| CATEGORII DOCUMENTE |
| Asp | Autocad | C | Dot net | Excel | Fox pro | Html | Java |
| Linux | Mathcad | Photoshop | Php | Sql | Visual studio | Windows | Xml |
After installing Terminal Services on a Windows 2000 domain controller, and Terminal Services Client on user's client computers, users report they are not allowed to logon interactively. You are able to log on to the Terminal server as an administrator. What should you do to allow users to log on to the Terminal server?
A: Grant the users the right to log on locally.
Your manager uses computers in many different locations. Many of the files he works with are confidential. What should you do to allow the manager to maximize security yet still allow him to access the confidential folder from any location?
A: Configure the manager's account to have a roaming user profile, and instruct him to use folder properties to set the encryption attribute for his folder.
A temporary employee has left your company. This employee used encryption to secure files in a shared folder. The files must now be made available to a new employee. What should you do? (Choose two)
A: Log on as an administrator and remove the encryption attribute from the files.
Configure the new employee's account to be an Encrypted Data Recovery Agent.
You configure the Local Security Options for the Default
Domain Policy object in your domain. You also enable a local security option to
display a logon message when a user logs onto the domain. You want a different
logon message for the
A: Create a new GPO in the
Enable policy inheritance for the new GPO.
What should you do to add a custom registry entry into a Group Policy Object with the least amount of administrative effort?
A: Configure an ADM template and add the template to the GPO.
An employee has created a file where he lists himself as the only person in the access control list. The file contains sensitive information and must be removed. Using the minimum amount of authority necessary, without modifying any of the permissions for the other files in the folder, how would you delete this file?
A: Take ownership of the file.
Grant yourself Modify permission for the file. Delete the file.
You have the following share and NTFS permissions for a Distributed file system root Public. You add a shared folder named Files as a Dfs node under the root.
Public Everyone: Read Everyone: Read
Files Users: Read Sales Full Control
Domain Admins: Full Control Domain Admins: Full Control
A user name
A: Set the share permissions for the Files folder to grant Sharon Change permission.
Sales users in your network have permission to access the Internet through a Windows 2000 Server running Microsoft Proxy Server. Sales users must enter their proxy server user names and passwords to connect to the proxy server, to the Internet, and to the Intranet server. Users who do not access the Internet do not have accounts on the proxy server. What should you do to allow all users to be able to connect to the Intranet server without entering a separate user name and password?
A: Configure each client computer to bypass the proxy server for local addresses.
You configure a server named print01.marketing.xco.local
as a print server at your
A: Use your Web browser to connect to https://print01.marketing.xco.local/printers.
Your TCP/IP network consists of Windows 2000 Servers computers, Windows 2000 Professional computers, and UNIX servers and uses IP addresses from the private range 10.0.0.0. Print jobs are sent to a shared printer on a Windows 2000 Server named PTRSRV. A print device is attached to one of the UNIX servers. This server uses an LPR printing protocol and its IP address is 10.1.1.99. The name of the printer queue is UPRINT. What should you do to allow users to be able to connect to this printer from their computers?
A: Create a local printer on PTRSRV.
Create a new TCP/IP port for an LPR port for an LPR server at address 10.1.1.99 with a queue named UPRINT.
Share this printer and connect to it from the users' computers.
You have shared a printer named HPPTR on a Windows 2000 Server computer named ptrsrv.xco.local. You grant Print permission only to the Domain Local group named XcoSales. You then add a new child domain named bristol.xco.local. A member of the global group named BrisolSales in the bristol.xco.local domain reports that she is unable to send a print job to HPPTR. What should you do to allow all member of the BrisolSales group to be able to print to HPPTR?
A: Add the BrisolSales group to the XcoSales group.
Your network consists of a Windows 2000 Server that runs Internet Information Services (IIS). Web developers need to update Web sites and virtual directories from remote locations simultaneously. What should you do to ensure that each developer can use Microsoft FrontPage to update the sites and manage content?
A: Configure the server extensions for each Web site by selecting Configure Server Extensions from the All Tasks menu in IIS.
Configure the server extensions to allow each developer update access for each Web site.
You install Client Service for NetWare on your Windows 2000 Professional computers and Gateway Service for NetWare on your Windows 2000 server computers. You have NetWare 4.0 servers in your network. After adding a new Windows 2000 Server computer, you install Gateway Service for NetWare on it, but it is unable to connect to any of your NetWare servers. What should you do?
A: Configure the NWLink IPX/SPX/NetBIOS Compatible Transport Protocol to use the correct Ethernet frame type.
You have two employees. One is a member of the Administration group, and the other is a member of the Intern group. Both groups are in the same domain. On the Intranet server, the Administration group is placed in the Security group, and the Intern group is placed in the non-security group. The Security group is granted Full Control permission for the Finance virtual directory. The member of the non-security group needs to update new financial information that is located on the Financial virtual directory. What should you do?
A: Make the non-security group employee a member of the Security group and remove him from the non-security group.
You are upgrading a Windows NT Server 4.0 computer to Windows 2000 Server. It is a member server in a Windows 2000 domain named sales.xco.local. The domain runs in native mode. What should you do to change the role of the upgraded server from a member server to a domain controller? (Choose two.)
A: Upgrade the server to Windows 2000 Server.
Run the Active Directory Installation Wizard to make the server a domain controller in the sales.xco.local domain.
Your routed Windows 2000 network includes 25 Windows 2000 Server computers. You want to install a new Windows 2000 Server computer as the first computer on a new routed segment. You configure the existing DHCP server with a scope that is valid for the new segment, and specify that the server should obtain its IP address from an existing DHCP server. But, after you complete the installation, you can only see the new server in My Network Places. You run ipconfig, and find that your IP address is 169.254.1.200, with a 16-bit subnet mask and no default gateway address. What should you do? (Choose two)
A: Configure all of the routers to route BOOTP broadcast frames.
Add a DHCP Relay Agent computer to the new routed segment.
Your network consists of a single Windows NT 4.0 domain. You want to install Windows 2000 Server on a new computer. What should you do to make the computer act as a domain controller in the existing domain?
A: On the new computer, install Windows NT Server 4.0 and designate the computer as a BDC in the existing domain.
Promote the computer to the PDC of the domain.
Upgrade the computer to Windows 2000 Server.
What should you do to configure the deployment of a Windows 2000 service pack so users automatically receive the service pack when they log on to the domain?
A: Create a Microsoft Windows Installer package for the service pack.
Configure the package in a Group Policy.
You are installing Windows 2000 on new computers in your network. These servers will provide file and print services. You want to use a centralized copy of the Windows 2000 installation files, which are stored on an existing Windows 2000 Server. What three actions should you take? (Choose three)
A: Create an MS-DOS network boot disk.
Create an Unattend.txt file.
Create a UDF file that identifies the names of the new computers.
Begin the installation process by running the Winnt /s /u /udf.
Your network consists of numerous domains within a single LAN, with one remote domain. The remote location is running an outdated service pack. Retaining the domain administrator's access to the Group Policy configuration, what should you do to update the remote location while reducing network traffic and easing administration of Group Policies?
A: Configure a Group Policy for the remote domain.
Configure a service pack software package for the Group Policy.
Your 32-bit application stops responding several days after installation. Task Manager shows the CPU usage to be 100 percent. You end the application. The CPU usage is still at 100 percent. What should you do?
A: Use Task Manager to end any related child processes.
Your application writes a large number of temporary files to a single directory on your Windows 2000 Server. You add three new 100-GB SCSI disks to hold the temporary files. You want the application to use all 300 GB of space with a single drive letter, using the fastest performance when writing to the disks. What should you do?
A: Convert all three disks to dynamic disks.
Create a striped volume.
Your boot volume is installed on volume C on your Windows 2000 Server, and volume C is mirrored on dynamic Disk 1. Later, you find that the status of volume C is Failed Redundancy, and the status of Disk 1 is Missing. The status of volume C does not return to Healthy after you attempt to reactivate Disk1. What should you do?
A: Remove the mirror on Disk1, replace the disk, and add back the mirror to the new
Disk 1.
After upgrading a Windows NT Server 4.0 computer to Windows 2000 Server, Disk 1 fails. The computer has two hard disks, and the system and boot partitions are located on two primary partitions on Disk 0. Both partitions are mirrored on Disk 1. You replace the failed disk with another from a Windows 2000 computer, but find the Repair Volume option is unavailable when you try to repair the fault-tolerant volumes. How should you repair the mirror set? (Choose two)
A: Delete all volumes on Disk 1.
Change Disk 1 back to a basic disk.
Repair the fault-tolerant volumes on Disk 0.
Break the mirror set.
Convert Disk 0 to a dynamic disk.
Create a mirror on Disk 1.
You have installed the boot volume D on your Windows 2000 Server computer on dynamic Disk 0, and mirror volume D on dynamic Disk 1. Later, you find the status of volume D is Failed Redundancy. The status of Disk 1 is Online (Errors). What should you do? (Choose two)
A: Break the mirror, delete the volume on Disk 1, and re-create the mirror.
Reactivate the mirror on Disk 1.
Your Windows 2000 Server computer has a single hard disk with two partitions. One of your applications creates a large log file in the SystemrootTemp folder. The disk does not contain enough free space to accommodate the log file. What should you do?
A: Add a second hard disk.
Delete the contents of the SystemrootTemp folder.
Create and format a partition.
Mount the partition as the SystemrootTemp folder.
You convert the stripe set with parity to a dynamic RAID-5 volume on your Windows 2000 Server computer that contains a stripe set with parity on a four-disk array. Users then report that disk access on the server is slow. The status of the third disk in the array shows Missing. What should you do first to recover the failed RAID-5 volume?
A: Ensure that the third disk is attached to the server and has power.
Use Disk Management to reactivate the disk.
You share a folder on your Windows 2000 Server that contains multiple subfolders. Some of these subfolders are compressed, and some are not. How do you move files from one uncompressed folder to a compressed folder, and ensure the files are compressed when you move them, without compressing the remaining files in the original uncompressed folder?
A: Copy the files from the uncompressed folder to the compressed folder, then delete the
original files.
You have configured your Windows 2000 Server, which utilizes a large NTFS volume, to have disk quotas for the NTFS volume. All users have a default limit of 100 MB, and the option to deny space to users who exceed their limit has been enabled. A user complains that they are receiving the error message "The disk is full or too many files are open". What should the user do?
A: Remove files until the total uncompressed file size is less than 100 MB.
You are the administrator of your company's network. You use a non-administrator account to log onto the server to perform routine upgrades. Prior to updating all the critical system files and patches on the server, what should you do?
A: Log on as an Administrator and run Windows Update.
Each of your branch offices uses Internet Connection Sharing to connect to the Internet. Randy is configuring a Windows 2000 Server as a file server. When he uses Windows Update for the first time, he selects Product Update, and receives an access denied error. What should you do to allow Randy to configure the server?
A: Give Randy's user account administrator privileges on the Windows 2000 Server
computer.
What three things can you do to help diagnose why users cannot connect to a second modem configured with Routing and Remote Access on your Windows 2000 Server? (Choose three)
A: Use the Diagnostics tab on the Phone and Modem Options.
Use Device Manager to identify any port resource conflicts.
Use the Routing and Remote Access snap-in to find out whether the ports are operational.
An incorrect driver was installed during the installation of a modem on your Windows 2000 Server computer. The computer will be used as a Routing and Remote Access server for a branch office. You attempt to remove the modem by the Phone and Modem Option, but the computer stops responding. What is the quickest way to install the correct driver after restarting the computer?
A: Use the Add/Remove Hardware Wizard to uninstall the modem.
Restart the server.
You are replacing an integrated 10-MB Ethernet adapter with a new 100-MB Ethernet adapter. After installing the new adapter you receive an error message stating the new adapter is missing or is not working. What should you do?
A: Use Device Manager to disable the integrated 10-MB Ethernet adapter.
You have a Windows 2000 Server that uses a non-Plug and Play ISA modem that uses IRQ 5. You add a PCI modem and restart the computer. You realize that both modems are trying to use IRQ 5. What should you do?
A: Edit the CMOS settings on the computer to reserve IRQ 5 for non-Plug and Play.
Your network is not directly connected to the Internet, and uses the private IP address range of 192.168.0.0. You install Routing and Remote access. You can successfully dial into the server, but cannot access any resources. The ipconfig command shows the dial-up connection has been given the IP address of 169.254.75.182, and when you ping the server, you receive a "Request timed out" message. What should you do?
A: Ensure that the remote access server is able to connect to a DHCP server that has a scope for its subnet.
You want to make an application available on all of the client computers in your network using Terminal Services on a Windows 2000 Server computer. The server will not run as a domain controller. You install Terminal Services. The Support department needs to be able to remotely control users' sessions to support and troubleshoot the application. What should you do to enable the Support department to control users' sessions?
A: Grant the Support department Full Control permission to the Remote Desktop Protocol on the Terminal server.
Your network consists of ten subnets that contain 10 domain controllers, 10 member servers, and numerous client computers. All servers run Windows 2000 Server, and all clients run Windows 2000 Professional. Two domain controllers are DNS servers. You use only TCP/IP. You want client computers to be able to register and resolve addresses if a server fails. How should you configure the DNS servers so that all computers can resolve the address of all other computers by using DNS?
A: Configure at least two servers with Active Directory integrated primary zones for the domain.
You have a multiple-process database named Application on your Windows 2000 Server. Users report that the application has stopped responding to queries. The server is running, so you decide to restart the application. What should you do before restarting the application?
A: End the Application.exe process tree.
Your Windows 2000 Server computer uses a SCSI adapter that is not included in the HCL. You install an updated driver for the adapter. After restarting the computer, you receive "Inaccessible_Boot_Device". What should you do? (Choose two)
A: Start the computer by using the Windows 2000 Server CD-ROM.
Perform an emergency repair.
Reinstall the old driver for the SCSI adapter.
Start the computer by using the Recovery Console.
Copy the old driver for the SCSI adapter to the system volume and to C:ntbootdd.sys
Restart the computer.
How can you revert Active Directory to a version that was backed up on each of three domain controllers on a previous day?
A: Shut down and restart a single domain control in Directory Services Restore Mode.
Use Windows Backup to restore the
Run the Ntdsutil utility.
Restart the computer.
After adding a new partition to your disk, you receive "Windows 2000 could not start because the following file is missing or corrupt: <Windows 2000 root>system32ntoskrnl.exe. Please re-install a copy of the above file". What should you do?
A: Start the computer by using the Recovery Console.
Modify the Partition parameter in the operating system path in C:Boot.ini.
Your Windows 2000 Server computer is a file server. It runs many 16-bit applications. One of these stops responding, causing all other 16-bit applications to stop responding. What should you do to isolate the application for monitoring and troubleshooting? (Choose all that apply)
A: Create a batch file that starts the application by running the start /separate command.
Use this batch file to start the application.
Create a shortcut to the application, and select the Run in a separate memory space.
Use this shortcut to start the application.
What columns would you choose to find out whether the response times of a new application would improve by the addition of one or more processors on your Windows 2000 Server? (Choose two)
A: USER Objects and I/O Reads.
After using Regedt32 to edit the registry of your Windows 2000 Server to insert a new value, and remove an unused key, your computer stops responding before the logon screen appears after you reboot. What should you do to return the computer to its previous configuration?
A: Restart the computer using the Last Known Good Configuration.
You have a 12 GB primary partition formatted as FAT32 on your Windows 2000 Server computer. The number of users and average size of files remains constant over a period of time. Users then begin to report that the server does not retrieve files as fast as when the server was first installed. What should you do?
A: Defragment the disk.
You install a new tape device on your Windows 2000 Server. After restarting the computer, you receive the error: "IRQL_NOT_LESS_OR_EQUAL". What should you do to bring the server back online as quickly as possible?
A: Restart the computer by using the Recovery Console.
Disable the driver.
Restart the computer.
Remove the driver.
Users report that when you run Microsoft Excel every afternoon, the response time on the server lags. What should you do?
A: Use Task Manager to set the priority of the Excel.exe process to Low.
Running System Monitor locally, and ensuring it has the least impact on other processes, how do you measure the physical disk performance counters on your Windows 2000 Server computer? (Choose two)
A: From the command prompt, run the Start/low perfmon command.
Use Task Manager to set the priority of the MMC.EXE process to Low.
Your Windows 2000 Server runs both 32-bit and 16-bit applications. Each 16-bit application is configured to run in a separate memory space. You want to create a performance baseline chart for all applications on the server. You add all of the 32- bit applications . What should you do to add the 16-bit applications?
A: Add the ntvdm and the ntvdm#2 instances of the %Processor Time counter for the
Process object.
You work with files that are confidential. These files are kept in your Private folder located in your home folder. You use numerous computers to access these folders. What should you do to maximize security of the Private folder, and still allow access from remote computers?
A: Configure your account to use a roaming user profile.
Use the properties of the Private folder to set the encryption attribute.
Your Windows 2000 Active Directory network consists of Windows 2000 Professional computers and Windows NT Workstation computers. Users of the Windows 2000 Professional computers cannot change their desktops or the display settings on their computers. Users of the Windows NT Workstation computers can change all display settings. What should you do to restrict all users of Windows NT Workstation computers from changing their desktop settings?
A: Configure a Windows NT policy file and place it in the proper folder on the PDC emulator.
Your Windows 2000 network consists of Windows 2000 Servers that were upgraded from Windows NT, Windows 2000 Professional computers, and Windows NT Workstation computers. After you implement GPOs for each OU, you find that the GPOs only apply to users of the Windows 2000 Professional computers. You want to restrict users of the Windows NT Workstation computers from accessing registry-editing tools. What should you do?
A: Create a Windows NT system policy file on a Windows 2000 domain controller.
Configure the policy so that it restricts default users from accessing registry editing
tools.
You have created a GPO for the Finance OU in your network. You want to prevent users in the Finance OU from accessing My Network and running the System applet in Control Panel. But, you want the Managers Domain Local group to be able to access My Network, yet not run System in Control Panel. What should you do?
A: Create a second GPO in the OU.
Add the Manager's group to the ACL of the GPO.
Allow the Manager's group to apply the Group Policy.
Disable the permission of the Authenticated Users group to read and apply the Group Policy.
Configure the new GPO to allow access to My Network Places.
Give the new GPO a higher priority than the original GPO.
How do you configure a Group Policy so that future changes to the Group Policy will be applied within 15 minutes to any computers that are logged onto the network?
A: Enable and configure the Group Policy refresh interval for computers.
You share a folder on your Windows 2000 Server that contains multiple subfolders. Some of these subfolders are compressed, and some are not. The Marketing folder is compressed. You want to delete it, but want to keep all the files in the folder. You want to copy all the files to the Admin folder before deleting the Marketing folder. You want the files to remain compressed, but do not want to compress any files in the Admin folder. What should you do?
A: Move all the files from the Marketing folder to the Admin folder.
Your Windows 2000 Server computer has a spanned volume that consists of areas on three disks. The disks support hot swapping. One of the disks fails. You replace the disk with a new, non-partitioned disk. How should you recover the spanned volume and its data as quickly as possible?
A: Rescan the disks.
Remove the spanned volume and create a new spanned volume that includes the new disk.
Format the spanned volume.
Use Windows Backup to restore the data.
Your Windows 2000 Server has a RAID-5 controller. The RAID array is configured as two partitions. Drive C is a 2 GB partition that holds the operating system and paging file. Drive D is a 30 GB partition that holds the home folders. Engineering employees use a data capture application that generates files that can be larger than 100 MB. You want to implement disk quotas. Normal users can be allowed to store a maximum of 75 MB. Quotas should not limit engineers. What should you do?
A: Enable quota management on drive D.
Select the Deny disk space to users exceeding quota limit check box.
Set the default quota limit to 75 MB.
Create a new quota entries for the Engineers' user accounts.
Select 'Do not limit disk usage for this entry.'
Your Windows 2000 Server contains two hard disks. Each disk is partitioned as a single primary partition. The first disk is formatted as FAT32, the second as NTFS. You compress shared folders on the second disk. When users move compressed files from a shared folder on the second disk to a shared folder on the first disk, the files lose their compression. What two actions should you take to ensure that all files moved from folders on the second disk to shared folders on the first disk remain compressed?
A: Convert the first disk to NTFS.
Compress the shared folders on the first disk.
You have two Windows 2000 Servers, Srv1 and Srv2. Srv1 has a spanned volume over three physical disks. These disks support hot swapping. The drive letter that the spanned volume uses on Srv1 is not currently in use on Srv2. You want to move the three disks to Srv2, using the same drive letter as Srv1. You back up the spanned volume. What should you do next?
A: Move the disks from Srv1 to Srv2.
On Srv1, rescan the disks.
On Srv2, rescan the disks.
You are installing Windows 2000 Server on a new computer that is connected to a network that contains Windows 98 computers and Windows 2000 Server computers. You want to install Windows 2000 Server from source files located on a server on the network. What should you do?
A: Start the new computer by using a Windows 98 network boot disk.
Connect to the network server.
Run WINNT.EXE.
Your Windows 2000 Server has two NTFS partitions. Windows 2000 Server is installed on drive D. After a power failure, you receive the error message: "NTLDR is missing. Press any key to restart". What should you do?
A: Start the computer by using the Windows 2000 Server CD-ROM and choose to repair the installation.
Select the Recovery Console and copy the NTLDR file on the CD-ROM to the root of the system partition.
What should you do to install a customized HAL designed for a computer on which you are installing Windows 2000 Server?
A: During the hardware confirmation portion of Windows 2000 Setup, install the customized HAL.
Your network consists of two domains: xco.local and tech.xco.local. It has Windows 2000 Professional computers and Windows 2000 Server computers. You enable auditing in the domain policy object for xco.local to audit the success and failure of object access. After installing a printer on a domain controller, you configure auditing on this printer to monitor printing successes and failures. When you review the security log later, no events have been written to the log, even though you know the printer has been used. What should you do to log all successes and failures of printing for the printer?
A: Configure auditing of successes and failures of object access in the Default Domain
Controllers Policy object in the Domain Controllers OU of the tech.xco.local domain.
Your network uses the TCP/IP protocol for its Windows 2000 Professional and Windows NT computers. You have one server that acts as both a WINS server, and a DNS server. All the client computers are configured to use this server for DNS and WINS. Users of Windows NT Workstation cannot connect to a file server, but Windows 2000 Professional users can. This server has a static address of 192.168.1.11. What should you do to allow the Windows NT Workstation computer to connect to the file server?
A: Select Enable NetBIOS over TCP/IP.
Add the WINS address used by the Windows NT Workstation computers.
Both of your domains are Active Directory domains that run in native mode. How can you see a list that shows which users are allowed to use remote access to your network?
A: Create a group named RAS_USERS.
Add users who are permitted to dial in to the network.
Create a remote access policy that allows only this group to use the remote access server.
Display the members of the group.
Your network is routed and uses TCP/IP as its only protocol. You have a single domain with Windows 2000 Professional and Windows NT Workstation computers. You install Gateway Service for NetWare on a Windows 2000 Server computer. You install a second network adapter on the gateway server. You want to configure the first adapter for communications to and from your Windows-based client computers exclusively. Which checkboxes in the Local Area Connection Properties dialog box should you select? (Choose all that apply)
A: Client for Microsoft Networks
File and Printer Sharing for Microsoft Networks
Internet Protocol (TCP/IP)
You have Routing and Remote Access on a server that has
one modem. The server is configured to use demand-dial routing to connect to
the main office. The manager wants users to be able to dial in to the server
only between
A: Set the remote access policy to
deny connections between
Your company has developed a 32-bit application that collects information from various processes. You want to make the application available on all of the client computers by using Terminal Services. The company wants users to shut down their computers at the end of their shifts, and to leave the application running on the Terminal Server. What should you do?
A: Set the RDP on the server to override user settings, and set the End Disconnected Sessions setting to Never.
Frequently, a newly installed modem stops communicating with your ISP. The only way to reactivate the modem is to restart the computer. You want to install a new driver for the modem. What should you do?
A: In Device Manager, on the property sheet for the modem, click the Update Driver button.
You have a Windows 2000 Server that uses a non-Plug and Play EISA modem that uses IRQ 11. You add a second PCI network adapter and restart the computer. You realize that both adapters are trying to use IRQ 11. What should you do?
A: Edit the CMOS settings on the computer to reserve IRQ 11 for the non-Plug and Play devices.
Your Windows 2000 Server has an integrated network interface adapter. You are replacing it with a new network interface adapter that will be installed in an available PCI slot. When you restart the computer, you receive an error message stating that the new network interface adapter is missing or not working. What should you do?
A: Disable the integrated network interface adapter.
A disk with the ARC path multi(1)disk(0)rdisk(1)partition(1) is not responding. Which disk should you replace?
A: Click Controller 1, Disk number 2.
You add a new SCSI disk controller that has six new disks attached to your Windows 2000 Server that has two disks attached to an EIDE disk controller. The new controller is not included in the HCL. When you restart your computer, Windows does not detect the new controller. What should you do? (Choose two)
A: Use the Add/Remove Wizard to add a new SCSI and RAID controller.
Use the manufacturer's setup program to install the SCSI driver.
You are logged on to a Windows 2000 Server computer as a member of the Backup Operators group. You try to configure the software for a tape backup device, but the configuration fails. You must update the driver. What should you do?
A: Instruct a domain administrator to run the 'runas' command using the domain administrator's user name and password.
Click the Update Driver button on the Driver tab for the tape backup device.
You are installing Windows 2000 Server on ten new computers. These computers will provide file and print services to branch offices. You want to install, configure and test Windows 2000 Server on the branch offices' computers before shipping them to the branch offices. The users of the branch offices should enter the computer names and serial numbers when they receive the computers. What should you do?
A: Install Windows 2000 Server on the computers. Use Setup Manager to create a
SYSPREP.INF file for SYSPREP.EXE.
Place the SYSPREP.INF file on the computers and run the 'sysprep -nosidgen' command.
You are upgrading a Windows NT Server 4.0 computer to Windows 2000 Server. The system partition uses FAT. After starting the Setup program from the Windows 2000 Server CD-ROM you receive an error message: "You chose to install Windows 2000 on a partition that contains another operating system. Installing Windows 2000 on this partition might cause the operating system to function improperly". What should you do?
A: Restart the computer.
Run WINNT32.EXE from the Windows NT Server environment.
Your network consists of two trees, with four domains in each tree. You plan to deploy a service pack to the support.IS.xco.com domain and the support.IS.yco.com domain, but to no other domains. You will use a Group Policy to configure the service pack package. You want to minimize complexity, administration, and network traffic. You create a Windows Installer package for the service pack. What should you do to configure the Group Policy?
A: Configure the Windows Installer package in a Group Policy for the support.IS.xco.com and support.IS.yco.com domains.
Your computer has three 100 GB hard disks without any partitions defined. You want as much space on Disk 0 as possible for the partition on which Windows 2000 Server is to be installed. You want as much disk space as possible across all three disks to be accessible by using a single driver letter. What should you do?
A: Install Windows 2000 Server on a 100 GB NTFS partition Disk 0.
After Setup is complete, create a 100 GB partition on Disk 1 and Disk 2.
Mount the partition on Disk 1 and Disk 2 as subdirectories on the Disk 0 partition.
You configure a new Windows 2000 Server as an intranet server. You configure a sales Web site and a Finance virtual directory in the Departments Web site. Users report that they can only see .htm, and .asp files. For security, you need to disable the users' ability to view the files of all Web sites in the form of a list. What should you do?
A: Clear the Directory Browsing checkbox for the server properties.
Apply the settings to the child web sites.
You configure an HP JetDirect device with an IP address of 10.4.20.200/16. You want to create and share a printer at a domain controller with an IP address of 10.5.20.50/16 that is connected to the TCP/IP port of the print device. When you enter the IP address of the device, you receive an error message. What should you do?
A: Change the IP address of the print device to 10.5.20.200.
Permissions for a shared folder on your NTFS partition are as follows:
Share Users Change
NTFS Users Full Control
Users are connected to this folder. You have an immediate need to prevent ten of the files in this folder from being modified. What two actions have the smallest possible effect on users who are using other files on the server? (Choose two)
A: Modify the NTFS permission for the ten files.
Disconnect the users from the Data folder.
Your network consists of Windows 2000 Servers. Each has separate system partitions and separate boot partitions formatted as NTFS. After you shut down one of the servers and restart, you receive the error message: "NTLDR is missing. Press any key to restart". You do not want to lose any settings you made since the original installation. What should you do to install a new NTLDR file on the server?
A: Start the computer by using the Windows 2000 Server CD-ROM and choose to repair the installation.
Select the Recovery Console and copy the NTLDR file on the CD-ROM to the root of the system partition.
You are planning to install a Windows 2000 Server computer that has a disk controller that is not included in the HCL. You start the computer using the Windows 2000 Server CD-ROM. At the end of the text mode on the restart of the computer, you receive "Inaccessible_Boot_Device". What should you do? (Choose two)
A: Restart Windows 2000 Setup by using the Windows 2000 Server CD-ROM.
Install a driver for the SCSI controller from a floppy disk.
What should you do to configure the deployment of an application update so that users automatically install the update when they log on to the domain?
A: Create a Microsoft Windows Installer package for the application update.
Apply the package to a Group Policy.
Each of your company's offices has a network of 5 - 20 computers. Employees have a limited knowledge of Windows 2000. You plan to install 50 identical computers with Windows 2000 Server in these offices. You create a Setup Information File that specifies the company's standard configuration. Using the least possible amount of time, how should you automate the installation process?
A: Create a floppy disk that contains only the SIF.
Instruct an employee at each office to start the installation by using the Windows 2000
Server CD-ROM, with the floppy disk inserted.
Your network consists of Windows NT Server computers, Windows NT Workstation computers, and UNIX computers in a single Windows NT domain. You are upgrading a Windows NT Server to Windows 2000 Server. It is currently a BDC. The existing DNS server is a UNIX computer that supports SRV (service) records and accepts dynamic updates. Another Windows NT Server serves as a WINS server. You plan on configuring the upgraded server as a domain controller in a new Active Directory forest, with the Windows NT domain accounts upgraded to Active Directory. Other domain controllers will be upgraded after this initial server upgrade. What should you do?
A: Promote the server to the PDC of the domain.
Run Windows 2000 Setup on the server.
You are installing Windows 2000 Server on a multiprocessor computer. What should you do to install a customized HAL designed for a computer on which you are installing Windows 2000 Server?
A: During the text mode portion of Windows 2000 Setup, install the customized HAL.
Your network consists of Windows 2000 Server computers and Windows 98 computers. You are installing Windows 2000 Server on a new computer that has one 20 GB hard disk with no partitions defined. The Windows 2000 Server CD-ROM is unavailable, so you are installing Windows 2000 Server from files on a server on the network. You want the entire hard disk of the new computer to be used for the system partition. What should you do?
A: Start the new computer by using a Windows 98 network boot disk.
Create and format a single FAT32 partition.
Connect to the network server.
Run WINNT.EXE.
Your Windows 2000 Server has five hard disks. Four 100 GB disks are configured as a single striped volume. You want to reconfigure these so that the volume is fault-tolerant and has as much space as possible. Using only the existing hardware, what should you do?
A: Backup the data on the striped volume, then delete the striped volume.
Create a RAID-5 volume from the four disks.
Restore the data to the new RAID-5 volume.
You configure a remote access server on your TCP/IP network. When users connect to the server, they receive the error message: "IPX/SPX compatible CUSTOMIZED PACKAGE OF INTERNET EXPLORER reported error 733: The PPP control network protocol for the network protocol is not available". If the users allow the connection to continue, they are able to connect to services that use TCP/IP. How should you prevent this message from being displayed?
A: Configure the client computers to use only TCP/IP for the connection to the remote access server.
Your company consists of a main office and several branch offices. Each branch office has a private network with a 56-Kbps connection to the Internet. To provide each office with access to the Internet, you will use Network Address Translation. After configuration, you discover that connections cannot be made to sites by using the FQDN, but connections can be made by their IP address. What should you do?
A: Configure the computers on each of the branch office networks with the address of a
DNS server on the Internet.
You have created a shared printer for your managers so they do not have to wait for their documents to print when the printer queue is large. You set up permissions for the following groups; Administrators, Creator Owner, Everyone, Managers, Print Operators and Server Operators. You select the check box to allow Printer permission for the Managers group. You want only the Administrators, Print Operators, Server Operators, and Managers groups to be able to print to the printer. What should you do?
A: Remove the Everyone group.
Clear all check boxes for the Everyone group.
Your Windows 2000 Server network runs in mixed mode. You create and share a new HP LaserJet printer. Your Windows 2000 Professional clients can print to the new printer successfully, but your Windows NT Workstation clients cannot. You receive the following error message on your NT Workstation clients: "The server on which the printer resides does not have a suitable HP LaserJet printer driver installed. Click on OK if you wish to install the driver on your local machine". What should you do to have the printer driver automatically installed on the Windows NT Workstation computers?
A: Change the sharing options on the printer to install additional drivers for Windows NT or Windows 2000.
You suspect someone is trying to log onto your domain by guessing user account names and passwords. What should you do to find out which computers are being used for this?
A: Edit the Default Domain Policy object to audit account logon failures.
Your Windows 2000 domain trusts each of your two Windows NT domains, and the Windows NT domains trust the Windows 2000 domain. A Windows 2000 domain controller is configured to use the highly secure domain controller security template. Windows NT users report they cannot access resources on this domain controller. What should you do?
A: Apply a less restrictive custom security template to the domain controller.
You are the administrator of the xco.local domain. You
configure the Local Security Options and other options for the Default Domain
Policy object. You delegate administration of the
A: From the Group Policy options for the xco.local domain, set the option not to override.
Your Active Directory single domain consists of Windows NT workstation clients and Windows 2000 Professional computers. You create a Windows NT default user policy on the Windows 2000 Server computer that is configured as a PDC emulator. It denies access to Network Neighborhood. You install Terminal Services on one of the servers, and Terminal Services Client on the NT Workstation client computers. Users of the Terminal server can still browse the network when they open My Network Places. What should you do to prevent all default users from browsing the network?
A: Create a Windows 2000 Group Policy that denies user access to My Network Places.
You have a Windows 2000 Server that serves as a print server. You install a second Plug and Play network adapter to improve network performance. The first network adapter uses IRQ 11. The second network adapter uses IRQ 5. The server is now unable to print to the print device connected to the non-Plug and Play LPT2 port adapter. What should you do?
A: Edit the CMOS settings on the computer to reserve IRQ 5 for non-Plug and Play devices.
Your Windows 2000 Server is configured with Routing and Remote Access. What can you do to help diagnose why dial-in users cannot connect to the server via a new modem?
A: Use the Routing and Remote Access snap-in to find out whether the ports for both modems are operational.
How do you configure the remote Windows 2000 server computers so that whenever a new Microsoft driver becomes available, branch offices are notified automatically when the administrator logs onto the server?
A: Install Windows Critical Update Notification.
After you install a new video adapter, one of the users at a remote location reports that Routing and Remote Access does not accept calls. After you resolve the Routing and Remote Access problem, you need to configure the server to prevent users from installing any unsigned device drivers. What two actions should you take in the Driver Signing Options dialog box?
A: Set File Signature Verification to Block.
Select the Apply settings as system default check box.
To provide redundancy for all data stored on your RAID-5 disk, you install a second RAID-5 disk array. When you right-click the free space on the new array in Disk Management, you see no option to create a new volume or mirrored volume. What should you do before you create a mirrored volume on the new array?
A: Convert both arrays to dynamic disks.
Your network uses the Encrypting File System (EFS) to encrypt data. You are installing a new server that has a 6 GB NTFS partition. You want to move numerous EFS folders to a new server. These folders must maintain their encryption. What should you do?
A: Backup the folder using the Backup utility in Windows 2000.
You are implementing a 140-node network. It should be divided into 10 subnets. Each subnet must be able to accommodate up to 14 nodes. How should you configure the IP addressing structure if your company's IP address is 194.194.194.0?
A: 194.194.194.0/28.
You have a Pentium III 400 MHz Windows 2000 Server computer with a built-in sound card. You must install another sound card that is on the HCL and enable it on the server. How should you configure the computer to use the new sound card and install the drivers for the sound card? (Choose three)
A: Install the new sound card.
In Device Manager, disable the integrated sound card.
Allow Windows 2000 to automatically detect the new sound card during the next boot of the computer after the sound card is installed.
Your Windows 2000 domain operates in native mode. The server uses the default remote access policy. You want the remote access permissions for new user accounts to automatically allow access. What should you do?
A: Change the setting from Control Access through Remote Access Policy to Allow Access.
All subnets on your network use a /24 subnet addressing scheme. Your router that connects a subnet to the network has an IP address of 158.25.64.1. The next router in line has an IP address of 158.23.65.2. Which subnet mask and default gateway should you use to configure the client computer?
A: 255.255.255.0
Your Windows 2000 network is configured with Active Directory and Group Policies. You create a Group Policy object linked to an Organizational Unit. You do not want the GPO to use any policies from the domain. What should you do?
A: Check the "Block Inheritance" box in the main screen of the OU's Group Policy editor.
On your Windows 2000 Active Directory domain controller, you are backing up the system boot files, the registry, the COM+ class registration database, the Certificate Server database, the Active Directory Services database, and the SYSVOL directory. Your domain controller is a Pentium 200 MHz with a RAID 5 array with ten 3-GB partitions. Minimizing backup time, how can you backup these files?
A: Use Windows Backup to back up the
How can you assign an application to one processor exclusively?
A: Right-click the application process, select Set Affinity, and select the appropriate processor.
You have an Active Directory-enabled Windows 2000 server. You create an Organizational Unit with a child OU named Designers. The child object must have explicit rights assigned to it, but the OU's permissions must propagate to the OU and all its other child objects. What should you do? (Choose all that apply)
A: Configure permission inheritance on the OU.
From the Security tab, clear the Allow Inheritable Permissions From Parent to Propagate To This Object box on the Designer's object.
You must prevent any unsigned drivers from being installed on any computer in your Windows 2000 network. The network consists of Windows 2000 domain controllers, Windows 2000 file and print servers, and Windows 2000 Professional computers. What should you do?
A: Configure the domain controllers, file and print servers, and client computers to Block unsigned drivers.
Your network contains two routed subnets: Subnet A and Subnet B. Subnet B contains a Windows 2000 server configured as a DHCP server. This server has scopes created for both Subnet A and Subnet B. Subnet A does not contain a DHCP server. The clients on Subnet A are not receiving IP addresses from the DHCP server. What can you do to enable clients in Subnet A to receive dynamically assigned IP addresses? (Choose all that apply)
A: Configure an RFC 1542-compliant router to forward BOOTP messaging between subnets.
Configure an RFC 1560-compliant router to pass all UDP traffic on ports 2151, 2152, 2153 and 2154.
Configure a DHCP relay agent on Subnet A to forward DHCP messages to Subnet B.
You configure several Group Policies to restrict users' desktop configuration changes. You want them to be applied immediately. What should you do?
A: Run the SECEDIT.EXE command to refresh the policy.
On several Windows 2000 computers you install the NWLink IPX/SPX/NetBIOS Compatible Transport Protocol. After installing the protocol you discover that the Windows 2000 machines can communicate with some but not all of the NetWare servers . What should you do?
A: The frame type is not set correctly. Reconfigure the Windows 2000 computers for Manual Frame Detection.
You are backing up all of the data on a computer on your network using the following strategy.
Saturday
Monday Differential Backup
Tuesday Differential Backup
Wednesday Differential Backup
Thursday Differential Backup
On Friday at
A: Restore data from Saturday, then Thursday.
You wish to install Recovery Console on a computer that has a mirrored volume. How do you do this?
A: Break the mirror, then install the Recovery Console using x:I386winnt32.exe
/cmdcons. Reestablish the mirrored volume.
You are concerned that someone is accessing confidential data files on a Windows 2000 Professional computer. You would like to configure the system so that all attempts to access those files, whether successful or failed, are tracked. What should you do? (Choose all that apply)
A: Right-click on the files to be audited.
From the Security tab, click Advanced.
From the Auditing tab click Add and select the user or group whose actions you want to audit.
In the Local Computer Policy, choose Audit Policy and select the checkboxes for "Success" and "Failure" under "Audit object access".
You use Network Address Translation to provide Internet access for the client machines on your network. You have a Windows 2000 Professional machine that you would like to use to establish a secure Virtual Private Networking session with another Windows 2000 machine at a remote office using L2TP. You are unable to establish an L2TP connection with the remote office, but are successful when you try to connect to another machine in the same office. Why are you unable to connect to the remote office?
A: You cannot establish a L2TP session behind a device performing NAT.
The L2TP session fails because the IP Security packets have become corrupted.
You are installing a new computer named Svr2.xco.com on your Windows 2000 network. You want to enter the appropriate TCP/IP addresses for the subnet mask and the default gateway for Svr2.xco.com. Which subnet mask and default gateway should you use? To answer, drag the appropriate addresses to the appropriate boxes in the Internet Protocol (TCP/IP) Properties dialog box.
A: Drag 255.255.0.0 to the subnet mask, and the IP address of the router to the default gateway.
Your Win 2000 Server has 2 hard disks. The system volume on Disk1 is mirrored to Disk2. These disks do not support hot swapping and you backup the mirrored volume using Windows Backup. When Disk1 fails, you shut down and replace it with an unpartitioned disk. How would you make the mirrored volume fault tolerant again?
A: Restart the server from the mirrored volume by using a startup floppy.
Configure the new Disk1 as a dynamic disk.
Break and recreate the mirror.
Your Windows 2000 server called DNS1 provides DNS service for your whole network. You want to configure a Windows 2000 computer called PRINT1 as a print server and you want it to print to a queue on a UNIX computer. You can PING the UNIX computer from PRINT1, but you cannot connect using its name. After adding a record for the UNIX computer to the DNA1 zone file, you still cannot connect using the name. What should you do?
A: Stop the DNS client service and restart it.
Run the ipconfig /flushdns command.
Your Windows 2000 server called DFS1 is a member of a workgroup and is a stand-alone Distributed file system (Dfs) server. The Dfs is configured for 10 nodes for shared resources on other computers. Your network has 100 Windows 2000 Pro computers that connect to by using the path DFS1Public. Your network currently uses DHCP, DNS and WINS. You install Dfs service on a new computer called DFS2 so you can take DFS1 offline temporarily. What should you do to ensure that Dfs clients can locate shared folders while DFS1 is off-line?
A: Create a Public folder on DFS2 and then create a Dfs tree that is identical to the existing tree in DFS1.
Change the DNS host resource record for DFS1 to point to the IP address of DFS2.
You have a VPN that connects 20 branch offices to the main office. You need to take it offline to make configuration changes. What would you do first?
A: Disable the Routing and Remote Access option for the VPN server.
You have a mail hosting server called MAIL1 and a domain controller called DOMAIN1 that runs the DNS for the TCP/IP network. Both servers are Windows 2000 computers with statically configured IP addresses. You take DOMAIN1 offline for maintenance. However, when you bring it back online, some clients cannot connect to MAIL1. When you check the DNS you find there is no entry for MAIL1. How would you make MAIL1 recreate its dynamic DNS entry?
A: Run the ipconfig /registerdns command.
You have two Windows 2000 domains. Each domain contains
two domain controllers called DC1 and DC2. Your Active Directory contains 2
sites named
A: Backup the system state data for each DC1 computer.
Backup the system state data for each DC2 computer.
You are installing a VPN. The VPN server is located inside a firewall that is configured to pass ICMP, TCP port 25 for SMTP, port 119 for NNTP, and port 80 for HTTP only. The VPN fails when you try to connect over the Internet. However, you can ping the VPN server. What do you need to do to the firewall to achieve a successful connection?
A: Enable port135 for the RPC port mapper service.
Enable ports 137, 138, and 139 for NetBIOS.
You have created 2 shared printers on Windows 2000 computers. One printer is shared as STUDENTS and the other as STAFF. Both printers are connected to the same print device at LPT1. You have set the priorities on the STAFF printer to 50 and the STUDENTS printer to 1. You grant the Everyone group Print permissions for both. What would you do to prevent users in the STUDENTS Domain Local group from printing to the STAFF printer?
A: Deny the STUDENTS Domain Local group Print permissions for the STAFF printer.
Users report that they are unable to access shared folders on one of your servers. When you open Disk Management you see that DISK3, where these folders are located, is offline. You confirm that the disk has power and that the SCSI adapter is functioning. What should you try first?
A: Reactivate Disk3.
You are installing Windows 2000 Server on a new computer that has a hardware RAID array, a floppy drive and a CD-ROM drive. The RAID disk controller is not on the HCL. You run setup by using the CD-ROM. When the computer restarts you receive a STOP error: "INACCESSIBLE_BOOT_DEVICE". What should you do?
A: Restart Setup from the CD-ROM.
Install a driver from the RAID controller from a floppy disk.
You have both Windows 2000 Servers and NetWare Servers on your network. The NetWare clients all use the IPX/SPX protocol only. You install a database server on a Windows 2000 machine called DB1. This computer has NWLINK and uses the 802.2 frame type and a network number of 77. The NetWare clients on the same subnet can access DB1. However, NetWare clients on other subnets cannot. What should you do?
A: Configure the other NetWare clients to use network number 77.
Omega Corp has 2 offices called North and South. The server in the North office is called north.omega.com. The one in the South office is called south.omega.com. Both offices backup applications, data, and system state data which is stored in the North office. You need to restore the system state data to south.omega.com. What should you do?
A: Ship the south.omega.com backup tapes to the South office.
Run Windows backup on south.omega.com and restore system state data.
Your network includes Win 2000, Win NT 4.0, Win 95 and UNIX clients. You have a Windows 2000 print server called PRINT1. If your UNIX clients support the LPR printing protocol, how would you make PRINT1 available to them?
A: Install Microsoft Print Services for UNIX on PRINT1.
Your company adds a new application to the network that reads and writes large image files to a server for 100 of your users. When they all use the application simultaneously, the application has a slow response time. There are more than 12,000 users in the domain where the imaging server resides, but none of them are reporting any problems. How could you use System Monitor to discover the cause of this problem?
A: Log the Avg. Disk Queue Length counter for the PhysicalDisk object.
How would you determine if you needed to defragment a 12-GB, FAT32 disk?
A: Use Disk Defragmenter to analyze the disk.
You have Windows 2000 clients that use only TCP/IP. You also have Win 3.1 clients that use NetBEUI. You install a new Windows 2000 server and configure it for TCP/IP and NetBEUI. All clients are able to connect. However, when you check network resources on the server, you notice a delay before the server list is returned. What should you do?
A: Disable NetBEUI from the Client for Microsoft Networks setting in the Advanced settings on the adapter.
You have Windows 2000 clients that use only TCP/IP. You also have Win 3.1 clients that use NetBEUI. You install a new Windows 2000 server and configure it for TCP/IP and NetBEUI. The Win 3.1 clients can connect, but the Windows 2000 clients cannot. What should you check?
A: Ensure that NetBIOS over TCP/IP is enabled in the Advanced TCP/IP settings.
You install COM+ applications on 2 of your Windows 2000 servers. How would you ensure that the Component Services Class Registration database is included in your normal backup?
A: Backup the
You have been instructed to implement auditing for the domain of which you are the administrator. The domain is on a network that uses a Windows 2000 Server computer and Windows 2000 Professional client computers.
After determining the best way to implement auditing for the domain, you determine you need to create an audit policy.
How will you implement the audit policy?
a. Create a separate audit policy for each domain controller in the domain
b. Create a separate group policy for each domain controller in the domain
c. Create a group policy that will apply to all domain controllers in the domain
d. Create an audit policy that will apply to all domain controllers in the domain
You use Setup Manager to create an answer file for an unattended installation of Windows 2000 Server. Which components can you specify using Setup Manager? (Choose all that apply.)
a. Create Txtsetup.oem files
b. Configure network settings
c. Create a subfolder in the distribution folder
d. Configure the installation to install IIS
e. Define user name options such as creating a Uniqueness Database File to access a file of valid computer names
You must properly configure Internet Information Service (IIS) ports on your Windows 2000 server to meet the following requirements:
You must configure the proper port so you can control a router via Telnet.
You must configure the proper port so all clients can connect to a secure HTTP server.
You must prevent users from accessing newsgroups.
You must configure the proper port for HTTP service to all clients.
You take the following actions:
You open port 80 on the IIS server.
You block port 119 on the IIS server.
You open port 23 on the IIS server.
You open port 443 on the IIS server.
Which requirements do the actions meet? (Choose all that apply.)
a. The IIS service is configured properly so all clients can use HTTP
b. The IIS service is configured so the router can be configured via Telnet
c. The IIS service is configured so all clients can connect to a secure HTTP server
d. The IIS service is configured properly so all clients are prevented from accessing newsgroups
You have a Pentium III 400 MHz Windows 2000 Server computer with a built-in sound card on the motherboard. You must install a high-end sound card that is on the HCL and enable it on the server. How should you configure the computer to use the new sound card and install the drivers for the sound card? (Choose three.)
a. Disable the sound card in the CMOS
b. Install the new sound card into the computer
c. Disable the integrated sound card in Device Manager
d. Use the Add/Remove Hardware Wizard and manually install the sound card
e. Install the driver from the Driver tab of the existing sound card's Properties page in the Device Manager
f. Let Windows 2000 automatically detect the new sound card during the next boot of the computer after the sound card is installed
You are the head of the MIS department of your company. You are required to travel about 25% of the time to various remote locations. The corporate office network consists of 17 Windows 2000 domain controllers that use the Cluster Service. One of the domain controllers has Terminal Services and Routing and Remote Access installed on it. When you travel, you must be able to edit the registry of the Windows 2000 server at the corporate office while using a remote access connection from a laptop computer. How can you configure this functionality?
a. Use WINS to edit the registry
b. Use Terminal services to edit the registry
c. Use Routing and Remote Access to edit the registry
d. Use Routing and Remote Access to connect to the Terminal Server and edit the registry
Your Windows 2000 server runs three 16-bit applications. The applications have their default installation settings and were installed in Windows NT 4.0. The Windows NT 4.0 server was then migrated to Windows 2000. You want to monitor the performance of these applications using the Process Performance object of Performance Monitor. How can you monitor these applications?
a. Monitor the %Processor Time counter
b. Monitor the %Privileged Time counter
c. Monitor the NTVDM for each application
d. Monitor a single Windows Virtual DOS machine
You have a hard disk fail in your Windows 2000 server. The disk was part of a RAID level 1 configuration. You replace the hard disk with an identical disk. How can you restore the RAID 1 volume?
a. Reactivate the disk
b. Recreate the volume
c. No action is necessary
d. Scan the volume for changes
A Windows 2000 domain controller has two Pentium III processors in it and you are required to assign the Exchange.exe process to one of the processors exclusively. How can you perform this function?
a. This configuration is not possible
b. Right-click the Exchange process, select Set priority, and select Low
c. Right-click the Exchange process, select Set priority, and select High
d. Right-click the Exchange process, select Set priority, and select Realtime
e. Right-click the Exchange process, select Set Affinity, and select the approptiate processor
Your company is adding 75 Windows 2000 servers to your network. The servers are Pentium II 400 MHz with 514 MB of RAM and five 30-GB SCSI hard drives. They have 100-Mbps Ethernet cards and writable CD-ROM drives. You are in charge of deploying Windows 2000 Server on these computers. After formatting a partition and establishing network connectivity, you must install the software via an unattended installation. You must specify a Uniqueness Database File (UDF) and an answer file. How can you configure the answer file? (Choose all that apply.)
a. Use Notepad to create the answer file unattend.txt
b. Use notepad to create the answer file unattend.msi
c. Use Setup Manager to create the answer file unattend.msi
d. Use Setup Manager to create the answer file unattend.txt
You must implement a 140-node network. You must divide the network into 10 subnets and each subnet must be able to accommodate up to 14 nodes. How should you configure the IP addressing structure to allow for this configuration if the company's IP address is 194.194.194.0?
a.
b.
c.
d.
You administer a Windows 2000 network that uses the Encrypting File System (EFS) to encrypt data. You are installing a new server that has a 6-GB NTFS partition.
You want to move several EFS folders to a new server and preserve encryption throughout the migration.
What is the best way to accomplish this task?
a. Compress the folder by enabling file compression
b. Decrypt, move, and re-encrypt the folder using EFS
c. Back up the folder using the Backup utility in Windows 2000
d. Decrypt the folder and compress the folder by enabling file compression
e. Decrypt the folder and back up the folder using the Backup utility in Windows 2000
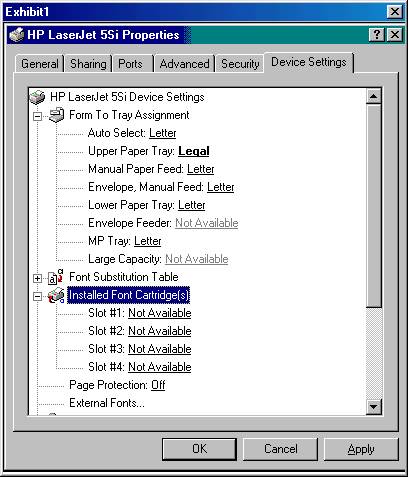
Your Windows 2000 network consists of 10 Windows 2000 Professional computers and a Windows 2000 domain controller running Windows 2000 Server. All the users of the Windows 2000 Professional computers are attorneys, paralegals, or administrative assistants, and they must print to various types of forms. Your network has a single Hewlett Packard 5SI printer on it. You must configure the printer as follows:
All legal-sized documents print to the printer's upper tray.
All letter-sized documents print to the lower tray.
The print mode is specified as PCL and a separation page is configured to print before printing each document.
All members of the Attorneys group have the minimum permissions required to print to the printer.
You take the following actions:
You set up the HP LaserJet 5SI Properties for Device Settings as shown here:
You set up the HP LaserJet 5SI Properties for printing as shown here:
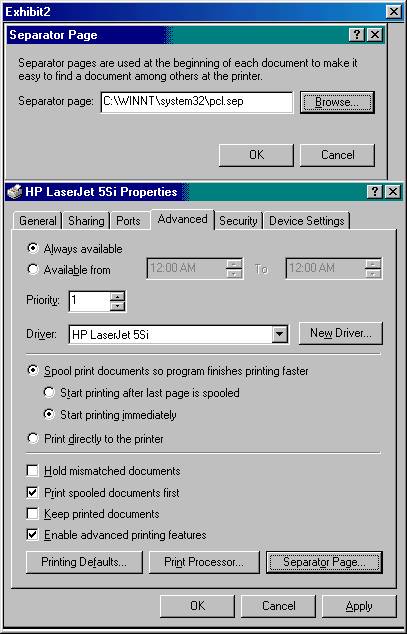
You assign the Attorneys group Modify permissions to the printer.
Which requirements are met by the actions? (Choose all that apply.)
a. All letter-sized documents print to the lower tray
b. All legal-sized documents print to the printer's upper tray
c. All members of the Attorneys group have the minimum permissions required to print to the printer
d. The print mod is specified as PCL and a separation page is configured to print before printing each document
You are in charge of upgrading 100 Windows NT 4.0 servers to Windows 2000 servers by implementing an unattended installation that meets the following requirements:
You must upgrade the existing software from Windows NT 4.0 to Windows 2000 Server.
You must copy the source files to the computer's F: drive.
You must specify the location for the L: drive as the drive for the network share since it contains the I386 directory.
You must specify a reboot 15 seconds after copying files to continue setup.
You must specify the L: drive as the location for the unattend.txt file.
You take the following action:
On the Run line, you type:
Winnt32.exe /s:L:I386 /unattend 15:L:unattend.txt /tempdrive:F.
Which requirements does the command meet? (Choose all that apply.)
a. The command copies the source files to the computer's F: drive
b. The command specifies the L: drive as the location for the unattend.txt file
c. The command specifies a reboot 15 seconds after copying files to continue setup
d. The command successfully upgrades the existing software from Windows NT 4.0 to Windows 2000 Server
e. The command specifies the location for the L: drive as the drive for the network share since it contains the I386 directory
You are the administrator for your company's Windows 2000 domain. You have several Windows 2000 Server computers that have the Windows Internet Name Service (WINS) installed. Your WINS servers have both dynamic and static mappings.
Recently your NetBIOS name requests have experienced some problems. Upon investigation, you discover that some static WINS entries are causing problems for some dynamic entries.
In the Replication Partners Properties dialog box, you check the Enable Migrate box.
Which result does this action achieve?
a. It scavenges the WINS database
b. It enables WINS to overwrite static records with dynamic records
c. It deletes all dynamic mappings and allows only static mappings from this point forward
d. It deletes all static mappings and allow only dynamic mappings from this point forward
You are the administrator for a Windows 2000 network that is configured for remote access (RAS), Active Directory, and Group Policies. The network uses only Windows 2000 Server computers and Windows 2000 Professional client computers.
You are making configuration changes to the user account properties. You decide to set the Always Callback To option in the Properties dialog box.
Why did you make this change?
a. To enable dial-in settings
b. To disable dial-in settings
c. To specify the telephone number that the user must dial in to
d. To specify that the RAS server calls back the user to a specified telephone number
Your company has its central headquarters
in downtown
The employee in the satellite office must post payments only on the corporate network's accounting software.
The connection to the corporate office from the satellite office must be very inexpensive.
The satellite office must connect to the network through the Internet.
Entire IP datagrams transferred from the satellite office to the corporate network must be encapsulated and encrypted to ensure data security.
You take the following actions:
You implement a Virtual Private Network (VPN) connection between the Windows 2000 domain controller and the Windows 2000 Professional workstation.
You assign the satellite office user the appropriate permissions to connect and use the accounting software.
You implement the VPN with the IPSec protocol using the ESP Tunnel Mode.
You use a dial-up ISP to form the connections on both sides.
Which requirements do the actions meet? (Choose all that apply.)
a. The satellite office connects to the network through the Internet
b. Entire IP datagrams are encapsulated and encrypted to ensure data security
c. The connection to the corporate office from the satellite office is inexpensive
d. The employee in the satellite office can post payments on the corporate network's accounting software
You are the administrator for a Windows 2000 Server network. The network contains a Windows 2000 native-mode domain. The server is set to use the default remote access policy.
You are setting up new user accounts on the domain. You want the Remote Access Permissions for the user accounts to be set to automatically allow access.
What should you do to ensure this setting?
a. Do nothing. Allow access is the default setting
b. Change the setting from Deny access to Allow access
c. Change the setting from Deny remote access permission policy to Allow access
d. Change the setting from Control access through Remote Access Policy to Allow access
As the network administrator, you must upgrade three Windows NT 4.0 Server computers (1 PDC and 2 BDCs) to the Windows 2000 Server operating system. The current servers have Windows NT 4.0 RAID level 1 implementations. You must meet the following requirements during the upgrade process:
You must install the new operating system and implement a RAID level 1 configuration under Windows 2000.
You must upgrade to Windows 2000 using the company network.
You must upgrade a Windows NT 4.0 Workstation computer to Windows 2000 Server.
You must provide support on all servers so all distributed applications can use the HTTP protocol to communicate through Internet Information Services (IIS).
You take the following actions:
On the Windows NT 4.0 Server computers and the Windows NT 4.0 Workstation computers, you upgrade the servers by connecting to the network shared CD-ROM drive g:i386winnt32.exe.
On the Windows 2000 servers, you install the following optional components:
All Management and Monitoring tools
Microsoft Script Debugger
Remote Installation Services
Remote Storage
Networking Services- COM Internet Services Proxy
Internet Information Services (IIS).
Which requirements do the actions meet? (Choose all that apply.)
a. The upgrade will take place using the company network
b. The Windows NT 4.0 Workstation computer will be upgraded to Windows 2000 Server
c. The RAID level 1 configuration will be in place in the Windows 2000 operating system
d. Support is provided on all servers so all distributed applications can use the HTTP protocol to communicate through IIS
You must back up the registry and all user data on a Windows 2000 Active Directory domain controller. How can you back up the appropriate files while minimizing the time the backup requires?
a. Use Windows Backup to back up the System State Data
b. Use Windows Backup to perform a full system back up
c. Use Windows Backup to create a differential back up
d. Use Windows Backup to create a backup of specified folders
As the Windows 2000 Server administrator, you must configure the server's hard drive configuration. The Pentium III 500 MHz server with 256 MB of RAM has two 10-GB hard drives and a 1.6 GB hard drive. The hard drive configuration is as follows:
C:- 2-GB FAT RAID Level 1 partition
D:- 999-MB NTFS RAID Level 5 partition
E:- CD-ROM
F:- 500-MB FAT32 striped set
G:- 13.66-GB FAT32 spanned volume
You must store all user data on the drive configuration that can recover if any single disk in the computer fails.
You must store the paging file on the disk configuration with the fastest write access.
You must store accounting data on the hard drive that can recover if either Disk 0 or Disk 1 fails.
You must store confidential data on the hard drive configuration that prevents unauthorized users from accessing information locally even though they have local access to the server.
The RAID configuration is shown here:
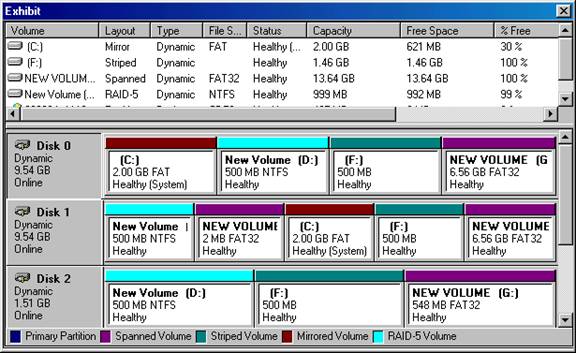
You take the following actions:
You store the user data on drive D:.
You store the paging file on drive G:.
You store the accounting data on drive C:.
You store the confidential data on drive D:.
Which data is properly stored on the computer by the actions? (Choose all that apply.)
a. User Data
b. Paging File
c. Accounting Data
d. Confidential Data
After the installation of Windows 2000 Server, you notice that the dependency service fails to start. How can you resolve this error? (Choose two.)
a. Verify the local computer name is unique to the network
b. Verify the proper domain name is used during the installation
c. Ensure the proper protocol and network adapter are configured in Network Settings
d. Ensure the target partition has sufficient free space for the Windows 2000 Server installation
You must install Windows 2000 on a new computer. The computer has four 20-GB disks. You must configure the system partition to be as large as possible on this Pentium III 667 MHz computer with 512 MB of RAM. For the remainder of the drive configuration, you want a single drive letter assigned to all the existing space. You do not want to implement any type of RAID configuration on the computer. How should you configure the system partition during the setup phase of Windows 2000?
a. Configure the system partition as a 4-GB partition
b. Configure the system partition as a 2-GB partition
c. Configure the system partition as a 20-GB partition
d. Configure the system partition as a 7.8-GB partition
You are the Windows 2000 network administrator for a stock brokerage firm. The 65 stockbrokers on site use Windows 2000 Professional computers as their workstations, and there are two Windows 2000 domain controllers that serve these clients. Due to the sensitive nature of the information, your company policy requires all trade information to be stored on one of the two domain controllers. Each domain controller has five 10-GB hard drives on it. The user information is stored on a striped set of four of the hard drives, and the system uses the other hard drive. The striped set is backed up every evening. You must configure disk quotas as follows:
You must limit disk storage space to 300 MB.
An event must be logged when the users approach 95% of their used space.
You must allow the user to exceed the quota limit.
An event must be logged when the users exceed their specified quota limit.
You take the following actions:
You configure the quota as shown below:
Which requirements are met by the quota configuration? (Choose all that apply.)
a. Users can exceed their quota limit
b. User disk space quota limits are 300 MB
c. An event is logged when the user exceeds their quota limit
d. An event is logged when the user exceeds 95% of their quota
You are the administrator for a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers. The network uses Active Directory with Group Policies. You want to begin the implementation of the Encrypting File System (EFS) on the network and client computers to encrypt all data files stored on the network.
You decide to use the Cipher command-line utility from a command prompt to encrypt a folder on one of the client computers. From the client computer, you open a command prompt screen. You want to encrypt the Administrator's My Documents folder on the C: drive of the client computer.
Which line will encrypt the folder?
a. Cipher /a "C:Documents and SettingsAdministratorMy Documents"
b. Cipher /a "C:Documents and SettingsAdministratorMy Documents"
c. Cipher /h "C:Documents and SettingsAdministratorMy Documents"
d. Cipher /k "C:Documents and SettingsAdministratorMy Documents"
In Device Manager on your Windows 2000 server, you notice a red X next to the U.S. Robotics 56K Voice PCI modem. How can you resolve this problem using Device Manager?
a. Right-click on the device and select Troubleshooter
b. Right-click on the device, select Properties, and on the General tab of the device's Properties page select Use This Device (enable) under the Device usage section of the page
c. Using the left pane of the two-pane Device Manager display, right-click on Device Manager on Local Computer, select View, select Devices by Connection, and expand the IRQ section in the right pane
d. Using the left pane of the two-pane Device Manager display, right-click on Device Manager on Local Computer, select View, select Resources by Connection, and expand the IRQ section in the right pane
You must implement a 17,000-node network. The network will consist of forty Windows 2000 domain controllers, twenty Windows 2000 servers, 60 Hewlett Packard 5SI printers, and 17,000 Windows 2000 Professional workstations. Your company has been assigned an IP address of 136.18.32.0. You expect the network to double in size to approximately 34 subnets with 1000 nodes per subnet in the next two years. How should you configure the IP addressing structure to allow for this configuration?
a.
b.
c.
d.
You administer a Windows 2000 network that uses Active Directory and Group Policies. The network uses only Windows 2000 Server computers and Windows 2000 Professional client computers. The network also uses the Encrypted File System (EFS) to encrypt and protect files and folders.
You are performing routine maintenance on some of the client computers. You need to ensure that the users are using file encryption properly. You want to display the encryption state of the files in the directory you are currently accessing.
How can you accomplish this using the Cipher command-line utility?
a. Cipher
b. Cipher /s
c. Cipher /h *
d. Cipher /h *.*
As the network administrator of a Windows 2000 network, you must secure the E:Confidential folder on your Windows 2000 domain controller. The domain controller has three 10-GB SCSI hard drives in it. The partitions are composed of a 10-GB NTFS partition (C:), a 5-GB RAID level 1 configuration (D:), and two 5-GB FAT32 partitions (E: and F:). You must encrypt all information in the E:Confidential folder. How can you encrypt the folder?
a. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the "Folder is ready for Archiving" box is selected
b. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the "Encrypt contents to secure data" selection box is selected
c. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the "For faster searching allow Indexing Service to Index the folder" box is selected
d. Convert the drive to an NTFS partition. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the "Encrypt contents to secure data" selection box is selected
Using Task Manager's Processes tab, you must monitor the following process settings:
The total processor time a process has used the processor since it started.
The ranking of a process which determines the order in which the process uses the processor.
Select the two boxes which will monitor the above information.
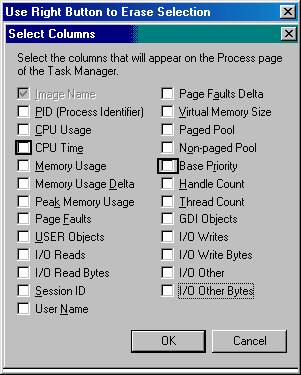
You are installing a new network adapter for a Windows 2000 Server computer on the Windows 2000 network you administer. You complete the installation and install the device drivers.
Which function will notify you whether the driver you are installing passes the Microsoft certification process?
a. Event Logs
b. Driver Signing
c. Device Manager
d. Service Pack Slipstreaming
You are the administrator of your Windows NT 4.0 network, and you must migrate the network to Windows 2000. The network has four Windows NT 4.0 servers. The servers have the configurations shown below:
Server_1 is a Pentium 200 MHz computer with 256 MB of RAM and a 2-GB FAT partition.
Server_2 is a Pentium III 350 MHz computer with 64 MB of RAM and a 10-GB NTFS partition.
Server_3 is a Pentium 100 MHz computer with 512 MB of RAM and a 6-GB NTFS partition.
Server_4 is a Pentium III 650 MHz computer with 2 GB of RAM and a 2-GB FAT partition.
You take the following actions to migrate to Windows 2000:
You type the Winnt32.exe command from the Run line of Server_1, Server_2, and Server_4.
You upgrade the processor of Server_3 to a Pentium 133 MHz processor and type the Winnt32.exe command from the Run line on the server.
Which computers will the actions upgrade properly? (Choose all that apply.)
a. Server_1
b. Server_2
c. Server_3
d. Server_4
You are the administrator for a Windows 2000 network that uses Active Directory and Group Policies. The network consists of a DNS server. In addition, auditing is used to track events.
You are making configuration changes to the audit policy. You have decided to audit access to all files and folders on the C: drive.
How can you implement this change? (Choose two.)
a. Enable the Audit Object Access policy
b. In the audit policy, enable Audit Directory Service Access
c. Enable auditing for all the files and folders on the C: drive
d. Add an audit policy from the server for the computer containing the specific files and folders
A hard disk fails in your Windows 2000 server. The disk was part of a RAID level 5 configuration. You replace the hard disk with an identical disk. How can you restore the RAID 5 volume?
a. Reactivate the disk
b. Recreate the volume
c. No action is necessary
d. Scan the volume for changes
You must configure a process to use the maximum available resources on the computer to complete the task. How should you configure the process using Task Manager?
a. Right-click the process, select Set priority, and select Low
b. Right-click the process, select Set priority, and select High
c.
Right-click the process, select Set
priority, and select
d. Right-click the process, select Set priority, and select Realtime
You are the administrator of your Windows 2000 domain controller. The domain controller serves 65 Windows 2000 clients. During the day, there are always four programs running on the domain controller: your accounting software, your Exchange 5.5 service, Word 2000, and Outlook. You must monitor the server as follows:
You must monitor the amount of time the CPU is used by the operating system.
You must view the status of the running applications.
You must view the amount of time the CPU is used by each process.
You must view the percentage of the CPU a process is using at a given time.
You take the following actions:
In the Performance tab of Task Manager, you select View and then you select Show Kernel Times. You then view the amount of time the CPU is being used by the operating system.
In the Applications tab of Task Manager, you view the applications that are active on the domain controller and the status of those applications.
In the Processes tab of Task Manager, you view the amount of time each process uses the CPU and the percentage of the CPU a process is using at any given time.
Which requirements do the actions meet? (Choose all that apply.)
a. You can successfully view the amount of time the CPU is used by each process
b. You can successfully view the status of running applications on the domain controller
c. You can successfully view the percentage of the CPU a process is using at a given time
d. You can successfully monitor the amount of time the CPU is being used by the operating system
You must add 4 Windows 2000 Server computers to your existing network. The network currently has 1 UNIX server, 25 Windows NT 4.0 servers, and 3 NetWare servers. There are 365 Windows 2000 Professional workstations, 400 Windows NT 4.0 Workstation computers, 600 Windows 98 computers, and 500 Windows 2000 laptop computers. You must configure the servers with the following requirements:
You must allow the UNIX server to print to a printer controlled by one of the Windows 2000 servers.
You must allow all client computers to access information on the NetWare servers.
You must configure the Windows 2000 servers so the laptop users can dial in to the network.
You must configure the Windows 2000 domain so it can still use the Windows NT 4.0 BDCs.
You take the following actions:
On all client computers, you install TCP/IP and NWLink.
On the UNIX server, you install an RFC-compliant Line Printer Remote (LPR) service.
On the Windows 2000 servers, you install Print Services for UNIX, the TCP/IP and NWLink protocols, and Gateway Services for NetWare (GSNW). In addition, you install Routing and Remote Access and configure it accordingly.
You configure the Windows 2000 servers to run in mixed mode.
Which requirements are met by the actions? (Choose all that apply.)
a. The Windows 2000 domain can still use the Windows NT 4.0 BDCs
b. The UNIX server can print to the Windows 2000 servers' printers
c. All client computers can access information on the NetWare servers
d. The laptop users can dial in to the network via the Windows 2000 servers
As the Windows 2000 network administrator, you must properly configure the domain controller's hard drive. You have just deleted a spanned volume on the Windows 2000 server, and the current drive configuration is below:
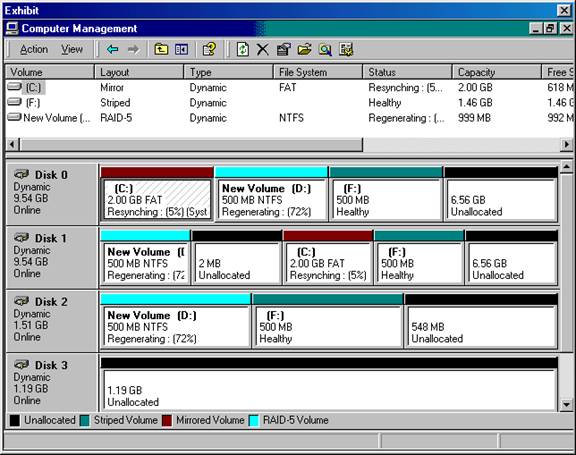
You are required to take this free space and configure it as follows:
You must create 3 GB of storage for a mission critical application and allow the entire 3 GB to be mirrored in case either Disk 0 or Disk 1 fails in the domain controller.
You must create a RAID level 5 configuration so there are 2 GB of space available for storage.
You must back up all volumes that are not fault tolerant.
You must use all remaining free space in a single volume.
You take the following actions:
You create a 3-GB RAID level 1 configuration using Disk 0 and Disk 1.
You create a RAID 5 volume using 1 GB of space on Disk 0, Disk 1, and Disk 3.
You back up disk F and implement a scheduled backup plan for it.
You use all the remaining free space on the disks to create a spanned volume.
Which requirements do the actions meet? (Choose all that apply.)
a. The 3 GB mirrored volume is properly configured
b. All remaining free space is used in a single volume
c. All volumes that are not fault tolerant are backed up
d. The RAID level 5 configuration is properly configured
Due to strict security limitations of your Windows 2000 production environment, you must prevent any unsigned drivers from being installed on any computer in your Windows 2000 network. The network consists of Windows 2000 domain controllers, Windows 2000 file and print servers, and Windows 2000 Professional computers. How can you prevent the installation of any unsigned drivers on all the computers on your network?
a. Implement a Group Policy to Ignore signature verification
b. Configure a Local Policy on the main Windows 2000 domain controller
c. Configure the domain controllers, file and print servers, and client computers to Block unsigned drivers
d. Configure the domain controllers, file and print servers, and client computers to Ignore unsigned drivers
You are the administrator for a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers. The network is configured to use Active Directory and auditing.
You perform regular maintenance on the network. You like to periodically use the Event Viewer to check the success or failure of events that have auditing enabled.
