| CATEGORII DOCUMENTE |
| Bulgara | Ceha slovaca | Croata | Engleza | Estona | Finlandeza | Franceza |
| Germana | Italiana | Letona | Lituaniana | Maghiara | Olandeza | Poloneza |
| Sarba | Slovena | Spaniola | Suedeza | Turca | Ucraineana |
v Internet Architecture and Philosophy
Ø A TCP/IP internet provides three sets of services as shown in the following figure
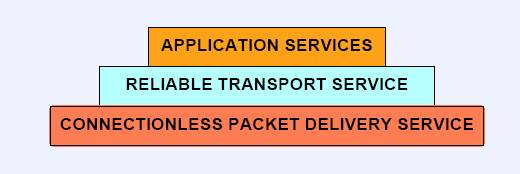
v Connectionless Delivery System
Ø The most fundamental internet service consists of a packet deliver system, which is unreliable, best-effort, and connectionless.
Ø Unreliable: packets may be lost, duplicated, delayed, or delivered out of order.
Ø Connectionless: each packet is treated independently from all others.
Ø Best-effort: the Internet software makes an earnest attempt to deliver packets.
v Purpose of the Internet Protocol
Ø The IP protocol defines the basic unit of data transfer (IP datagram)
Ø IP software performs the routing function
Ø IP includes a set of rules that embody the idea of unreliable packet delivery:
t How hosts and routers should process packets
t How and when error messages should be generated
t The conditions under which packets can be discarded.
v IP Datagram Encapsulation
IP Datagram Encapsulation for Ethernet
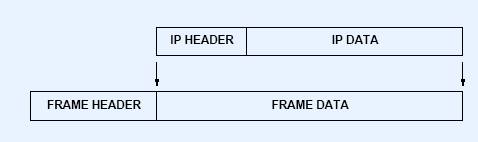
![]()
v IP Header Format
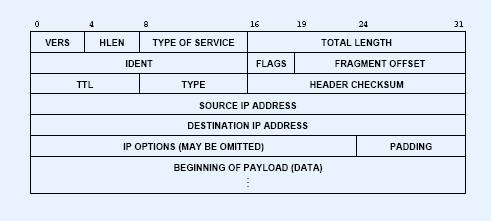
v VERS: current version is 4, I.e. IPv4
Ø proposal for IPv6, which will have a different header
v HLEN: header length in # 32-bit words
Ø Normally = 5, i.e. 20 octet IP headers
Ø Max 60 bytes
Ø Header can be variable length (IP option)
v TYPE OF SERVICE 3-bit precedence field (unused), 4 TOS bits, 1 unused bit set to 0
Ø TOS bit 1 (min delay), 2 (max throughput), 3 (max reliability), 4 (min cost): only one can be set
Ø typically all are zero, for best-effort service
Ø DiffServ proposes to use TOS for IP QOS
v TOTAL LENGTH: of datagram, in bytes
Ø Max size is 65535 bytes (64K C 1)
v IDENT, FLAGS, FRAGMENT OFFSET:
Ø Used for fragmentation and reassembly, will talk about this later
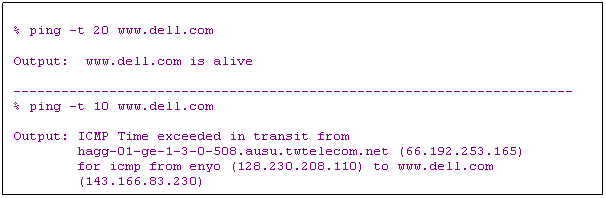
v TTL (Time To Live): upper limit on # routers that a datagram may pass through
Ø Initialized by sender, and decremented by each router. When zero, discard datagram. This can stop routing loops
Ø Example: ping Ct TTL IP allows us to specify the TTL field
Ø Question: normal users are not supposed to be able to modify the TTL field, how does ping do that? (the SetUID concept)
Ø Question: How to implement traceroute? i.e., how to find the routers to a destination (without using IP options)?
