box and type in filename logon.scp.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Require the entry of a password upon connection
b. Use the Windows logon and password for authentication
c. Require the use of data encryption
d. Automatically run a script named logon.scp upon connection
You are the administrator for your company's Windows 2000 domain. Your network consists of a Windows 2000 Server Primary Domain Controller (PDC) and 200 Windows 2000 Professional computers. The network connects to the Internet over a T1 line. The network uses all static IP addresses.
You set up a Routing and Remote Access Server, named R1, on your domain to allow access to your VPN resources.
Your company's salesmen use laptop computers while on the road. One of the salesmen can connect to the Internet through a local ISP and wants to connect to the company VPN. After configuring all of the appropriate components, he informs you that he cannot communicate with the VPN.
At a Windows 2000 Professional computer on the domain, you ping R1 and receive a reply. You then discover that another computer on the domain has the same IP address as R1.
Which utility can you use to discover this problem?
a. The RSH utility
b. The Netsh utility
c. The Telnet utility
d. The Ipconfig utility
You are the administrator for your company's Windows 2000 domain. You have a Windows 2000 Server computer that is your Domain Name System (DNS) server.
You want to view the properties of the DNS server, the DNS zones, and the resource records (RRs).
Which tool can you use?
a. DNScmd.exe
b. Netdom.exe
c. Nltest.exe
d. DNSstat.exe
e. Netdiag.exe
You are the administrator for your company's Windows 2000 domain, which contains three file servers as shown below. The FileSrvr1HR folder is a shared Encrypted File System (EFS) folder.
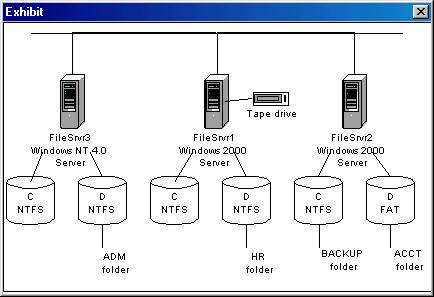
On FileSrvr1HR, you have a file named procedures.doc. On FileSrvr2ACCT, you have a file named policies.doc.
You copy procedures.doc to FileSrvr2ACCT, to FileSrvr2BACKUP, and to FileSrvr3ADM. You also back up procedures.doc to a tape drive connected to FileSrvr1.
You move policies.doc to FileSrvr2BACKUP. You then copy policies.doc to FileSrvr1HR.
What is the status of the two files? (Choose two.)
a. The procedures.doc file exists on FileSrvr2ACCT in decrypted form, on FileSrvr2BACKUP in decrypted form, on FileSrvr3ADM in decrypted form, and on the tape drive in encrypted form.
b. The procedures.doc file exists on FileSrvr1HR in encrypted form, on FileSrvr2ACCT in decrypted form, on FileSrvr2BACKUP in encrypted form, on FileSrvr3ADM in decrypted form, and on the tape drive in encrypted form.
c. The procedures.doc file exists on FileSrvr1HR in encrypted form, on FileSrvr2ACCT in decrypted form, on FileSrvr2BACKUP in decrypted form, on FileSrvr3ADM in decrypted form, and on the tape drive in encrypted form.
d. The procedures.doc file exists on FileSrvr2ACCT in decrypted form, on FileSrvr2BACKUP in encrypted form, on FileSrvr3ADM in decrypted form, and on the tape drive in encrypted form.
e. The policies.doc file exists on FileSrvr1HR in encrypted form and on FileSrvr2BACKUP in decrypted form.
Your company's network contains 8 Windows 2000 Server computers, 50 Windows 2000 Professional computers, and 25 Windows 95 computers.
You are the administrator for the network, and you have decided to install Windows Internet Name Service (WINS) for name resolution. You want the Windows 2000 computers to use the WINS server, then use broadcasts. However, you want the Windows 95 computers to use broadcasts, then use the WINS server.
What should you do? (Choose two.)
a. On the Windows 95 computers, change the node type to H-node
b. On the Windows 95 computers, change the node type to M-node
c. On the Windows 2000 computer, change the node type to P-node
d. On the Windows 2000 computers, change the node type to H-node
You administer your home network as part of your company's network. Your home network contains a Windows 2000 Server computer, a Windows 2000 Professional client computer, and a Windows NT 4.0 Server computer.
You discover that you failed to enable NAT addressing on the private interface. Which problem did this error cause?
a. Your network host did not filter the IP packets properly
b. Your network host did not statically assign name servers
c. Your network host did not dynamically assign name servers
d. Your network host did not receive IP address configurations
You administer a Windows 2000 network for your company. The company consists of a home office and many branch offices in surrounding states. The network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers. Remote access is enabled on the network. The branch offices dial into the home office server.
You receive a call from a user at a branch office that is having problems with the connection to the server at the home office. The user states that the connection was closed by the remote computer. You have the phone line checked for problems. A return call to you from the phone company informs you that the phone lines are working and clear.
What may be the problem?
a. The user account is not configured properly
b. The user account is configured to use dynamic IP addresses
c. The client computer is configured with the incorrect authentication protocol
d. The client computer cannot negotiate correctly with the modem on the remote access server at the selected speed
You are the administrator for a Windows 2000 network. Your internal DNS server is located behind a firewall. When you test your DNS server by using the Monitoring tab on the server's properties page, the DNS server passes the simple test but fails the recursive test.
What should you do?
a. Run ipconfig /registerdns
b. Delete the %systemroot%system32dnscache.dns file
c. Copy the %systemroot%system32dnssamplescache.dns file to %systemroot%dns, and overwrite the existing cache.dns file
d. Create a forward lookup zone for the root zoen. Name the forward lookup zone "."
You administer a small office network. The network contains 2 Windows 2000 Server computers and 10 Windows 2000 Professional client computers. The network uses Internet Connection Sharing and DNS.
You create a dial-up connection to an Internet Service Provider. You check the Enable on-demand dialing option in the properties for the dial-up connection.
What is the reason for this type of dial-up connection configuration?
a. To allow for name resolution on the Internet
b. To enable name resolution and address translation for the network
c. To allow other computers to access the Internet when the connection is already established
d. To enable the connection to automatically dial when a separate computer attempts to access the Internet
You are the administrator for a Windows 2000 Server network. The network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers. The Windows 2000 Server computer on the network uses Routing Information Protocol (RIP).
You have discovered that you are deploying variable length subnetting. What type of problem might this cause?
a. Host routes may not be propagated
b. The RIP hosts may send improper routes
c. Silent RIP hosts may not receive routes
d. The RIP routers may not receive expected routes
You are the administrator for your company's Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. Another Windows 2000 Server computer is your Windows Internet Name Service (WINS) server.
You want to provide fault tolerance for both the DHCP server and the WINS server. You want to accomplish this with the least amount of administrative overhead.
What should you do?
a. Configure the DHCP server to use option 44
b. Configure the DHCP server to use options 44 and 46
c. Purchase a third Windows 2000 Server and set it up as the secondary DHCP server and the secondary WINS server
d. Configure the current WINS server to be the secondary DHCP server. Configure the current DHCP server to be the secondary WINS server.
You are the administrator for a Windows 2000 network. The network consists of only Windows 2000 Server computers and Windows 2000 Professional client computers. The network contains 4 domains.
You are currently implementing a Public Key Infrastructure (PKI). You have created and implemented Group Policies and designated the recipients of the Group Policy. You have created certificate trust lists and would like the lists to be applied to recipients in Group Policies.
View the exhibit to determine the correct path for entering the PKI entries from the Group Policy object in the Group Policy snap-in to MMC. Choose the correct exhibit.
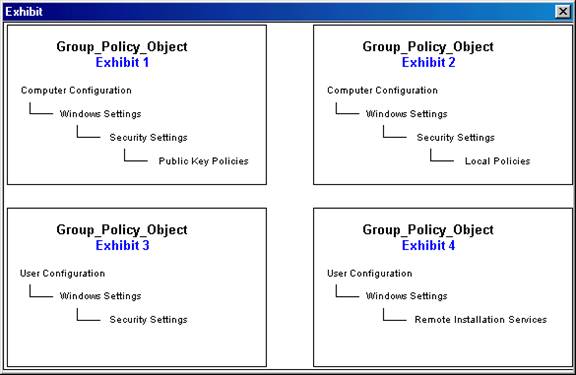
a. Exhibit1
b. Exhibit2
c. Exhibit3
d. Exhibit4
You administer a Windows 2000 network that consists of a domain, 2 Windows 2000 Server computers, and 25 Windows 2000 Professional client computers. One of the servers is configured to be a routing and remote access server in the domain.
The sales staff travels frequently and each person has recently been assigned a laptop to use. The sales staff will use the laptop to dial into the home office server and maintain their customer information.
One of the sales staff members is receiving an error message when attempting to dial in. The message states that the account does not have permission to dial in.
What must you do to resolve the problem?
a. Enable dial-in permissions for the user in Routing and Remote Access
b. Enable dial-in permissions for the user in Telnet Server Administration
c. Enable dial-in permissions for the user in Shared Folders in Computer Management
d. Enable dial-in permissions for the user in Local Users and Groups in Computer Management
You administer a Windows 2000 broadcast multi-access network. The network contains 12 routers and 10 Windows 2000 Server computers.
You want to assign Router Priorities so that at least one router is configured with a Router Priority of 1 or greater. What will this accomplish for the network?
a. It will ensure that the network will have two Designated Routers
b. It will ensure that the network will have three Designated Routers
c. It will ensure that the network will have a Designated Router and that adjacencies will be established
d. It will ensure that the network will not be assigned a Designated Router and that no adjacencies will be established
You are the administrator for a Windows 2000 Server network. You have a Dynamic Host Configuration Protocol (DHCP) Server which is configured to give DHCP clients all appropriate TCP/IP settings. You also have a Domain Name System (DNS) / Windows Internet Name Service (WINS) server. You set up a Windows 2000 Server computer to be the dial-up connection server and want to configure the security for the dial-up connections. You want to accomplish the following goals:
Require the entry of a secure password upon connection.
Use the Windows logon and password for authentication.
Require the use of data encryption.
Automatically run a script named logon.scp upon connection.
You perform the following actions:
From the dial-up connection properties on the Security tab in the Security options section, select Typical (recommended settings) radio button.
For the Validate my identity as follows box, select Allow unsecured password.
Check the Automatically use my Windows logon name and password (and domain if any) box.
Check the Require data encryption (disconnect if none) box.
In the Interactive logon scripting section, check the Run script box and type in filename logon.scp.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Require the entry of a secure password upon connection
b. Use the Windows logon and password for authentication
c. Require the use of data encryption
d. Automatically run a script named logon.scp upon connection
You are the administrator for your company's Windows 2000 domain. The network contains a Windows 2000 Server computer that uses the Network Address Translation (NAT) routing protocol. The network also uses Windows 2000 Professional client computers.
You decide to set up the NAT server to be a DHCP Allocator with the default values. What must you do to the client computers to automatically receive IP configurations?
a. Configure all Windows 2000 Professional client computers to use DNS
b. Configure all Windows 2000 Professional client computers to use OSPF
c. Configure all Windows 2000 Professional client computer as DHCP clients
d. Configure all Windows 2000 Professional client computers to use ICMP routers
You are the administrator for a Windows 2000 Server network. The network is configured to use EFS for file encryption.
Your supervisor asked that you ensure the private keys are protected from hackers. Your supervisor is also concerned with system crashes that may cause the private keys to become inaccessible.
How can you protect these keys?
a. Encrypt the RSA folder
b. Copy the entire RSA folder to a separate directory on a separate server computer
c. Export the certificate and private key to a floppy disk, and delete the private key from the computer
d. Encrypt the certificate and private key, copy the encrypted file to a separate server computer, and delete the private key from the main directory on the computer
You are the administrator for a Windows 2000 network. The network uses Network Address Translation (NAT) to communicate with the Internet.
You have deployed several applications to work with NAT. While testing one of the applications, you find that the payload of the application is not transferable.
How did you discover this problem?
a. The application returns an error message concerning public addresses not found
b. The application returns an error message concerning IP packets not transferring
c. The application can launch from a computer on the private network, but not from the NAT computer
d. The application can launch from the NAT computer, but not from a separate computer on the private network
You are the administrator for a Windows 2000 Server network. The network contains a Windows 2000 server that uses Point-to-Point Tunneling Protocol (PPTP). The PPTP server has an IP address of 204.29.70.1, and uses the default TCP ports.
You need to configure traffic filtering for the PPTP server to protect against attacks to the server. Although you have a Virtual Private Network (VPN), the PPTP server will never need access to it.
Using the Drop all packets except those that meet the criteria below filter action, which filters should you configure for the PPTP server? (Choose all that apply.)
a.
Input filters for Destination 204.29.70.1
and
b. Output filters for Source 204.29.70.1 and
c.
Output filters for Source 204.29.70.1 and
d. Input filters for Destination 204.29.70.1 and
You administer a Windows 2000 Server network for a company whose employees work from home. The network uses a tunnel server to connect to the Internet.
You must create a virtual private network (VPN) connection to tunnel users from their network to the corporate office network.
Which statement must be true for this to occur properly?
a. Users must have DNS enabled on their computers
b. Users must have DHCP enabled on their computers
c. Users must have static IP addresses configured on their computers
d. Users must have Internet Connection Sharing enabled on their computers
Your Windows 2000 Server network contains a Windows 2000 Server computer and 10 Windows 2000 Professional client computers. The Windows 2000 Server computer is your network's Windows Internet Name Service (WINS) server. All computers on your network use the TCP/IP protocol with the default settings.
A client computer is receiving the error message 'Network path not found' when attempting to resolve a name. You check the database for the name and cannot locate the name.
You then ping the name and receive the request timed out message. But when you ping the computer's IP address, you receive a reply.
What could be the problem?
a. The computer is not using WINS
b. You have typed the name incorrectly
c. The computer does not exist or is offline
d. You have typed the IP address incorrectly
You are the administrator for your company's Windows 2000 Server network. The network contains 8 Windows 2000 Server computers and 170 Windows 2000 Professional client computers. The company has six branch offices that access the network from different states in the country.
The network is configured to use EFS for file encryption. You have exported the private keys to a floppy disk for protection from hackers, and removed the keys from the computer.
Because of problems with the database, you need to decrypt a data file. What should you do?
a. Import the certificate from the floppy disk to the EFS root directory
b. Import the certificate from the floppy disk to the administrator's home directory
c. Import the certificate and private keys from the floppy disk to the recovery agent account
d. Import the certificate and private keys from the floppy disk to the WINNTSecurity directory
You are attempting to resolve a communication problem with a computer
named adm20 on a remote subnet. You can
successfully PING other computers on the same subnet as adm20. However, when you try to
Which of the following could be the problem? (Choose all that apply.)
a. Adm20 is offline
b. Adm20 has an incorrect DHCP Server
c. Adm20 has an incorrect default gateway
d. Your default gateway is configured incorrectly
You administer your company's Windows 2000 network. Your network consists of 5 Windows 2000 Server computers, 300 Windows 2000 Professional computers, and 10 UNIX servers. One of your Windows 2000 Server computers is your DNS server. The DNS zone is configured as an Active Directory integrated zone. The DNS zone is also configured to allow dynamic updates.
Users report that although they can access the Windows 2000 computers by host name, they cannot access the UNIX servers by host name.
What should you do?
a. Manually enter A (host) records for the UNIX servers in the zone database
b. Manually add the UNIX servers to the Windows 2000 domain
c. On the DNS server, manually create a HOSTS file that contains the records for the UNIX servers
d. Configure a UNIX computer to be a DNS server in a secondary zone
You enable DNS server and WINS server collaborations on the DNS client. How many of the following are true statements about the benefits of the collaboration? (Choose all that apply.)
a. The DNS server can pass the host part of the resolution of the DNS name to the WINS server
b. The WINS server will automatically update the DNS database with IP addresses that it receives from DHCP
c. IF a DNS client host is moved to another subnet , DNS will get the correct IP address from the WINS server database
You are beginning the implementation of a new Windows 2000 network for your company. You have decided to use all Windows 2000 Server computers with Windows 2000 Professional client computers.
The network will be configured with Routing and Remote Access, and you will create an OSPF internetwork.
You are in the process of determining the proper OSPF router types to use with the network. You want to implement a router that exchanges routes with sources outside of the OSPF autonomous system.
Which type of OSPF router will you implement?
a. Internal Router
b. Backbone Router
c. AS Boundary Router
d. Area Border Router
You are the administrator for a company called We Consult. We Consult has a Windows 2000 Server network. The network contains two Windows 2000 servers and 40 Windows 2000 Professional client computers that access the servers through a WAN. In addition to the 40 client computers, the company has several freelance consultants who need access to the company's network through a dial-up connection. The company's domain is weconsult.com.
You need to configure your dial-up connection authentication methods for consultants. The consultants will need to use their Windows 2000 account for your network. You want to configure the authentication methods for the dial-up connection to accomplish the following goals:
Disconnect the connection if the server declines encryption.
Use a certificate that is registered in the certificate store.
Verify expiration, signature, and root certificate authority of the certificate presented to your computer.
Only connect to servers in the domain weconsult.com.
Only allow certificates from the authority DST (UPS) RootCA.
Allow the consultants to log on using their Windows 2000 user account configured on your network.
You perform the following actions:
On the Security tab of the Properties dialog box for the connection, select Advanced (custom settings) and click the Settings button.
Select Require encryption option.
Select Use Extensible Authentication Protocol (EAP), select Use Smart Card or other Certificate (encryption enabled), and click Properties.
Select Use certificate on this computer.
Check the Validate server certificate box.
Check the Connect only if server name ends with: box and type in weconsult.com.
Select DST (UPS) RootCA from the drop-down list of the Trusted root certificate authority box.
Which goal or goals are accomplished by these actions? (Choose all that apply.)
a. Disconnect the connection if the server declines encryption
b. Use a certificate that is registered in the certificate store
c. Verify expiration, signature, and root certificate authority of the certificate presented to your computer
d. Only connect to servers in the domain weconsult.com
e. Only allow certificates from the authority DST (UPS) RootCA
f. Allow the consultants to log on using their Windows 2000 user account configured on your network
You are the administrator for a network that contains several Windows 2000 Server computers. Encrypting File System (EFS) is configured on one of the servers for purposes of protecting data files.
You want to export the recovery keys to a location on the same server computer. You accomplish this using the Certificate Export wizard. You now need to fully protect the exported file.
What should you do to ensure protection?
a. Encrypt the exported file and move the file to a separate server
b. Copy the exported file to a separate directory on the computer. Encrypt the directory to which you copied the file.
c. Encrypt the RSA folder on the computer. Create a copy of the encrypted file on a floppy disk, and store the floppy disk in a secure location within the office.
d. Move the exported file from the server to a floppy disk. Create a backup copy of the floppy disk, and store one floppy disk in a secure location within the office and one floppy disk in an offsite location
You are the administrator for a Windows 2000 network. The network contains a Windows 2000 Server computer with Network Address Translation (NAT) enabled.
You are attempting to resolve network problems and found that the DNS proxy was not enabled.
Which problem might this resolve?
a. A problem resolving names for your private network hosts
b. A problem resolving IP addresses for your private network hosts
c. A problem with dynamic IP addressing for your private network hosts
d. A problem with automatic IP addressing for your private network hosts
Your Windows 2000 network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers. The network uses a Routing and Remote Access server.
As the administrator for the network, you decide to configure the remote access server to allow a dial-in connection to access more than one line. You decide to accept the default for the Bandwidth Allocation Protocol settings. The default setting is to reduce a Multilink connection by one line if the lines fall below 50% capacity for a period of 2 minutes.
While testing Multilink, you determine that the Multilink and BAP settings are not being enforced. What must you do to resolve this problem?
a. Enable Multilink and BAP
b. Enable the Restrict maximum session to property
c. Enable the Extensible Authentication Protocol property
d. Enable the Require BAP for dynamic Multilink requests property
You are the administrator for your company's small network. The network contains three Windows 2000 Server computers and 20 Windows 2000 Professional client computers.
You have installed network address translation (NAT) so that all computers can share a single connection to the Internet. While testing, you discover that the network address translation computer is not configured properly for name resolution.
Which problem might have been caused by this improper configuration?
a. The NAT computer is not properly filtering packets
b. The NAT computer is not properly translating packets
c. The network is not receiving IP address configurations
d. The network is not able to resolve names to IP addresses
You administer a Windows 2000 network. You configure a Windows 2000 Server computer to act as a router between your network and the Internet.
After installing the Open Shortest Path First (OSPF) routing protocol, you check the Enable autonomous system boundary router checkbox in the OSPF Properties dialog box.
Why did you perform this action?
a. To begin the configuration of a router
b. To configure a non-broadcast multiple access network type
c. To configure a virtual interface for the Internet interface
d. To begin the configuration of External Routing route filters
Within two weeks your company will secure several domain names which must then be added to a newly-installed DNS service on your network server. Before this time, you want to be sure that the DNS service is functioning correctly. What is the best way to test the DNS service without compromising your ability to add the new domain names when they arrive?
a. Use the DNS console and add a zone and host record for an imaginary domain such as mytest.com. Make sure the host record contains the IP address of a valid host. Use the ping utility with mytest.com as the command line argument and see if it successfully returns the IP address of the host.
b. Use the DNS console and add a zone and host record for an imaginary domain such as mytest.com. Make sure the host record does not contain the IP address of a valid host. Use the ping utility with mytest.com as the command line argument.
c. Use both the ping utility and the ipconfig utility to test the DNS service. The ping utility can be used to insure that the DNS service IP address responds. The ipconfig utility can be used to add a temporary domain name to the DNS server.
d. Use both the ping utility and the ipconfig utility to test the DNS service. The ping utility can be used to insure that the DNS service IP address responds. The ipconfig utility can be used to make sure that the TCP/IP settings for the DNS service are correct.
The DNS server on your network is not performing as well as you think it could. You think there are resource records that are no longer in use and this is causing the poor performance. What can you do to fix this?
a. From the DNS console, select Recover unused resource records from the Action menu
b. From the DNS console, select 'Scavenge stale resource records' from the Action menu
c. From the command line, run the ipconfig utility with a command line argument 'clean'
d. From the command line, run the netstat utility with a command line argument 'optimize'
You are the administrator for a Windows 2000 network. The network contains a Windows 2000 Server computer configured as the Enterprise Certificate Authority (CA).
While performing monthly network maintenance, you determine that the CA certificate will expire within one week.
Which action should you take to ensure the CA server will continue working properly?
a. No action necessary. When the certificate expires, the CA will automatically issue another certificate to replace it
b. Stop the Certificate Services service. From the Certification Authority console, select the Renew CA Certificate option.
c. Remove the c:WINNTSystem32certsrv directory and reboot the CA server. When the CA re-initializes, the certificate expiration date will reset.
d. Stop and restart the Certificate Services service. Because the expiration time is below two weeks, another certificate will be issued to replace the expired on automatically
You manage a network of 1,500 Windows 2000 Professional computers, all configured to use Dynamic Host Configuration Protocol (DHCP). You decide to implement Windows Internet Name Service (WINS) on your network for NetBIOS name resolution.
You set up a Windows 2000 Server computer and install the WINS service. You want to configure the client computers to use WINS?
What is the easiest way to do this?
a. Configure the DHCP server with the 138 UDP/netbios option only
b. Configure each client with the address of the WINS server manually
c. Configure the DHCP server with options 44 WINS/NBNS and 46 WINS/NBT
d. Configure the DHCP server with the 137 TCP/netbios and 138 138 UDP/netbios option
You administer your company's Windows 2000 network. To facilitate connections for remote administration, you install Routing and Remote Access on a Windows 2000 domain controller.
You want to accomplish the following goals:
Only administrators will have dial-up access.
Dial-up connections will be accepted only from 6 p.m. to 6 a.m. Wednesday through Friday.
Connections will be forcibly disconnected after 15 minutes of inactivity.
All connections will encrypt all communications.
Connections will be limited to two hours.
You take the following actions:
You set the level or levels of encryption to No Encryption or Basic.
You add the DomainAdmins group to the Routing and Remote Access Policy.
You configure the dial-in properties as shown below:
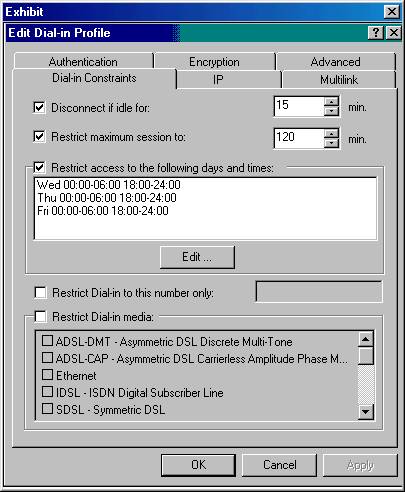
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Only administrators will have dial-up access.
b. Dial-up connections will be accepted only from 6 p.m. to 6 a.m. Wednesday through Friday.
c. Connections will be forcibly disconnected after 15 minutes of inactivity.
d. All connections will encrypt all communications.
e. Connections will be limited to two hours.
You administer a Windows 2000 network for your company. The network consists of 4 Windows 2000 Server computers, 20 Windows 2000 Professional client computers, and 10 Windows 98 second edition client computers. The network also uses a DHCP server and DNS server.
Your immediate supervisor requested that you install and enable Network Address Translation (NAT) on one of the server computers. What may be the purpose for your supervisor making this request?
a. To provide static IP addresses for the network
b. To provide dynamic IP addresses for the network
c. To provide a permanent connection to the Internet for the network
d. To provide IP address translation, provide addressing, and provide name resolution services
Your company needs to send highly sensitive data over the Internet.
As the administrator, you have the option to implement one of the following authentication protocols:
Extensible Authentication Protocol - Transport Layer Security (EAP-TLS)
Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2)
Microsoft Challenge Handshake Authentication Protocol version 1 (MS-CHAP v1)
What is one reason that one of these three protocols would provide the security needed in this situation?
a. To implement an authentication protocol that uses encapsulation
b. To implement an authentication protocol that uses data encryption
c. To implement an authentication protocol that uses data compression
d. To implement an authentication protocol that uses plain text passwords
You are the administrator for a Windows 2000 network. The network contains four Windows 2000 server computers that use IPSec to secure the network communication.
While using IPSec Monitor, you determine that hard security associations (SAs) are not being established between computers. After running IPSec Monitor on one of the computers, you find that a soft SA exists between two of the computers. You also find that the security setting for the SA is set to 'None'.
You stop all traffic until the SA times out and verify the SA is gone. Then you start the traffic again. A hard SA is automatically established. What must you do to delete all soft SAs?
a. Delete the SAs from the IPSec Monitor
b. Stop all traffic
c. Restart the policy agent
d. Refresh the IPSec Monitoir
e. Reboot the server computers
154. You are the administrator for your company's network. Your network consists of 100 Windows 2000 Professional computers, 15 Windows NT Workstation 4.0 computers, 10 Windows 98 computers, and 3 Windows 2000 Server computers, all using TCP/IP over an Ethernet backbone.
Your company, Anonymous Software, has recently been purchased by Friendly Software. Friendly Software is attached to your network by a T1 line and has a NetWare bindery-based file server to which all computers on your network need access.
You have been asked to complete the appropriate administrative task(s) to accomplish this goal. You want to accomplish this goal with as little administrative overhead as possible. Since security is a major concern, you have been asked to implement user-level security.
Which action should you take?
a. On all computers on your network, install and configure Client Service for NetWare. Each client will connect directly to the NetWare bindery-based file server at Friendly Software.
b. On one Windows 2000 Server computer, install and configure Client Service for Netware. All clients will use the Windows 2000 Server computer to connect to the NetWare bindery-based file server at Friendly Software.
c. On one Windows 2000 Server computer, install and configure Gateway Service for NetWare. All clients will use the Windows 2000 Server computer to connect to the NetWare bindery-based file server at Friendly Software.
d. On one Windows 2000 Professional computer, install and configure Client Service for NetWare. All clients will use the Windows 2000 Professional computer to connect to the NetWare bindery-based file server at Friendly Software.
You are the administrator for your company's Windows 2000 network. The network contains a Windows 2000 Server computer configured as the Enterprise Certificate Authority (CA).
A network user requested the ability to perform revocation checking tasks through a Web browser. You implement the change for the user, configuring the appropriate permissions. The user then informs you that revocation checking is not working.
After examining the user's client computer, you discover that he uses Netscape Communicator 4.0 as the Web browser.
What must you do?
a. From a command prompt on the CA server, type: certutil -s SetReg PolicyRevocationType +AspEnable
b. From a command prompt on the CA server, type: certutil -SetReg PolicyRevocationType +AspDisable
c. From a command prompt on the user's computer, type: certutil -SetReg PolicyRevocationType +AspEnable
d. From a command prompt on the user's computer, type: certutil -SetReg PolicyRevocationType +AspDisable
You are the administrator for a Windows 2000 Server network. The network contains a Windows 2000 native-mode domain. The server is set to use the default remote access policy.
You are setting up new user accounts on the domain. You want the Remote Access Permissions for the user accounts to be set to automatically allow access.
What should you do to ensure this setting?
a. Do nothing. Allow access is the default setting
b. Change the setting from Deny access to Allow access
c. Change the setting from Deny remote access permission policy to Allow access
d. Change the setting from Control access through Remote Access Policy to Allow access
You are the administrator for your company's Windows 2000 network that uses the Network Address Translation (NAT) routing protocol to connect to the Internet. You enable the DNS Proxy and DHCP Allocator NAT components to provide a DNS server and provide IP address configuration information to the network.
Because of company growth, you decide to add a second scope of IP addresses. What must you do to the NAT routing protocol to accomplish this task?
a. Disable the DNS proxy
b. Disable the DHCP allocator
c. Check the Translate TCP/UDP headers option on the properties page of the Internet interface
d. Remove the check from the Public interface connected to the Internet option on the properties page of the Internet interface
You are the administrator for your Windows 2000 domain. You currently use Internet Protocol Security (IPSec) to secure traffic and to prevent attacks on your data.
You are concerned that a computer on your network is compromising security and want to know whether it is using a local policy or a policy from the Active Directory.
Which tool should you use?
a. Event Viewer
b. IPSec Monitor
c. Network Monitor
d. Active Directory Sites and Services
You implement and administer a Windows 2000 network. The network uses Windows 2000 Server computers and Windows 2000 Professional client computers. The network also has Internet Connection Sharing enabled.
Which statement or statements are true about this network?
a. Configuration of DNS is not allowed
b. Configuration of DHCP is not allowed
c. Configuration of the PPTP protocol is not allowed
d. Configuration of Network Address Translation is not allowed
You are the administrator for a Windows 2000 Server network. The network consists of the main office,
located in
Your company has decided to implement a new policy that involves using high levels of security on the network. One area of this security will include setting the strongest level of MPPE data encryption possible. The encryption level is currently set to Strong encryption (56-bit).
What should you do to implement the highest level of data encryption?
a. Set the encryption level to No encryption
b. Set the encryption level to Basic encryption (40-bit)
c. Set the encryption level to Strongest encryption (128-bit)
d. Do nothing. Strong encryption is the strongest level of encryption eavailable
You are the administrator for your company's Windows 2000 domain. You have a Windows 2000 Server computer that is your Domain Name System (DNS) server. It is not configured to perform dynamic updates for the reverse lookup zone because you do not want these to take place at this name server.
On a DNS client you are receiving error messages stating the PTR records could not be registered.
What should you do?
a. On the DNS client, edit the
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersInterfaces<name of the interface> registry key.
Add the DisableReverseAddressRegistrations entry with a value of 1.
b. On the DNS server, edit the
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersInterfaces<name of tservererface> registry key.
Add the DisableReverseAddressRegistrations entry with a value of 1.
c. On the DNS client, edit the
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersInterfaces<name of the interface> registry key.
Add the DisableDynamicUpdate entry with a value of 1.
d. On the DNS server, edit the
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersInterfaces<name of the interface> registry key.
Add the DisableDynamicUpdate entry with a value of 1.
You are the administrator for your company's Windows 2000 network. The network uses Certificate Authorities (CAs) to ensure security of data files.
While performing maintenance on the CA, you discover that one of the CAs has been compromised. Which steps must you take to repair the CA? (Choose all that apply.)
a. Repair the cause of the compromise
b. Revoke the certificate of the compromised CA
c. Publish a new CRL with the revoked CA certificate
d. Inform the affected users and administrators of the compromised CA
e. Remove the compromised CA from Trusted Root Certification Authorities stores and CTLs
You are the administrator for your company's network. Your company includes a main office in Charlotte and three branch offices in surrounding states. You are currently nearing completion of the project to upgrade the network's server computers from Windows NT 4.0 Server to Windows 2000 Server. You have completed the upgrade of the network's Windows NT 4.0 Workstation computers to Windows 2000 Professional computers.
You decide to replace the certificate server that currently runs on a Windows NT 4.0 Server computer with a Windows 2000 Certificate Authority (CA). You plan to use the current policy module from the Windows NT server.
How can you accomplish this task with minimal administrative overhead?
a. Copy the policy module from the NT 4.0 Server computer to the Windows 2000 Server computer
b. Export the CA settings from the NT 4.0 Server computer and import the settings to the Windows 2000 Server computer
c. Using Regsvr32, register the policy module DLL file. Using the CA console, select the current policy module.
d. Recreate the current policy on the Windows 2000 Server computer by creating a custom policy module with the same settings
You are the administrator for a Windows 2000 network. The network uses Windows 2000 Server computers and Windows 2000 Professional client computers. Network address translation (NAT) is enabled on the network, along with DHCP.
You want to configure the IP addresses for a NAT interface that connects to the Internet. You have the following IP address configuration:
IP Addresses:
200.100.100.212
200.100.100.213
200.100.100.214
200.100.100.215
Subnet Mask:
255.255.255.252
Which steps should you take, from Routing and Remote Access, to accomplish this task? (Choose all that apply.)
a. From the Address Pool tab, click Add
b. Enter 255.255.255.252 in the Mask field
c. Enter 200.100.100.212 in the Start Address field
d. From IGMP, right-click the interface to configure, and click Properties
e. From Network Address Translation, right-click the interface to configure, and click Properties
You work from your home for your company. You must have a network set up in your office to properly perform your job. You use TCP/IP to connect your Windows 2000 Server computer to your Windows 2000 Professional computer on your network.
You want the computers on your network to share an Internet connection that is configured on your Windows 2000 Server computer. You install Internet connection sharing on the server computer. After enabling Internet connection sharing, you discover that you must reestablish the TCP/IP connections on the network. Why are the connections for your network lost?
a. Because you need to configure new IP address configurations for the network
b. Because Internet connections are lost each time new software is installed on a network
c. Because Network Address Translation is required after enabling Internet connection sharing
d. Because the network adapter connected to the network is given a new static IP address configuration
You administer a Windows 2000 Server network. The network contains a Windows 2000 server and 20 Windows 2000 Professional client computers.
The Information Technology (IT) manager of your company has requested that he have priority on server resources when resources are limited. You need to configure the server to allow the IT manager priority allocation of bandwidth when needed.
What can you use to accomplish this?
a. Network Monitor
b. QoS Admission Control
c. Windows Media Performance
d. Telnet Server Administration
e. Subnet Bandwidth Management
Your company has informed you of the need for security on the Windows 2000 network of which you are the administrator. The network uses Windows 2000 Server computers and Windows 2000 client computers. Routing and Remote Access is enabled on the server.
You decide to implement EAP-Transport Level Security (EAP-TLS) and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP) version 2 on the network.
Which feature is common to these protocols?
a. callback
b. caller-ID
c. mutual authentication
d. secure user authentication
You are the administrator for your company's Windows 2000 Server network. The network contains 3 Windows 2000 Server computers and 25 Windows 2000 Professional client computers.
You decide to use Network Address Translation (NAT) to connect the network to the Internet. After installing the NAT protocol, you perform the following tasks:
Open Routing and Remote Access.
Open the Properties dialog box for NAT.
Select the Address Assignment tab.
Check the Automatically assign IP addresses by using DHCP option.
Close Routing and Remote Access.
What did you accomplish with these tasks?
a. You enabled NAT
b. You installed DHCP
c. You configured dynamic IP addresses
d. You enabled name resolution inbound traffic
You are the administrator for a Windows 2000 domain. The domain's network contains 7 Windows 2000 Server computers. One of the server computers is configured with EFS for file encryption for the domain.
You decide to export the private keys to removable media. You use the Certificate Export wizard to accomplish this, specifying that the recovery keys be deleted if the export is successful.
Where will the wizard store the keys?
a. In a .pfx file
b. In a .fxp file
c. In a .xep file
d. In a .rxc file
Your company has placed you in control of creating the PKI certificate services needed for your Windows 2000 network. The network contains 6 domains, 5 Windows 2000 Server computers, and 300 Windows 2000 Professional client computers.
You have identified the future applications that require digital certificates. You now need to determine the certificate services needed.
Which factors must you consider in this creation process? (Choose all that apply.)
a. Purpose of certificates
b. Location of certificates
c. Certification types to be issued
d. Number of entities requiring certificates
e. Location of entities requiring certificates
You are the administrator for a Windows 2000 network. Currently, your network consists of a Windows 2000 Server computer and 20 Windows 2000 Professional client computers. The server and client computers are on a single subnet.
Because of company growth, you decide to add a second subnet for 10 new Windows 2000 Professional computers. Your company purchases a Windows 2000 Server computer to serve as the router between the two subnets.
Currently, the network has a 10 Mbps Ethernet backbone, and traffic on the network is at an all-time high. You want to upgrade to a 100 Mbps Ethernet network, but the company's budget does not allow it at this time.
You decide to implement RIP version 2 on the new Windows 2000 Server computer. What is one reason for making this decision?
a. To ensure the use of broadcasts in the routing process
b. To ensure broadcasts are not used in the routing process
c. To ensure route tags are not used in the routing process
d. To ensure the subnet mask is not sent in the routing process
You are the administrator for a Windows 2000 domain. The network contains a Windows 2000 Server computer with the Network Address Translation (NAT) routing protocol installed.
You install NAT editors for the following protocols:
FTP
PPTP
ICMP
NetBIOS over TCP/IP
How are these editors used on the network?
a. To configure proxy software for each protocol
b. To allow you to edit the NAT options for each protocol
c. To modify and recalculate the fields in the IP, TCP, and UDP headers
d. To translate and adjust the payload beyond the IP, TCP, and UDP headers
You are the administrator of a Windows 2000 network that uses TCP/IP as its only network protocol. Your company has decided to use IPSec to secure all data transmissions on the intranet and with the Internet.
You want the plan you implement to offer user authentication, mutual computer authentication, encryption, data authentication, and data integrity. You want to implement this plan with the least amount of administrative overhead.
Which should you do?
a. Implement Layer Two Tunneling Protocol (L2TP)
b. Implement AH nested with L2TP
c. Implement ESP in combination with AH
d. Implement ESP in combination with AH, nested with L2TP
174. You are the administrator for a Windows 2000 Server network. You have a Dynamic Host Configuration Protocol (DHCP) Server which is configured to give DHCP clients all appropriate TCP/IP settings. You also have a Domain Name System (DNS) / Windows Internet Name Service (WINS) server. You set up a Windows 2000 Server computer to be the dial-up connection server and want to configure the security for the dial-up connections. You want to accomplish the following goals:
Require the entry of a password upon connection.
Use the Windows logon and password for authentication.
Require the use of data encryption.
Automatically run a script upon connection.
You perform the following actions:
From the dial-up connection properties on the Security tab in the Security options section, select Typical (recommended settings) radio button.
For the Validate my identity as follows box, select Allow unsecured password.
Check the Automatically use my Windows logon name and password (and domain if any) box.
Check the Require data encryption (disconnect if none) box.
In the Interactive logon scripting section, check the Show terminal windows box.
Which goal or goals are accomplished from these actions? (Choose all that apply).
a. Require the entry of a password upon connection
b. Use the Windows logon and password for authentication
c. Require the use of data encryption
d. Automatically run a script upon connection
175. You are the administrator for your Windows 2000 network. You have a Windows 2000 Server computer that is your Dynamic Host Configuration Protocol (DHCP) server. Another Windows 2000 Server computer is your Domain Name System (DNS) server.
You want the DHCP server to configure the DNS server setting for all DHCP clients.
What should you do?
a. Use DHCP option 6
b. Use DHCP option 44
c. Use DHCP option 46
d. Use DHCP option 44 and 46
Answer Key:
D
C
A,D
D
C
B
D
B
C
A,B,C,D
D
A,E
B,D
D
D
A
D
B
C
C
A
B
C,D
A,C
A,B,C
B
D
B
B
C
B
C
D
A,D
A
B
A,B,D
A
D
D
B,D,E
C
C
C
D
A
C,D
C,D
A,B,C,D
C
A
C
A,C,D
A
C
B
C
B
C
C
D
C
B
A,B,C
A
D
A,D
D
A
B
D
B
B
A
C
D
D
B
B
A,D
C,D
D
D
C
A,B,C
A
A
A
D
C
A,B,D
A,B,C,D
A
D
B
C
A,B,D,E
C
A
D
B
A,C
B
B,E
B,C
E
D
C,D
C
A
C
A
B
A,C,D
D
A
C,E
B,D
D
D
C
D
D
D
A
A
C
B,C,D
C
C
D
C,D
D
B
C
A,C
A
A,B
C
A,B,C,D,E
D
A
A
D
D
A
B
B
C
A,B,C,E
D
B
C
A
A
D
B
A
A,B
B
A
A,B,C,D,E
C
A,B,C,E
D
B
C
A
A
A,C,D,E
B
D
A
A,B,C
A
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1438
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2026 . All rights reserved