What do you use to monitor these events?
a. System log
b. DNS Server
c. Security log
d. Application log
e. Directory Service
f. File Replication Service
You must take a Windows 98 Pentium III 550 MHz computer and make it a Windows 2000 domain controller. After installing the Windows 2000 operating system, you install a USB scanner on the computer while it is on. How can you force Windows 2000 to search for a new scanner?
a. Restart the computer
b. Log off and back on to the domain controller
c. Right-click on the domain controller's name in Device Manager and select "Scan for hardware changes"
d. This is not possible because Windows 2000 domain controllers do not support adding hardware while the computer is on
You must take a Windows 98 Pentium III 550 MHz computer and make it a Windows 2000 domain controller. After installing the Windows 2000 operating system, you install a USB scanner on the computer while it is on. How can you force Windows 2000 to search for a new scanner?
a. Restart the computer
b. Log off and back on to the domain controller
c. Right-click on the domain controller's name in Device Manager and select "Scan for hardware changes"
d. This is not possible since Windows 2000 domain controllers do not support adding hardware while the computer is on
Your existing TCP/IP network has an address of 194.194.194.0. The network consists of 2 subnets with 60 nodes on one segment and 40 nodes on the other segment. All nodes are either Windows 2000 servers, Windows 2000 Professional computers, or HP 8000 printers using JetDirect cards. There are 3 Windows 2000 domain controllers. You must configure the network as follows:
You must properly subnet your network address.
You must configure the Windows 2000 Professional computers so they are automatically configured with a valid IP address.
You must minimize human error when configuring the computers with the networking information.
You must configure the client computers so they can be moved to another subnet without any modifications.
You take the following actions:
You use the subnet of 194.194.194.0/26.
You configure all Windows 2000 Professional computers as WINS clients.
You configure all Windows 2000 domain controllers as WINS servers and properly configure them.
Which requirements do the actions meet?
a. The network is properly subnetted
b. The client computer can be moved to another subnet without any modifications
c. Human error is minimized when configuring the computers with the networking information
d. The Windows 2000 Professional client computers are automatically configured with a valid IP address
You are the administrator for a Windows 2000 network. The network consists of all Windows 2000 Server and Windows 2000 Professional computers. You need to perform auditing maintenance. You want to accomplish the following goals:
Track successful attempts to create folders.
Track failed attempts to create files.
Track successful attempts to write attributes.
Track failed attempts to read folder permissions.
You perform the following actions:
Open the Properties dialog box for a specific folder.
Select the Security tab and click the Advanced button.
Select the Auditing tab and add an entry with permissions set as indicated below:
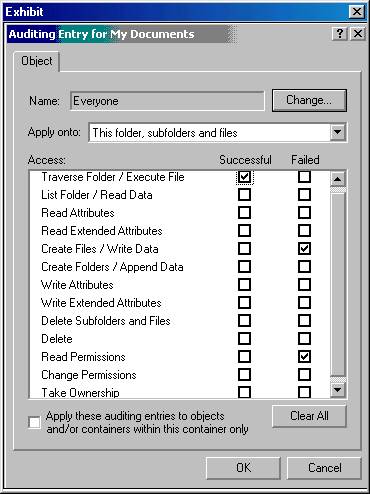
Which goal or goals are accomplished by these actions? (Choose all that apply.)
a. Track failed attempts to create files
b. Track failed attempts to create folders
c. Track successful attempts to write attributes
d. Track failed attempts to read folder permissions
As the network administrator, you must upgrade 3 Windows 98 computers to the Windows 2000 Server operating system. The Windows 98 computers are Pentium III 550 MHz computers with 256 MB of RAM, but they do not have a CD-ROM in them. You must perform an over-the-network install of the operating system. How can you perform this function?
a. Share the installation folder. Boot the computers with an MS-DOS network boot disk.
b. Share the installation folder. Boot the computers with a Windows 98 network boot disk.
c. Share the installation folder. Upgrade the new operating system using the Winnt.exe command.
d. Share the installation folder. Migrate to the new operating system using the Winnt32.exe command from the Run line of Windows 98
You are administering a Windows 2000 network for your company. The network consists of Windows 2000 Server and Windows 2000 Professional computers. The network is configured for Active Directory and includes a DNS server.
You are making routine configuration changes to the network. You are using the Security Configuration and Analysis snap-in.
Which tasks can you perform using this snap-in? (Choose all that apply.)
a. Track events
b. Create group policies
c. Set a working database
d. Import a security template
You are the administrator for a Windows 2000 network. The network is configured with Active Directory and Group Policies. Only Windows 2000 Server and Windows 2000 Professional computers are used on the network.
You need to make some group policy configuration changes. You create a group policy object (GPO) linked to an Organizational Unit (OU). You do not want the GPO to use any policies from the domain.
How can you accomplish this task?
a. Check the "Block Inheritance" box in the main screen of the OU's Group Policy Editor
b. Check the "Apply Group Policy" box in the main screen of the domain's Group Policy Editor
c. Check the "Delete All Child Objects" box in the domain GPO policy's Properties dialog box
d. Check the "No Override" box in the OU GPO's Options dialog box within the Properties dialog box
You are administering a Windows 2000 network. The network uses a DHCP server. The network contains Windows 2000 Server and Windows 2000 Professional computers.
You are implementing DHCP leasing on new client computers. While testing the configurations, TCP/IP is initialized for the first time. This starts the DHCP lease process.
What is the first step in this process?
a. DHCPACK
b. DHCPNACK
c. DHCPOFFER
d. DHCPREQUEST
e. DHCPDISCOVER
You must configure a client's subnet mask and default gateway. All subnets on the network use a /24 subnet addressing scheme. The router that connects the subnet to the network has an IP address of 158.25.64.1. The next router in line has an IP address of 158.23.65.2. Which subnet mask and default gateway should you use to configure the client computer?
a.
158.25.64.1
b.
158.23.65.2
c.
158.25.64.1
d.
158.23.65.2
You are administering a Windows 2000 network. The network uses Active Directory and Group Policies. The network consists of a DNS server and uses auditing to track events.
You are making configuration changes to the audit policy. You have decided to enable auditing for an additional event. After making the change, how will it begin to take effect? (Choose all that apply.)
a. By restarting the computer
b. By typing Secedit at a command prompt
c. From a regularly scheduled policy propagation
d. By logging off and logging on to the computer
e. By typing RefreshPolicy machine_policy at a command prompt
You are the administrator for your company's Windows 2000 domain. Your network consists of a Windows 2000 Server Primary Domain Controller (PDC) and 200 Windows 2000 Professional client computers. The network uses static IP addresses. The network connects to the Internet over a T1 line, as shown below:
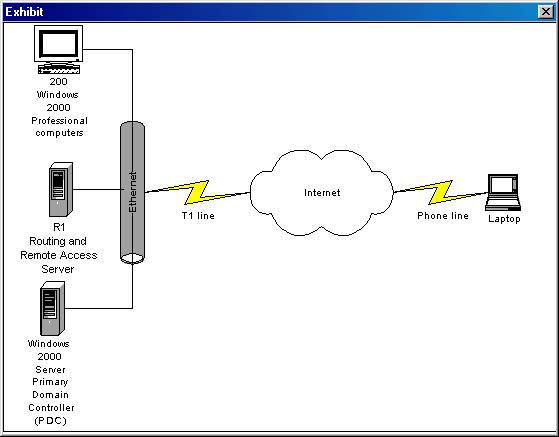
You set up a Routing and Remote Access Server, named R1, on your domain to allow access to your Virtual Private Network (VPN) resources.
Your company's salesmen use laptop computers while on the road. One of the salesmen can connect to the Internet through a local ISP and wants to connect to the company VPN. After configuring all of the appropriate components, he informs you that he cannot communicate with the VPN.
From a Windows 2000 Professional client computer on the domain, you ping R1 and receive a reply. You then discover that another computer on the domain has the same IP address as R1. How might you have discovered this problem?
a. By using the RSH utility
b. By using the Netsh utility
c. By using the Telnet utility
d. By using the IPCONFIG utility
You have four 10-GB disks in your Windows 2000 server. You are trying to provide the maximum usable space while still providing for redundancy in case a single disk in the drive fails. How should you configure the hard drives to meet these requirements?
a. Create two Raid Level 1 volumes
b. Create two Raid Level 5 volumes
c. Use all four disks to create a single RAID level 5 volume
d. Use all four disks to create a single RAID level 1 volume
As the Windows 2000 network administrator, you must enforce quota limits on disk storage space on the Windows 2000 domain controller. The domain controller has 3 GB of space for user storage, and there are only about 15 users that store information on the server. You must meet the following requirements:
You must enforce disk quota limits on your account, but you must still be able to install applications on the server without this space being added to your disk quota limit.
You need to be able to monitor usage of the free space so you can know when you need to modify the server's hardware configuration. In monitoring this, you must not prevent any user from saving data.
You must delete several users from the volume since they are no longer employed by your company.
You must log an event when a user exceeds their quota limit.
You take the following actions:
In your day to day activities you use your user account, but when you add applications to the server, you log on as the administrator.
You ensure the 'Deny Disk Space to Users Exceeding Quota Limit' check box is cleared.
You delete or transfer ownership to another user for all files owned by the former employees and then delete their quota entries.
Which requirements do the actions meet? (Choose all that apply.)
a. An event is logged when a user exceeds their quota
b. You successfully delete the former employees' quotas
c. Applications installed using the Administrator account will not be charged to your quota limit
d. You can monitor the usage of free space so you can plan for hardware modification without preventing users from saving data
In Device Manager on your Windows 2000 server, you notice a yellow question mark next to the Realtek RTL8139 PCI Fast Ethernet NIC. You suspect the problem is due to an IRQ conflict. How can you troubleshoot the problem with this device using Device Manager?
a. Right-click on the device and select Troubleshooter
b. Right-click on the device, select Properties, and on the General tab of the device's Properties page, select Troubleshooter
c. Using the left pane of the two-pane Device Manager display, right-click Device Manager on the Local Computer, select View, select Devices by Connection, and expand the IRQ section in the right pane
d. Using the left pane of the two-pane Device Manager display, right-click Device Manager on the Local Computer, select View, select Resources by Connection, and expand the IRQ section in the right pane
You must implement a 250-node network. You must divide the network into 2 subnets and each subnet must not exceed 125 nodes. How should you configure the IP addressing structure to allow for this configuration if the company's IP address is 194.194.194.0?
a.
b.
c.
d.
You are the administrator for a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers. The network also uses a DHCP server.
You are testing the DHCP lease process between the DHCP clients and the server. You receive a broadcast of a DHCPNACK on the DHCP client.
When does this broadcast take place?
a. After the DHCPOFFER message is broadcast
b. After the DHCPREQUEST message is broadcast
c. When a client attempts to lease its previous IP address, and the IP address is not longer available
d. When the IP address is invalid because the client computer was moved to a different location within the subnet
You administer a domain on a Windows 2000 network. The network uses Active Directory, and contains a DNS server. The network consists of all Windows 2000 Server computers and Windows 2000 Professional client computers.
You have decided to implement roaming user profiles. You came to this conclusion based on numerous complaints from users that wanted to access their files and folders from different computers.
Which steps must you take to accomplish this task? (Choose two.)
a. Create a shared folder on a server
b. Create a read-only folder on a server
c. Create a non-shared folder on a server
d. From the Profile tab in the Properties dialog box of the user accounts, enter the path to a shared folder
e. From the Profile tab in the Properties dialog box of the user accounts, enter the pat to a read-only folder
f. From the Profile tab in the Properties dialog box of the user accounts, enter the path to a non-shared folder
You must upgrade a Windows NT 4.0 Workstation computer to the Windows 2000 Server operating system. Once the upgrade is complete, you must implement a RAID level 5 configuration and you must provide support on the upgraded server so all distributed applications can use the HTTP protocol to communicate through Internet Information Services (IIS). How can you configure the server so Windows 2000 Server is the only operating system on the computer? (Choose all that apply.)
a. Install Windows 2000 Server by connecting to the shared CD-ROM using the F:i386Winnt32.exe command. Then implement RAID level 5 on the server.
b. On the Windows 2000 server, install the following optional components:
All Management and Monitoring tools
Microsoft Script Debugger
Remote Installation Services
Remote Storage
Networking Services- COM Internet Services Proxy.
c. On the Windows 2000 server, install the following optional components:
All Management and Monitoring tools
Microsoft Script Debugger
Remote Installation Services
Remote Storage
Networking Services- COM Internet Services Proxy
Internet Information Services (IIS).
d. Format the hard drive of the workstation. Install a client so you can obtain access to a network shared CD-ROM, install Windows 2000 Server by connecting to a shared CD-ROM using the F:i386Winnt.exe command. Then, implement a RAID level 5 configuration on the server.
Your network has a Windows 2000 Active Directory server and a UNIX server. You must allow the UNIX server to print to a printer connected to the Active Directory server. How must you configure the network adapter on the LAN connection so this functionality is allowed on the Active Directory server? (Choose all that apply.)
a. Install the DLC protocol
b. Install Print Services for UNIX
c. Install TCP/IP
d. Install Client for Microsoft Networks
e. Install File and Print Sharing for Microsoft Networks
You are the administrator for a Windows 2000 network. The network is configured to use Active Directory and Group Policies. The network contains a DNS server and DHCP server.
You need to make changes to the security configurations stored in the network. These configurations are stored in security templates on the domain controller.
What can you access to make these changes?
a. Security Templates snap-in
b. Security Configuration and Analysis snap-in
c. Active Directory Sites and Services snap-in
d. Active Directory Users and Computers snap-in
You must back up the Registry, the COM+ Class Registration database, the system boot files, the Certificate Server database, the Active Directory Services database, and the SYSVOL directory on a Windows 2000 Active Directory domain controller. The domain controller is a Pentium 200 MHz with a RAID 5 array composed of ten 3-GB partitions. How can you back up the appropriate files while minimizing the time the backup takes?
a. Use Windows Backup to perform a full system backup
b. Use Windows Backup to create a differential backup
c. Use Windows Backup to back up the System State Data
d. Use Windows Backup to create a backup of specified folders
You are administering a Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers.
You need to configure some settings for the network adapter in one of the server computers. You want to use the tools that Windows 2000 provides for managing the device.
Where can most of these tools be found?
a. The General tab of the System Properties dialog box
b. The Advanced tab of the System Properties dialog box
c. The Hardware tab of the System Properties dialog box
d. The Network Identification tab of the System Properties dialog box
You are the administrator for a Windows 2000 network that uses Windows 2000 Server computers and Windows 2000 Professional client computers. The network is configured to use Active Directory and Group Policies.
You find out that one of the Windows 2000 Server computer's local group policy settings is incorrect according to your company's standards. The administrator before you changed the permissions for the local group policy. You want the permissions set back to the defaults.
Where will you access these permissions and how should the permissions be set?
a. Use the WINNTSystem directory, and set the permissions to:
Administrators = Read, Write, and Modify
SYSTEM = Full Control
Authenticated Users = List Folder Contents.
b. Use the WINNTSystem32 directory, and set the permissions to:
Administrators = Read, Write, and Modify
SYSTEM = Full Control
Authenticated Users = Read, and List Folder Contents.
c. Use the WINNTSystem directory, and set the permissions to:
Administrators = Full Control
SYSTEM = Read, Write, and Modify
Authenticated Users = Read and Execute, and List Folder Contents.
d. Use the WINNTSystem32GroupPolicy directory, and set the permissions to:
Administrators = Full Control
SYSTEM = Full Control
Authenticated Users = Read and Execute, List Folder Contents, and Read.
As the network administrator, you create an Organizational Unit (OU) with a child OU named ENGUSERS. The child object must have explicit rights assigned to it, but the OU's permissions must propagate to the OU and all its other child objects. How can you configure this functionality on the Active Directory-enabled Windows 2000 server? (Choose all that apply.)
a. Configure permission inheritance on the OU
b. Configure permission inheritance on the OU and all child objects
c. On the child object with explicit rights, use the Security tab and clear the check box to Allow Inheritable Permissions From Parent to Propagate To This Object
d. On the child object with explicit rights, use the Security tab and select the check box to Allow Inheritable Permissions from Parent to Propagate To This Object
Your Windows 2000 server has 2 IDE 15-GB hard drives in it. Each drive has 3 partitions on it. The system partition is the first partition on the first hard drive and it is replicated to the second partition on the second drive using a RAID level 1 configuration. The first hard drive fails and you must edit the Boot.ini file so the system partition uses the replication on the second disk. How should you configure the ARC path?
a. multi(0)disk(0)rdisk(1)partition(2)WINNT="Windows 2000 Server"
b. multi(0)disk(0)rdisk(2)partition(2)WINNT='Windows 2000 Server'
c. multi(0)disk(0)rdisk(2)partition(3)WINNT='Windows 2000 Server'
d. multi(0)disk(0)rdisk(1)partition(3)WINNT='Windows 2000 Server'
As the Windows 2000 network administrator, you must optimize disk space on your Windows 2000 domain controller. There are some folders that must be compressed. You must compress the C:Operations folder and the D:Aged Accounts folder. The C: partition is an NTFS partition and the D: partition is a FAT32 partition. How can you compress the folders? (Choose two.)
a. Right-click on the C:Operations folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Compress contents to save disk space'.
b. Right-click on the D:Aged Accounts folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Compress contents to save disk space'.
c. Convert the D: partition to NTFS, right-click on the D:Aged Accounts folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Compress contents to save disk space'.
d. Format the D: partition, restore the folder from backup, right-click on the D:Aged Accounts folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Compress contents to save disk space'.
You are the administrator for a Windows 2000 network that uses only Windows 2000 Server computers and Windows 2000 Professional client computers. Your company uses the Encrypted File System (EFS) to encrypt files and folders on the network.
You have just installed a new Windows 2000 Professional client computer for a new employee. You need to create a new file encryption certificate on the computer.
Using the Cipher command-line utility, which line will accomplish this task?
a. Cipher /k
b. Cipher /f
c. Cipher /e
d. Cipher /f /q
Your company plans to establish a new Web site. This Web site will allow visitors to download various shareware programs from your FTP site. The network administrator will be responsible for managing the FTP traffic to the site.
Which optional component should you install?
a. Remote Storage
b. Windows Media Services
c. Remote Installation Services
d. IIS
You are the administrator of your Windows 2000 domain controller. The domain controller's hard drive configuration is shown below:
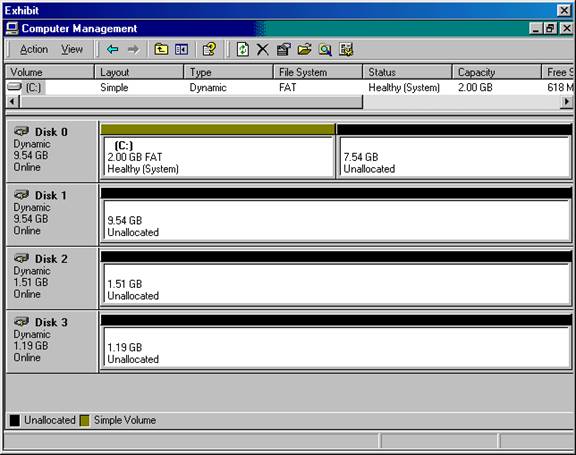
You must configure the hard drives in the server as follows:
You must protect the system partition by creating an exact duplicate of it so if one of the hard drives fails, the system information is still protected.
You must create a disk configuration that has approximately 6 GB of usable hard disk space, and can recover in the event one of the hard drives fails.
You must create a 3-GB disk configuration where you can allow the fastest Read access to the drive possible.
You must create 2 GB of usable space in a RAID level 1 configuration.
You take the following actions:
You mirror the system partition using 2 GB of space from Disk 1.
You create a RAID level 5 configuration using 2 GB of disk space from Disk 0, Disk 1, and Disk 2.
You create a striped set using 1 GB from Disk 0, Disk 1, and Disk 3.
You create a mirrored set using 1 GB of space from Disk 0 and Disk 1.
Which requirements do the actions meet? (Choose all that apply.)
a. A disk configuration is created so 2 GB of usable space is used in a RAID level 1 configuration
b. A 3-GB disk configuration is created where you can allow the fastest write access to the drive possible
c. A disk configuration is created that has approximately 6 GB of usable hard disk space and can recover in the event one of the hard drives fails
d. The system partition is protected by creating an exact duplicate of itself so if one hard drive fails the system information will still be protected
You are a network administrator for your company's Windows 2000 Server network. The network contains a remote access server with dial-in access enabled.
You need to set the profile properties for the default remote access policy. You want to accomplish the following goals:
Disconnect client sessions if the dial-in client is idle for 15 minutes.
Limit client sessions to three hours.
Limit client system
access times to Monday through Friday,
Limit clients to Async modem access.
You perform the following actions:
From the Routing and Remote Access console, you double-click your remote access server.
You open the Properties dialog box for the default remote access policy.
You click the Edit Profile button.
You make the changes as shown below:
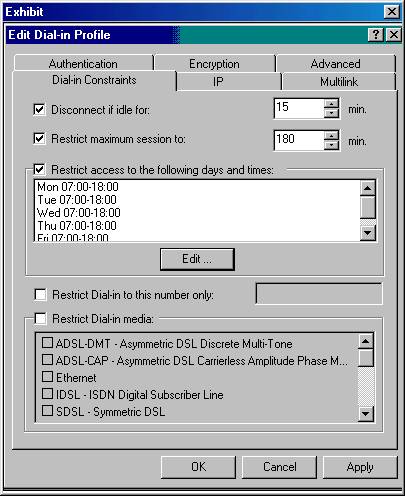
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Limit clients to Async modem access
b. Limit client sessions to three hours
c. Disconnect client sessions if the dial-in client is idle for 15 minutes
d. Limit client system access times to Monday through Friday,
As the network administrator of a Windows 2000 network, you must optimize disk performance on five Windows 2000 domain controllers. Each domain controller has five 6-GB SCSI hard drives in them. In addition to the five domain controllers, there are 600 Windows 2000 Professional computers on the network. Your network is a 100BaseT network. You must optimize the domain controllers as follows:
You must implement a plan for optimizing the data on the hard drives at the recommended Microsoft interval so application initialization is optimized.
You must compress all user store information that is located in the main D:User_info folder.
You must provide fast searching capabilities for the D:Data and E:Marketing folders.
You must prevent users from exceeding 50 MB of storage on any single disk in a domain controller.
You take the following actions:
You implement a defragmentation plan the first Sunday of the month on all domain controllers.
You configure the folder compression as shown below:
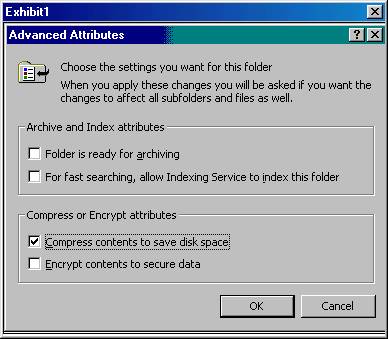
You configure the searching capabilities on the two folders as shown above, except you clear the 'Compress contents to save disk space' check box, and you select the 'For faster searching allow Indexing Service to Index the folder.'
You implement disk quotas as below with Local Disk (D:) Properties at the top on all the disks in all the domain controllers.
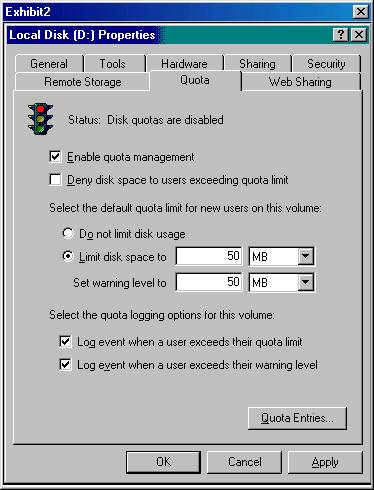
Which requirements do the actions meet? (Choose all that apply.)
a. All user store information located in the main D:User_info folder is compressed
b. The Microsoft recommended plain is implemented to optimize application initialization time
c. Fast searching capabilities for the D:Data and E:Marketing folders are properly provided
d. Users are prevented from exceeding 50 MB of storage on any single disk in a domain controller
As the Windows 2000 network administrator, you must optimize disk space on your Windows 2000 domain controller. There are some folders that must be encrypted. The C: volume in the domain controller is an NTFS volume and is fault tolerant. You must configure the C:Accounting, C:Marketing, C:Downloads, and C:My Documents folder as follows:
You must compress the C:Downloads folder so it requires less disk space.
You must compress and encrypt the C:Marketing folder.
You must encrypt the C:My Documents folder.
You must encrypt the C:Accounting folder.
You take the following actions:
You right-click on the C:Downloads folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Compress contents to save disk space'.
You right-click on the C:Marketing folder in Explorer and select Properties. On the General Tab, you select Advanced, you select the check box to 'Compress contents to save disk space', and the check box to 'Encrypt contents to secure data'.
You right-click on the C:My Documents folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Encrypt contents to secure data'.
You right-click on the C:Accounting folder in Explorer and select Properties. On the General Tab, you select Advanced, then you select the check box to 'Encrypt contents to secure data'.
Which folders are properly configured? (Choose all that apply.)
a. C:Downloads
b. C:Marketing
c. C:Accounting
d. C:My Documents
You are the administrator of your company's Windows 2000 network. One of the Windows 2000 Server domain controllers needs its hardware upgraded to keep up with company standards. You need to upgrade the 10BaseT network card to a 100BaseT network card. In addition, you need to add a 3D sound card, a modem, and a Super VGA video card to your domain controller for videoconferencing capabilities. The domain controller's motherboard has an on-board video card and sound card.
The new video card is not on the Hardware Compatibility List (HCL), but you need to use it.
The new sound card is on the HCL.
The new network adapter is not on the HCL.
The new modem is on the HCL.
You take the following actions to install the software properly:
You configure driver-signing options as below:
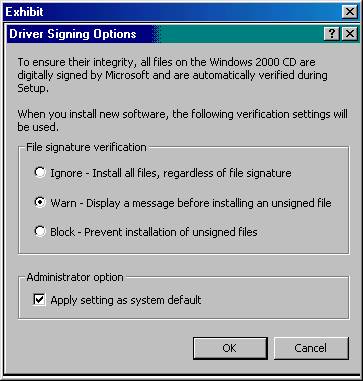
You disable the on-board sound card and video card.
You physically install the hardware into the computer.
You boot the domain controller and install the appropriate drivers.
Which devices will function properly in the domain controller? (Choose all that apply.)
a. Modem
b. Sound card
c. Video card
d. Network adapter
While administering a Windows 2000 network, you and your co-workers decide to implement roaming user profiles for all users on the network. The network uses only Windows 2000 Server computers and Windows 2000 Professional client computers.
In addition to implementing the roaming user profiles, you have decided to implement home folders on the network for the users. When creating the home folders, which permission change is required?
a. The permissions on the folder must be changed from Full Control for the Everyone group to Full Control for the Users group.
b. The permissions on the folder must be changed from Full Control for the Users group to Full Control for the Everyone group.
c. The permissions on the folder must be changed from Write Permissions for the Everyone group to Write Permissions for the Users group.
d. The permissions on the folder must be changed from Write Permissions for the Users group to Write Permissions for the Everyone group.
You are the administrator for a Windows 2000 network. The network uses Terminal Services.
You have decided to deploy applications to the client computers from the domain controller. You have discovered that the original application installation package did not install all of the necessary components to the local disk. What do you need to use in deploying the application from the domain controller?
a. target file
b. transform file
c. installation file
d. initialization file
You are the administrator of a Windows 2000 network. The network has 5 Windows 2000 domain controllers, 17 Windows NT 4.0 servers, 6 NetWare 5.1 servers, and 3 UNIX servers. It also has 600 Windows 95 workstations, 800 Windows 98 workstations, 200 Windows 2000 Professional workstations, and 1500 Windows NT 4.0 workstations. The network uses Microsoft Exchange as its e-mail server and all clients use Outlook 98 as the e-mail client. You have installed Microsoft Exchange on one of the Windows 2000 domain controllers in the volume of the server that provides the best overall performance. Your Exchange server crashes and you look at the domain controller's drive configuration:
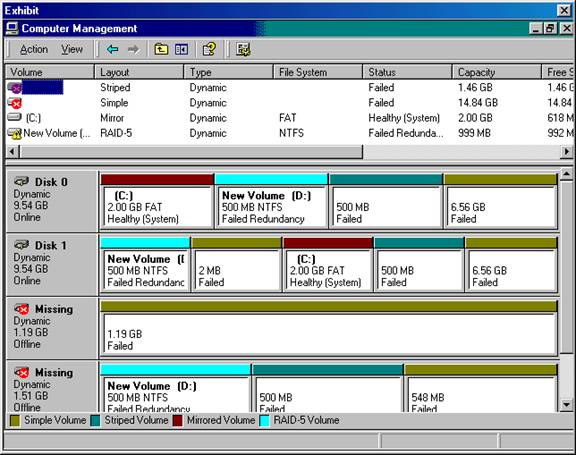
You must meet the following requirements:
You must restore the Exchange information and get the server back up immediately.
You must restore the information on the other hard drive configuration that has failed.
You must replace the failed hard drives.
You must put the server back in the original working order.
You take the following actions:
You install a 1.19-GB hard disk and a 1.51-GB hard disk into the server.
You remove the striped volume and the spanned volume.
You recreate the striped volume and spanned volume exactly as they were originally.
You restore the Exchange backup to the spanned volume.
You restore the backup from the spanned volume into the new spanned volume.
Which requirements do the actions meet? (Choose all that apply.)
a. The failed hard drives are replaced
b. The information on the other hard drive is successfully restored
c. The server is back in the original working order after the actions
d. The Exchange information is successfully restored to its original location
You are configuring Group Policy for your Windows 2000 network. The network uses only Windows 2000 Server computers and Windows 2000 Professional client computers.
You want to create a group policy. You want the policy linked to a site. You must first create a group policy object (GPO).
How can you accomplish this task?
a. Open the Active Directory Sites and Services snap-in. Select the site and open the Properties dialog box. Select the Object tab and enter the object name.
b. Open the Active Directory Users and Computers snap-in. Select the Users node and open the Properties dialog box for Group Policy Creator Owners. Enter a name for the new GPO.
c. Open the Active Directory Sites and Services snap-in. Select the site and open the Properties dialog box. Select the Group Policy tab and click New. Enter a name for the new GPO.
d. Open the Active Directory Users and Computers snap-in. Select the site and open the Properties dialog box. Select the Group Policy tab and click New. Enter a name for the new GPO.
You have recently been hired as one of the network administrators for a Windows 2000 network. The network uses Active Directory and Group Policies, and consists of all Windows 2000 Server computers and Windows 2000 Professional client computers.
You have been training for your new position with one of the administrators. While observing maintenance procedures, the administrator uses the utility Gpedit.msc.
Why did the administrator use this utility?
a. To edit the local GPO
b. To edit the domain GPO
c. To create a new local GPO
d. To create a new domain GPO
After the installation of Windows 2000 Server, the server fails to start and you receive a blue screen error. How can you resolve this error?
a. Increase the amount of memory in the server
b. Verify all hardware is properly detected an on the HCL
c. Create enough free space for the Windows 2000 Server installation on the target partition
d. Replace the CD-ROM drive with one that is on the Windows 2000 Hardware Compatibility List
You want to perform an installation of Windows 2000 Server on three new computers. You must meet the following requirements:
The installation must be performed over the network.
The users must not be able to change any installation options.
The users must be able to use the Recovery Console after installation.
You must specify an optional folder named INSTALL to be installed and not removed with the temporary files after the installation.
You take the following action:
On the Run line, you type:
Winnt32.exe /s:L:I386 /u:unattend.txt /r:INSTALL.
Which requirement does the command meet?
a. The installation is performed over the network
b. The actions do not meet any of the requirements
c. The users cannot change any installation options
d. The users can use the Recovery Console after installation
e. The optional folder named INSTALL is installed and not removed with the temporary files after the installation
Your company has recently hired you to be the Windows 2000 network administrator. The network uses a DHCP server and Terminal Services.
You must install a new network card in one of the Windows 2000 Server computers. You must then configure properties and settings after the installation of the device and the device drivers.
What is the best way to accomplish this task?
a. Use the Installation CD
b. Manually configure the settings
c. Allow Windows 2000 to configure the settings
d. Copy the settings from another network adapter
You are the administrator for a Windows 2000 network. The network is configured for Active Directory and Group Policies.
You want to implement auditing on the network. You have enabled access to Active Directory objects. You now need to enable auditing for specific Active Directory objects.
What must you access to enable these objects?
a. Event Viewer snap-in
b. Security Configuration and Analysis snap-in
c. Active Directory Sites and Services snap-in
d. Active Directory Users and Computers snap-in
You must connect a satellite office to the main office network using the Internet. At the main office, you will connect to a Windows 2000 server using a Windows 2000 Professional computer from the satellite office. How should you make the connection using the most secure method over the Internet?
a. Implement a VPN connection with the IP in IP (IP-IP) protocol
b. Implement a VPN connection with the Point-to-Point Tunneling Protocol
c. Implement a VPN connection with the Layer 2 Tunneling Protocol
d. Implement a VPN connection with the PPTP protocol using IPSec Encapsulating Security payload Tunnel Mode
You are the administrator for your company's Windows 2000 network. The network consists of Windows 2000 Server computers and Windows 2000 Professional client computers. The network uses the Encrypting File System (EFS) to encrypt data files and folders.
You are setting up encryption on some files of a user's computer. You want to achieve the following goals:
Encrypt the data in the My Documents folder.
Configure the My Documents folder to be archived.
Configure the My Documents folder to be indexed.
Compress the data in the My Documents folder.
You perform the following actions:
You select the My Documents folder, right-click, and open the Properties dialog box.
You click the Advanced button to open the Advanced Attributes dialog box.
You check the 'Folder is ready for archiving' box.
You check the 'For fast searching, allow Indexing' box.
You check the 'Encrypt Contents To Secure Data' box.
You close the dialog boxes.
Which goal or goals are accomplished from these actions? (Choose all that apply.)
a. Encrypt the data in the My Documents folder
b. Compress the data in the My Documents folder
c. Configure the My Documents folder to be indexed
d. Configure the My Documents folder to be archived
As the network administrator, you must upgrade 3 Windows 3.1 workstations to the Windows 2000 Server operating system. The workstations meet the minimum hardware requirement for installing Windows 2000 Server, but they do not have a CD-ROM in them. You must perform an over-the-network install of the operating system. You must also partition the hard drive in the computer so it is 2 GB and not the existing 1 GB. How can you perform this function? (Choose three.)
a. Boot the computers with a Windows 95 boot disk
b. Boot the computers with an MS-DOS network boot disk
c. Install the new OS using the Winnt.exe command
d. Fdisk the drive, delete the partition, and create a new 2 GB primary partition
e. Migrate to the new operating system using the Winnt32.exe command from the Run line of Windows 3.1
f. Fdisk the drive, delete the partition, create a new 2 GB primary partition and format the new partition
You are administering a Windows 2000 network that uses Windows 2000 Server computers and Windows 2000 Professional client computers.
You need to make some configuration changes to the hardware profiles for one of the server computers.
What should you access to accomplish this task?
a. System in Control Panel
b. Power Options in Control Panel
c. Add/Remove Hardware in Control Panel
d. Network and Dial-Up Connections in Control Panel
You are configuring Group Policy for your Windows 2000 network. The network uses only Windows 2000 Server computers and Windows 2000 Professional client computers.
You want to create a group policy. You want the policy linked to a domain. You must first create a group policy object.
What do you access to accomplish this task?
a. Services snap-in
b. Security Configuration And Analysis snap-in
c. Active Directory Sites and Services snap-in
d. Active Directory Domains and Trusts snap-in
e. Active Directory Users and Computers snap-in
You must implement a 200-node network. You must divide the network into 4 subnets and each subnet must not exceed 60 nodes. How should you configure the IP addressing structure to allow for this configuration if the company's IP address is 194.194.194.0?
a.
b.
c.
d.
You attempt to install Windows 2000 server on a Pentium III 550 MHz computer with a bootable CD-ROM and a bootable CD-RW drive and you receive a media error. You have received this error on the bootable CD-ROM drive on three attempts. You then change the CMOS settings so the CD-RW drive is the first place the computer looks for initialization files. However, you also receive a media error when attempting to install Windows 2000 on the computer. Both drives are on the Hardware Compatibility List (HCL) for Windows 2000. How should you proceed?
a. Verify all hardware is properly detected and on the HCL
b. Verify the proper domain name is used during the installation
c. Contact Microsoft and request a Windows 2000 server replacement CD
d. Ensure the target partition has sufficient free space for the Windows 2000 server installation
e. Replace the CD-ROM drive and reset the CMOS to search it first for initialization files during the system boot process
As the network administrator of a Windows 2000 network, you must optimize disk space on a domain controller. The domain controller has a 6-GB SCSI hard drive in it that is a single NTFS partition. You must compress all archive information that is in the C:Archive folder. How can you compress the folder?
a. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the 'Folder is ready for Archiving' box is selected.
b. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the 'Encrypt contents to secure data' selection box is selected.
c. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the 'Compress contents to save disk space' selection box is selected.
d. Right-click on the folder, select Properties, select Advanced from the General Tab, and ensure the 'For faster searching allow Indexing Service to Index the folder' box is selected.
You must share the C:user data folder on a Windows 2000 server. The C: partition of the Windows 2000 drive is an NTFS partition. The name of the Windows 2000 server is Server1. You have created three Windows 2000 groups on the server named Employees, Board Members, and IT Staff. John is a member of the Users group and the IT Staff group. Mark is a member of the Board Members group. Max is a member of the Employees group and the Users group. Bob is a member of the IT Staff group and the Board Members group. You must share the folder and file so the following users have access to the share:
Mark must have read-only access to the folder when he accesses the folder remotely.
Max must be able to modify the contents of the folder when he accesses the folder remotely.
John must be able to take ownership of the folder when he is logged on to the server.
Bob must be able to add files to the folder when he accesses the folder remotely.
The permissions for each group are shown below:
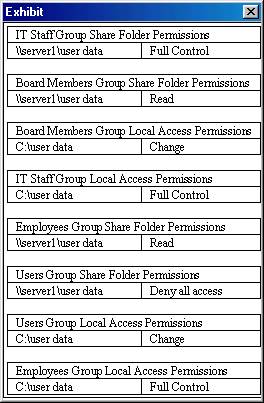
Which users have appropriate access to the folder? (Choose all that apply.)
a. Max
b. Bob
c. John
d. Mark
e. None of the users will have the appropriate access
You add a printer to a Windows 2000 Server domain controller. This printer is intended for use only by the top ten executives in the company. They are all members of the Executives group, but there are 75 other executives that are also members of this group. The executives are also members of the Domain Users Group, the Everyone Group, and the Board Members group. The Board Members group contains the 20 board members of the company. You want to configure the printer so only these 10 members can access the printer. How can you perform this function?
a. Allow Print permissions to the Executives group and deny access to the printer for all the other groups.
b. Allow Full Control permission to the Executives group and deny access to the printer for all the other groups.
c. Clear all access to all groups and add the 10 executives to the printer's ACL with Print permissions assigned to each one of them.
d. Deny access to all groups and add the 10 executives to the printer's access control list (ACL) with Full Control permissions assigned to each one of them.
You are the administrator of your Windows 2000 network. The domain controller on the network had a hard drive fail in it. The disk configuration is shown below:
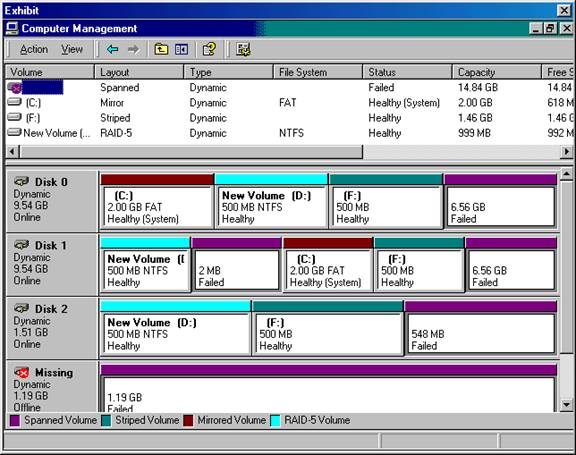
You must meet the following requirements:
You must replace the missing hard drive.
You must recreate all volumes that were affected by the missing hard drive.
You must restore the data to its original state.
You take the following actions:
You replace the hard drive with a 10-GB hard drive.
You make the new hard drive Dynamic.
You recreate the spanned volume allocating 1.19 GB of space for Disk 3 and all the other free space on the other 3 hard drives.
You restore the data from backup.
Which requirements do the actions meet? (Choose all that apply.)
a. The missing hard drive is replaced
b. The data is restored to its original state
c. The actions do not meet any of the requirements
d. All volumes affected by the missing hard drive are replaced
You must implement a 1000-node network. The network will consist of four Windows 2000 domain controllers, two Windows 2000 servers, 3 Hewlett Packard 5SI printers, and 995 Windows 2000 Professional workstations. Your company has been assigned an IP address of 136.18.32.0. You expect the network to double in size to approximately 8 subnets with 250 nodes per subnet in the next two years. How should you configure the IP addressing structure to allow for this configuration so that no single subnet can have more than 300 nodes, but can accommodate at least 250 nodes?
a.
b.
c.
d.
During the installation of Windows 2000 Server, you receive an insufficient disk space error. There is a small amount of data on this disk that must not be erased, and the server's hardware must not be modified. How can you resolve this error?
a. Format the partition
b. Install another hard drive
c. Verify all hardware is properly detected and on the Hardware Compatibility List
d. Create enough free space for the Windows 2000 Server installation on the target partition
As the network administrator, you must run a processor intensive report every afternoon before closing. You receive many complaints from network users about the network slowing down dramatically during the time this report runs. You must still run the report locally on the Windows 2000 server, but you must minimize the effect on the processor. How can you achieve this functionality?
a. Run the application that creates the report with the /BelowNormal switch from the Run line
b. Use the Processes tab of Task Manager and set the priority of the process running the report to Low
c. Use the Performance tab of Task Manager and set the priority of the process running the report to Low.
d. Use the Processes tab of Task Manager and set the priority of the process running the report to Realtime.
e. Use the Performance tab of Task Manager and set the priority of the process running the report to Realtime.
You are the administrator for a Windows
2000 network. The company consists of
the corporate office located in
From the
What may be the problem?
a.
The servers at the
b. The servers at the Daytona and
c.
The PPP conversations are not configured
to access the servers at the Daytona and
d. The PPP conversations do not support conversations with the operating
systems on the servers at the
You are configuring your Windows 2000 server and must configure certain information on a fault tolerant volume. You must store the entire Exchange database and all customer information so a single failed disk in the drive will not lose any information. The partitions in the drive are as follows:
C:- 2-GB FAT RAID Level 1 partition
D:- 6-GB NTFS RAID Level 5 partition
F:- 2-GB FAT32 striped set
G:- 13-GB FAT32 spanned volume
On which partition could you store the information if you needed to encrypt the files?
a. C:
b. D:
c. F:
d. G:
You are the administrator of your company's Windows 2000 domain controller. The domain controller contains three 5-GB hard drives. They are configured as follows:
The system partition is a 2-GB NTFS partition and is assigned the C: drive letter.
There is a RAID 5 volume that is composed of 2 GB from each drive and is assigned the D: drive letter.
There is a 1-GB FAT partition on DISK 0 that is assigned the E: drive letter.
There are two 3-GB FAT32 partitions that fill the remaining space on the other two drives. They are assigned letters F: and G: respectively.
You must optimize the disk space on the drives to meet the following requirements:
You must check all volumes for errors.
You must optimize the speed with which your applications initialize.
You must ensure all files are arranged on the volumes in a contiguous manner.
You must ensure the RAID volume is adequately prepared to minimize install time and initialization time of the program.
You take the following actions:
You use the Check Disk tool on all the drives.
You use Disk Defragmenter to analyze and defragment all volumes.
Which requirements are met by the actions? (Choose all that apply.)
a. All volumes are checked for errors
b. All files are arranged on each volume in a contiguous manner
c. The speed with which your applications initialize is optimized
d. The RAID volume is adequately prepared to minimize install time and initialization time of applications
You have two disks in your Windows 2000 server. You must protect the system partition by creating an exact duplicate of it so if one of the hard drives fails, the system information is still protected. How should you configure the computer's hard disks?
a. As a striped set
b. As a spanned volume
c. As a RAID level 1 configuration
d. As a RAID level 5 configuration
A Windows 2000 server print device fails and can no longer print successfully. You must print a specific document sent to the print device. The queue for the print device has 200 pending print jobs. How can you print the specific document?
a. Print the document to a file
b. Delete and recreate the print device
c. Redirect the single document to another print device
d. Redirect all documents to a different print device
Answer Key:
C
B
A,B,C,D
B,C,F
D
D
B
E
A,D
D
C
A,B,D
A,B,C,D,E
B
D
A,B,C,D
D
A,C,D
D
A,C,D
A,C
D
A,B,C,D
B
B
B
A
D
CPU Time, Base Priority
B
A,B,C,D
A,C
A
D
A,B,C,D
A,B,C,D
A,B,C,D
C
C
C
C
A
A,B,D
D
C,D
A
E
C
C
D
C
B,C,D
D
A
C
A,D
C,D
B,C
A
C
C
D
A,C
A
A,C
A
D
B,D
B,C,D
A,B,C
A,C,D
A,B,C,D
A
B
A,B
C
A
B
B
C
D
D
A,C,D
B,C,F
A
E
B
C
C
B,C,D
C
D
C
D
B
B
B
A,B,C,D
C
D
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1671
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2026 . All rights reserved