t Use TTL=1,2,3,
v TYPE: IP needs to know to what protocol it should hand the received IP datagram
Ø In essence, it specifies the format of the DATA area
Ø Demultiplexes incoming IP datagrams into either UDP, TCP, ICMPt
v HEADER CHECKSUM
Ø 16-bit 1ts complement checksum
Ø Calculated only over header
Ø Recomputed at each hop
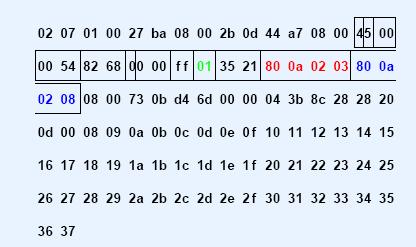
v An example of IP datagram
Ø Header length: 20 octet
Ø TYPE: 01 (ICMP)
Ø Source IP: 128.10.2.3
Ø Destination IP: 128.10.2.8
An example of IP datagram encapsulated in an Ethernet Frame
v IP OPTIONS
Ø IP OPTIONS field is not required in every datagram
Ø Options are included primarily for network testing or debugging.
Ø The length of IP OPTIONS field varies depending on which options are selected.
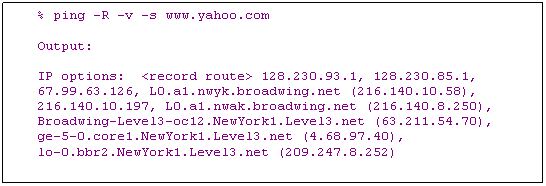
v Record Route Option
Ø The sender allocates enough space in the option to hold IP addresses of the routers (i.e., an empty list is included in the option field)
Ø Each router records its IP address to the record route list
Ø If the list is full, router will stop adding to the list
Ø Example: ping CR (on Solaris)
v Timestamp Option
Ø Works like the record route option
Ø Each router along the path fills in a 32-bit integer timestamp
v Source Routing
Ø It provides a way for the sender to dictate a path through the Internet.
Ø Strict Source Routing
t The list of addresses specifies the exact path the datagram must follow to reach its destination
t An error results if a router cannot follow a strict source route
Ø Loose Source Routing
t The list of addresses specifies that the datagram must follow the sequence of IP addresses, but allows multiple network hops between successive addresses on the list
Ø Question: how are these two types of source routing implemented?
![]()
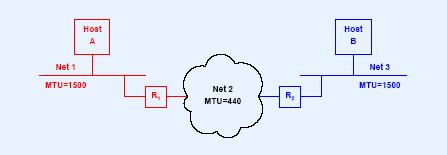
v Why do we need fragmentation?
Ø MTU: Maximum Transmission Unit
Ø An IP datagram can contain up to 65535 total octets (including header)
Ø Network hardware limits maximum size of frame (e.g., Ethernet limited to 1500 octets, i.e., MTU=1500; FDDI limited to approximately 4470 octets/frame)
Illustration of When Fragmentation is Needed
v IP fragmentation
Ø Routers divide an IP datagram into several smaller fragments based on MTU
Ø Fragment uses same header format as datagram
Ø Each fragment is routed independently
v How is an IP datagram fragmented?
Ø IDENT: unique number to identify an IP datagram; fragments with the same identifier belong to the same IP datagram
Ø FRAGMENT OFFSET:
t Specifies where data belongs in the original datagram
t Multiple of 8 octets
Ø FLAGS:
t bit 0: reserved
t bit 1: do not fragment
t bit 2: more fragments. This bit is turned off in the last fragment (Q: why do we need this bit? A: the TOTAL LENGTH field in each fragment refers to the size of the fragment and not to the size of the original datagram, so without this bit, the destination does not know the size of the IP datagram)
An Example of IP Fragmentation
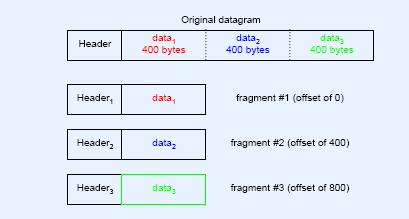
Ø Example: Header + 400 + 400 + 400
t Header 1: FLAGS=001 and OFFSET = 0
t Header 2: FLAGS=001 and OFFSET = 400/8 = 50
t Header 2: FLAGS=000 and OFFSET = 800/8 = 100
v How are IP fragments reassembled?
Ø All the IP fragments of a datagram will be assembled before the datagram is delivered to the layers above.
Ø Where should they be assembled? At routers or the destination?
t They are assembled at the destination.
Ø IP reassembly uses a timer. If timer expires and there are still missing fragments, all the fragments will be discarded.
v Question: if you are implementing the IP fragmentation, what (malicious) situations do you need to consider? Malicious situations are those that are intentionally created by adversaries, rather than occurring naturally.
Ø What do you do if you never get the last missing piece?
Ø What do you do if you get overlapping fragments?
Ø What do you do if the last byte of a fragment would go over the maximum size of an IP packet, i.e., if the size of all reassembled fragments is larger than the maximum size of an IP packet?
v Attack 1: Denial of Service Attack
Ø 1st fragment: offset = 0
Ø 2nd fragment: offset = 64800
Ø Result: The target machine will allocate 64 kilobytes of memory, which is typically held for 15 to 255 seconds. Windows 2000, XP, and almost all versions of Unix are vulnerable.
v Attack 2: TearDrop
Ø Send a packet with:
t offset = 0
t payload size N
t More Fragments bit on
Ø Second packet:
t More Fragments bit off
t offset + payload size < N
t i.e., the 2nd fragment fits entirely inside the first one.
Ø When OS tries to put these two fragments together, it crashes.
v Overlapping attacks against firewalls
Ø Many firewalls inspect packet separately. When the filtering rule is based on TCP header, but the TCP header is fragmented, the rule will fail
Ø TCP header is at the beginning of the data area of an IP packet.
Ø Firewalls often check TCP header: for example, SYN packet for connection request.
t Tiny Fragment Attack: Assumption: firewalls only check the packets with offset=0.
t Overlapping attacks: Assumption: firewalls only check the packets with offset=0.
![]()
v Spoofing:
Ø Any host can send packets pretending to be from any IP address
Ø Replies will be routed to the appropriate subnet.
v Egress (outgoing) Filtering
Ø Remove packets that couldn't be coming from your network; however it doesn't benefit you directly, so few people do it.
v Ingress (incoming) Filtering: remove packets from invalid (e.g. local) addresses.
v To conduct IP spoofing, one needs the superuser privilege.
![]()
v Router vs. Host
Ø A router has direct connections to two or more networks, has multiple network cards and multiple IP addresses.
Ø A host usually connects directly to one physical network.
v Direct and Indirect Delivery
Ø Direct delivery: ultimate destination can be reached over one network
Ø Indirect delivery: requires intermediary (router)
v Routing table
Ø Used by routers to decide how to send datagram
Ø Only stores address of next router along the path
Ø Scheme is known as next-hop routing
Ø (We will discuss later on how to construct routing tables)
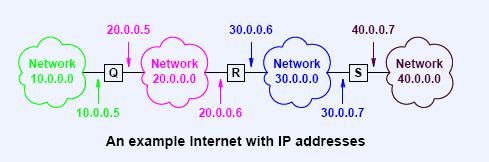
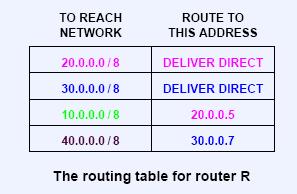
v Next-Hop Routing
Ø The destination IP address will not change, the next hop's MAC address is used.
Ø Routing table entries (the router R's IP is 20.0.0.6 and 30.0.0.6):
v Host-Specific Routes:
Ø Allows per-host routes to be specified as a special case
v Default Routes
Ø Only selected if no other match in table
Ø Especially for hosts.
v IP Routing Algorithm

v Handling Incoming Datagrams
Ø Host: accept or drop. Don't forward. Hosts are forbidden from attempting to forward datagrams that are accidentally routed to the wrong machine. Why?
Ø Router: accept or forward.
t Forwarding: decrease TTL field, recompute the header checksum.
t Dropping: TTL=0; send an error message to the source.
v Manipulate routing tables: the route command (Linux, Windows, Solaris)
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1166
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved