| CATEGORII DOCUMENTE |
| Asp | Autocad | C | Dot net | Excel | Fox pro | Html | Java |
| Linux | Mathcad | Photoshop | Php | Sql | Visual studio | Windows | Xml |
If your organization is an
In the sections that
follow, the components of an
A Hotspot Service Provider (
The following illustration depicts the components of an
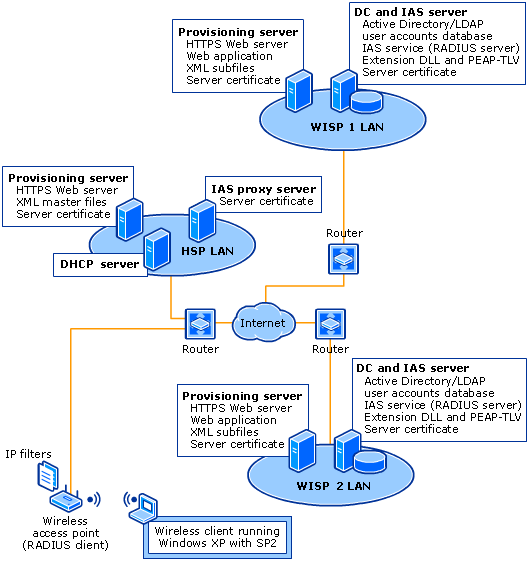
Components of an
This configuration consists of the following components.
A computer running Windows XP Home Edition with
SP2, Windows XP Professional with SP2, or Windows XP Tablet PC
Edition with SP2. The wireless client connects to the
The wireless access point is configured as a RADIUS client
to the IAS proxy server deployed on the
Support for the IEEE standard 802.1X authentication.
Support for Wi-Fi Protected Access (WPA) is preferred
The ability to implement client isolation by applying IP filters to the connection with the client.
Support for RADIUS authentication and RADIUS accounting, including:
Support for the Class attribute as defined in RFC 2865, "Remote Authentication Dial-in User Service (RADIUS)," to allow session correlation for RADIUS authentication and accounting records. For session correlation, when you configure RADIUS accounting at your IAS server or proxy, you must log all accounting data that allow applications (such as billing applications) to query the database, correlate related fields, and return a cohesive view of each session in the query results. At a minimum, to provide session correlation, you must log the following IAS accounting data: NAS-IP-Address; NAS-Identifier (you need both NAS-IP-Address and NAS-Identifier because the access server can send either attribute); Class; Acct-Session-Id; Acct-Multi-Session-Id; Packet-Type; Acct-Status-Type; Acct-Interim-Interval; NAS-Port; and Event-Timestamp.
Support for accounting interim requests, which are sent periodically by some access servers during a user session, that can be logged. This type of request can be used when the Acct-Interim-Interval RADIUS attribute is configured to support periodic requests in the remote access profile on the IAS server. The access server, in this case a wireless access point, must support the use of accounting interim requests if you want the interim requests to be logged on the IAS server.
Support for IP address range filtering.
Support for dynamic retransmit timeout (RTO) estimation or exponential backoff to handle congestion and delays in a wide area network (WAN) environment.
In addition, there are some filtering features that the access points must support to provide enhanced security for the network. These filtering options include:
DHCP filtering. The access point must filter on IP ports to prevent the transmission of DHCP broadcast messages in the instance that the client is a DHCP server. The access point must block the client from sending IP packets from port 68 to the network.
DNS filtering. The access point must filter on IP ports to prevent a client from performing as a DNS server. The access point must block the client from sending IP packets from port 53 to the network.
IP filters that isolate client computers connecting as
guest are configured in the remote access policy on the
The router must provide multiple ports for connection to
access points, the
The
The
The Internet Information Services (IIS) or third-party Web server must be deployed with HTTPS.
The domain name of the WISP. For example, if Microsoft Corporation is the WISP, the domain name is "microsoft.com."
The friendly name of the WISP. For example, Microsoft Corporation.
The TTL for the XML master
file. When client computers connect to the
The list of URLs that point to XML subfiles. The XML subfiles are located on the WISP provisioning server for which the XML master file was created. Only HTTPS URLs are supported for use within the XML schema, and by WISP provisioning servers. The name of the XML schema described in the subfile is included, as is the version number for the subfile. Possible subfile names include: Signup, SSID, EAP, Location, and Help. For more information, see "XML Schemas" in this paper.
For server authentication to client computers, the
provisioning server must maintain a valid certificate in its certificate store.
The certificate must contain the Server Authentication purpose in Enhanced Key
Usage (EKU) extensions and be issued by a public certification authority (CA),
such as Verisign or Thawte, that is trusted by client computers connecting to
the
The
The IAS proxy server must be a computer running Windows Server 2003, Standard Edition with Service Pack 1 (SP1); Windows Server 2003, Enterprise Edition with SP1; or Windows Server 2003, Datacenter Edition with SP1; and Internet Authentication Service (IAS). IAS is the Microsoft implementation of a Remote Authentication Dial-In User Service (RADIUS) proxy and server.
The IAS proxy functions both as an IAS proxy and as an IAS server. The IAS proxy server is configured to locally process connection requests for users that authenticate as guest, and to forward non-guest authentication and accounting requests to the IAS servers located at individual WISPS based on the realm name configuration specified in Connection Request Policies in the IAS console.
On the IAS proxy, the IAS servers at each WISP are added to
a remote RADIUS server group, with a minimum of one remote RADIUS server group
created for each WISP. Because Windows Server 2003, Standard Edition,
permits the creation of only two remote RADIUS server groups, an
For server authentication to client computers, the
provisioning server must maintain a valid certificate in its certificate store.
The certificate must contain the Server Authentication purpose in Enhanced Key
Usage (EKU) extensions and be issued by a public certification authority (CA),
such as Verisign or Thawte, that is trusted by client computers connecting to
the
The DHCP server must be able to assign valid public IP addresses to computers accessing the network through the wireless access points.
The WISP 1
The WISP provisioning server is configured with the following components.
Like the
The WISP Web server is configured with an account processing Web application. When a customer uses the sign-up wizard on the client computer to create and pay for an account, the customer enters data, such as name, address, and credit card information, that is converted to an XML document and sent to the WISP provisioning server.
The account processing Web application on the provisioning server must be capable of accepting and processing the XML documents containing the user data. For example, the account processing Web application must dynamically create an account in the Active Directory user accounts database, and must contain a credit card verification component to process customers' payment information. The account processing Web application must permit new customers to sign up and to permit existing customers to renew their subscriptions for service.
The WISP provisioning server maintains the XML subfiles that provide the client with all configuration information needed to access the network, create an account, pay for the account, and ultimately access the Internet. For more information about XML subfiles, see "XML schemas" in this paper.
For server authentication to client computers, the
provisioning server must maintain a valid certificate in its certificate store.
The certificate must contain the Server Authentication purpose in Enhanced Key
Usage (EKU) extensions and be issued by a public certification authority (CA),
such as Verisign or Thawte, that is trusted by client computers connecting to
the
The WISP domain controller and IAS server is configured with the following components.
The user accounts database on the domain controller must be an Active Directory user accounts database or a database that uses Lightweight Directory Access Protocol (LDAP) and supports dynamic creation of user accounts. When a customer signs up for an account, the account processing Web application on the provisioning server creates a new account in the user accounts database, and adds the user to a group that has clearly defined access privileges that match the type of account the customer purchased when signing up.
If you use an accounts database other than Active Directory, IAS authentication and authorization extensions must be written and installed for this process to function correctly.
For information about configuring Active Directory replication, see "Active Directory replication" in this paper.
IAS is the Microsoft implementation of a Remote Authentication Dial-In User Service (RADIUS) server and proxy, and is used to authenticate and authorize users connecting to your network. IAS is configured with remote access policies that allow guest authentication for non-domain member computers and users. It is also configured to provide IP filters to RADIUS clients (access points) that apply the filters to client connections during guest authentication. IAS also provides unrestricted access to users with valid accounts.
For server authentication to client computers, the
provisioning server must maintain a valid certificate in its certificate store.
The certificate must contain the Server Authentication purpose in Enhanced Key
Usage (EKU) extensions and be issued by a public certification authority (CA),
such as Verisign or Thawte, that is trusted by client computers connecting to
the
An IAS extension DLL defining a URL PEAP-TLV provides IAS with the ability to send the location of the provisioning server to client computers.
PEAP-Type-Length-Value (PEAP-TLV) is an Extensible Authentication Protocol (EAP) authentication type that allows the IAS server to pass information to client computers attempting to connect to your network.
In this circumstance, the value contained in the PEAP-TLV is an HTTPS Uniform Resource Locator (URL) that provides client computers running Windows XP with the location of the WISP provisioning server. With this URL, Windows XP can download the WISP XML files to the client computer.
In addition to the URL of the provisioning server, the URL PEAP-TLV includes an action parameter. The action parameter directs the client to perform a specific task. The action parameter included in the URL PEAP-TLV defines tasks such as new customer sign-up, existing account renewal, and password change.
For more information, see "How to create an IAS extension DLL and a URL PEAP-TLV" in this paper.
The WISP 2
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1436
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved