| CATEGORII DOCUMENTE |
| Bulgara | Ceha slovaca | Croata | Engleza | Estona | Finlandeza | Franceza |
| Germana | Italiana | Letona | Lituaniana | Maghiara | Olandeza | Poloneza |
| Sarba | Slovena | Spaniola | Suedeza | Turca | Ucraineana |
v What is intrusion detection
Ø Process of monitoring the events occurring in a computer system or network and analyzing them for signs of intrusion.
v Types of Intrusion Detection Systems
Ø Information Sources: the different sources of event information used to determine whether an intrusion has taken place.
t Network-based IDS
t Host-based IDS
t Application-Based IDS
Ø Analysis: the most common analysis approaches are
t Misuse Detection
t Anomaly Detection
Ø Response: the set of actions that the system takes once it detects intrusions.
t Passive measure: reporting IDS findings to humans, who are then expected to take action based on those reports.
t Active measure: involving some automated intervention on the part of the system.
v Misuse Detection (signature-based ID)
Ø Looking for events or sets of events that match a predefined pattern of events that describe a known attack. The patterns are called signatures.
Ø Rule-based systems: encoding intrusion scenarios as a set of rules.
Ø State-based intrusion scenario representations.
Ø Advantages:
t Very effective at detecting attacks without generating an overwhelming number of false alarms.
Ø Disadvantages
t Can only detect those attacks they know abouttStherefore they must be constanly updated with signatures of new attacks.
t Many misuse detectors are designed to use tighly defined signatures that prevent them from detecting variants of common attacks.
v Anomaly Detection
Ø Identify abnormal unusual behavior (anomalies) on a host or network. They function on the assumption that attacks are different from tnormalt (legitimate) activity and can therefore be detected by systems that identify these differences.
Ø Static and dynamic:
t Static: Static means a portion of the system remain constant, e.g. data integrity, tripwire, virus checkers.
t Dynamic: profile. A profile consists of a set of observed measures of behavior for each of a set of dimensions. Frequently used dimensions include:
t Preferred choices, e.g., log-in time, log-in location, and favorite editor.
t Resources consumed cumulatively or per unit time.
t Representative sequences of actions.
t Program profiles: system call sequence.
Ø Methods
t Threshold detection: certain attributes of user and system behavior are expressed in terms of counts, with some level established as permissible. Such behavior attributes can include the number of files accessed by a user in a given period of time, the number of failed attempts to login to the system, the amount of CPU utilized by a process, etc.
t Statistical measures
t Parametric: The distribution of the profiled attributes is assumed to fit a particular pattern
t Non-parametric: The distribution of the profiled attributes is tlearnedt from a set of historical values, observed over time.
t Rule-based measures: similar to non-parametric statistical measures in that ooberved data defines acceptable usage patterns, but differs in that those patterns are specified as rules, not numeric quantities.
t Other methods:
t Machine learning
t Data mining
t Neural networks, genetic algorithms, etc.
Ø Advantages
t Can detect unusual behavior and thus have the ability to detect symptoms of attacks without specific knowledge of details.
t Can produce information that can in turn be used to define signatures for misuse detectors.
Ø Disadvantages
t Usually produce a large number of false alarms due to the unpredictable behaviors of users and networks.
t Often require extensive ttraining setst of system event records in order to characterize normal behavior patterns.
v Host-based IDS
Ø Using OS auditing mechanisms: e.g. BSM in Solaris logs all direct and indirect events generated by a user; strace monitors system calls made by a program.
Ø Monitoring user activities: analyzing shell commands.
Ø Monitoring executions of system programs, e.g. sendmail's system calls.
Ø Advantages
t Can detect attacks that cannot be seen by NIDS
t Can operate in an environment in which network traffic is encrypted
t Unaffected by switched networks
t Can help detect Trojan horse or other attacks that involve software integrity breaches
Ø Disadvantages
t Since at least the information sources reside on the host targeted by attacks, the IDS may be attacked and disabled as port of the attack
t Are not well suited by detecting network scans or other such surveillance that targets an entire network
t Since they use the computing resources of the hosts they are monitoring, therefore inflicting a performance cost on the monitored systems.
v Network Intrusion Detection Systems (NIDS)
Ø Using packet sniffing.
Ø Looking at IP header as well as data parts.
Ø Disadvantages of Network-Based IDSs:
t NIDS may have difficult processing all packets in a large or busy network and therefore, may fail to recognize an attack launched during periods of high traffic.
t Modern switch-based networks make NIDS more difficult: Switches subdivide networks into many small segments and provide dedicated links between hosts serviced by the same switch. Most switches do not provide universal monitoring ports
t NIDS cannot analyze encrypted information.
t Most NIDS cannot tell whether or not an attack was successful.
v Evaluating an IDS
Ø False positive
Ø False negative
Ø ROC curve: Receive Operating Characteristic
v IDS strengths and limitations
Ø Up side:
t Detect an ever-growing number of serious problems
t New signatures are added.
t New methods are being developed.
Ø Down side:
t IDs look for known weaknesses (patterns or normal behavior)
t False positive
![]()
v Insertion: Defeating signature analysis
Ø Conceptual Example
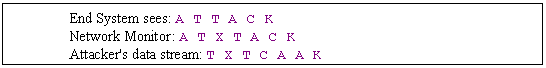
Ø Real example: 'Get /cgi-bin/phf?'
Ø Solution: make the IDS as strict as possible in processing packets read off the wire.
v Evasion
Ø Conceptual Example
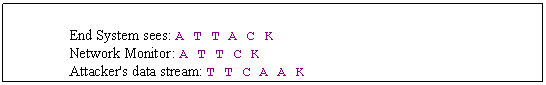
v How to achieve Insertion/Evasion Attacks based on IP
Ø Checksum (easy to solve)
Ø TTL: large enough for IDS monitor, but not enough for the end system.
Ø Don't fragment
Ø IP Options:
t Many OS automatically reject source routed packets.
t Timestamp: discard packets with illegal formats
Ø MAC address: address the faked packet to IDSts Mac address, so the end system will not receive it.
Ø IP Reassembly Problem
Ø IDS also needs to reassembly packets.
Ø Subject to DOS attacks.
Ø IDS must drop incomplete fragments (or late fragments) the same manner as the end system does. Otherwise inconsistence exists.
Ø Overlapping fragments: must process them in the same manner as the end system.
t Windows NT 4.0: always favors old data
t Solaris 2.6: always favors old data
t 4.4BSD: Favors New data for forward overlap
t Linux: Favors New data for forward overlap
v How to achieve Insertion/Evasion Attacks based on TCP?
Ø TCP Code: packets with illegal code will be discarded.
Ø SYN packet may carry data, and some implementation may not process these data.
Ø TCP Window size: inconsistence between end system and IDS can cause problems.
Ø TCP Overlapping: NT 4.0 favors old data; others favor new data.
Ø Establishing TCP Connections: consistency between IDS and end systems.
Ø Tearing Down TCP Connections: consistency
v Denial of Service Attacks on IDS
Ø CPU, memory, bandwidth
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 931
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved