| CATEGORII DOCUMENTE |
| Bulgara | Ceha slovaca | Croata | Engleza | Estona | Finlandeza | Franceza |
| Germana | Italiana | Letona | Lituaniana | Maghiara | Olandeza | Poloneza |
| Sarba | Slovena | Spaniola | Suedeza | Turca | Ucraineana |
|
2: The OSI Model |
|
Select Objective:
|
|
2: The
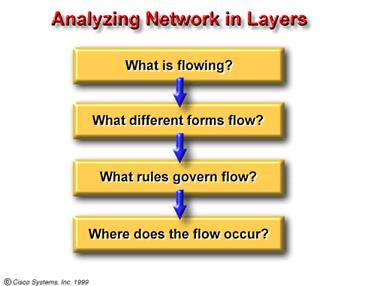
OSI Model Now examine the 'Comparing Networks' chart. Another example of how you might use the concept of layers to analyze an everyday subject is to examine human conversation. When you create an idea that you wish to communicate to another person, the first thing you do is choose (often subconsciously) how you want to express that idea, then you decide how to properly communicate it, and finally, you actually deliver the idea. Imagine a young person seated at one end of a very long dinner table. On the other end of the table, quite a distance away, sits the young person's grandmother. The youngster speaks English. The grandmother prefers to speak Spanish. The table has been set with a wonderful meal that the grandmother has prepared. Suddenly the young person shouts at the top of his lungs, 'Hey, you! Give me the rice!' and reaches across the table to grab it. In many cultures, this action is considered quite rude. What should the young person have done to communicate his/her wishes in an acceptable manner? To help you find the solution to this question, analyze the communication process in layers. First you have the idea the young person wants rice; then you have the representation spoken English; next is the method of conveyance/transport 'Hey, you'; and finally, the medium shouting (sound) and grabbing (physical action) across the table for the rice. From this group of four layers, you can see that three of them prevent the young person from communicating his/her idea in an appropriate/acceptable manner. The first layer the idea is acceptable. The second layer (representation), of spoken English instead of Spanish, and the third layer (transport), of a loud demand instead of a polite request, most definitely do not follow acceptable social protocol. The fourth layer (medium), shouting and grabbing from the table rather than politely requesting assistance from another person seated nearby, is unacceptable behavior in most any social situation. By analyzing this interaction in terms of layers you can understand more clearly some of the problems of communication (human or computer), and how you might solve them.
https://www.rad.com/networks/1994/osi/osi.htm |
|
2.1.2.1. Describe source,
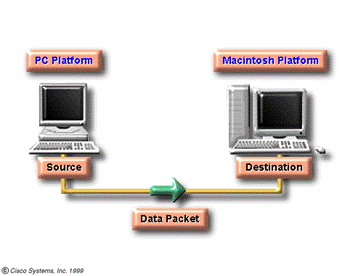
destination, and data packet. Data are logically grouped units of information that move between computer systems. They include the original user information along with other elements necessary to make communication of the information possible and reliable. At its most basic level, computer data consist of binary digits, or bits (0s and 1s). Computers that send one or two bits of information, however, are not very useful, so other groupings - bytes, kilobytes, megabytes, and gigabytes - are necessary.
https://www.rad.com/networks/1994/osi/osi.htm |
|
2.1.3.1. Define medium.
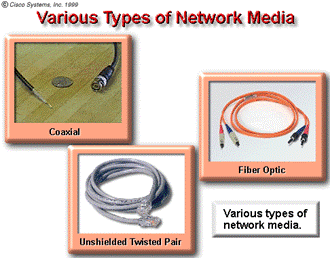
There are two more types of media that are less obvious, but should nonetheless be taken into account in network communications. First, is the atmosphere (mostly oxygen, nitrogen, and water) that carries radio waves, microwaves, and light. The second medium is not a medium in the physical sense, but are patterns of electromagnetic waves that travel in the vacuum of outer space, where there is virtually no matter, no molecules, and no atoms along which they can travel. Communications without some type of wire or cable are called wireless or free-space communications.
https://www.rad.com/networks/1994/osi/osi.htm |
|
2.1.4.1. Define protocol.
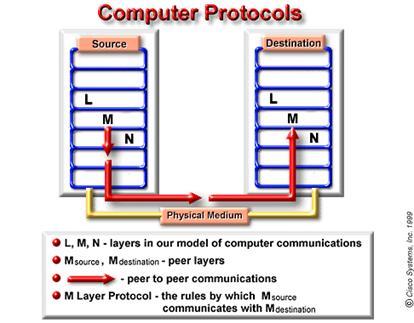
One technical definition of data communications protocol is: a set of rules, or an agreement, that determines the format and transmission of data. Layer n on one computer communicates with layer n on another computer. The rules and conventions used in this communication are collectively known as the layer n protocol.'
https://www.rad.com/networks/1994/osi/osi.htm |
|
2.1.5.1. Describe the evolution
of ISO networking standards. The International Organization for Standardization (ISO) researched networks schemes like DECNET, SNA, and TCP/IP in order to find a set of rules. As a result of this research, the ISO created a network model that would help vendors create networks that would be compatible with, and operate with, other networks. The OSI reference model (Note: Do not confuse with ISO.), released in 1984, was the descriptive scheme they created. It provided vendors with a set of standards that ensured greater compatibility and interoperability between the various types of network technologies that were produced by the many businesses around the world. To check on the current status of the continually evolving networking standards), view this website address:
https://www.acm.org/sigcomm/sos.html
https://www.rad.com/networks/1994/networks/preface.htm |
|
2.2.1.1. State the purpose of the
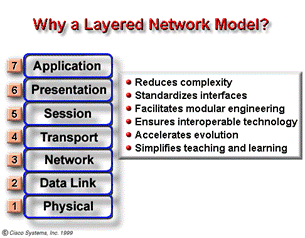
OSI reference model. The OSI reference model allows users to view the network functions that occur at each layer. It is a method of illustrating how information travels throughout a network. It explains, visually, how information, or data, travels from application programs (e.g. spreadsheets, documents, etc.), through a network medium (e.g. wires, etc.), to another application program that is located in another computer on a network, even if the sender and receiver have different types of networks. In the OSI reference model, there are seven numbered layers, each of which illustrates a particular network function. This separation of networking functions is called layering. Dividing the network into these seven layers provides the following advantages:
|
|
2.2.2.1. Identify each of the
seven layers of an OSI model. Layer 1: The Physical
Layer An easy way to help you memorize the names of the layers might be to use a mnemonic device such as All People Seem To Need Data Processing. During the course of this semester you will start with Layer 1 and work your way through the OSI model, layer by layer. For more information about the OSI model, visit the following sites:
https://ganges.cs.tcd.ie/4ba2/
https://cmit.unomaha.edu/isclass/bdc/c3/sld007.htm
https://www.shopthenet.net/publiclibrary/cie/topics/15.htm
https://www.rad.com/networks/1997/nettut/protocols.html#OSI7 |
|
2.2.3.1. Describe each of the
seven layers of an OSI model. The seven layers and their functions can be described, in more detail, as follows:
Layer 7: The application layer The application layer is the OSI layer that is closest to the user; it provides network services to the users applications. It differs from the other layers in that it does not provide services to any other OSI layer, but rather only to application processes outside the scope of the OSI model. Examples of such application processes are spreadsheet programs, word processing programs, and banking terminal programs. The application layer identifies and establishes the availability of intended communication partners, synchronizes cooperating applications, and establishes agreement on procedures for error recovery and control of data integrity. It also determines whether sufficient resources for the intended communication exist. If you want to remember Layer 7 in as few words as possible, think of browsers.
Layer 6: The presentation layer The presentation layer ensures that the information that the application layer of one system sends out is readable by the application layer of another system. If necessary, the presentation layer translates between multiple data representation formats by using a common data representation format. If you want to think of Layer 6 in as few words as possible, think of encoding, representation of data, ASCII.
Layer 5: The session layer As its name implies, the session layer establishes, manages, and terminates sessions between applications. Sessions consist of dialogues between two or more presentation entities. The session layer provides its services to the presentation layer. Also, the session layer synchronizes dialogue between presentation layer entities and manages their data exchange. In addition to basic regulation of conversations (sessions), the session layer offers provisions for data expedition, class of service, and exception reporting of session layer, presentation layer, and application layer problems. If you want to remember Layer 5 in as few words as possible, think of dialogues and conversations.
Layer 4: The transport layer The transport layer segments and reassembles data into a data stream. The boundary between the session layer and the transport layer can be thought of as the boundary between media-layer protocols and host-layer protocols. Whereas the application, presentation, and session layers are concerned with application issues, the lower three layers are concerned with data transport issues. The transport layer attempts to provide a data transport service that shields the upper layers from transport implementation details. Specifically, issues such as how reliable transport over an internetwork is accomplished are the concern of the transport layer. In providing reliable service, the transport layer provides mechanisms for the establishment, maintenance, and orderly termination of virtual circuits, transport fault detection and recovery, and information flow control, to prevent one system from overrunning another with data. If you want to remember Layer 4 in as few words as possible, think of quality of service, and reliability.
Layer 3: The network layer The network layer is a complex layer that provides connectivity and path selection between two end systems that may be located on geographically diverse networks. You'll learn more about Layer 3 in Chapter 3, 'Networking Devices.' If you want to remember Layer 3 in as few words as possible, think of path selection, switching, addressing, and routing.
Layer 2: The data link layer The data link layer provides reliable transit of data across a physical link. In so doing, the data link layer is concerned with physical (as opposed to network, or logical) addressing, network topology, line discipline (how end systems use the network link), error notification, ordered delivery of frames, and flow control. If you want to remember Layer 2 in as few words as possible, think of naming, framing, and of media access control.
Layer 1: The physical layer The physical layer defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating the physical link between end systems. Such characteristics as voltage levels, timing of voltage changes, physical data rates, maximum transmission distances, physical connectors, and other, similar, attributes are defined by physical layer specifications. If you want to remember Layer 1 in as few words as possible, think of signals and media.
|
|
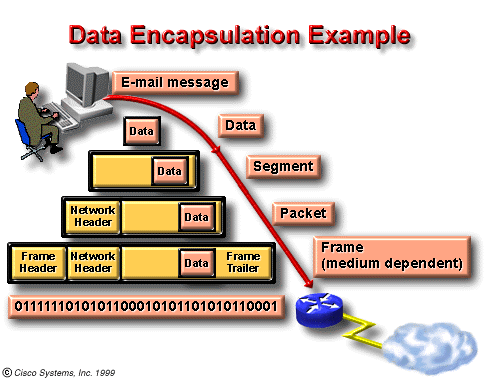
2.2.4.1. Define encapsulation. As networks perform their services for users, the packaging and flow of the information that is exchanged goes through changes. The following example of encapsulation illustrates the five conversion steps that networks must perform.
|
|
2.2.5.1. Identify data names at
each layer (segment/packet/frame/bits) of the OSI model.
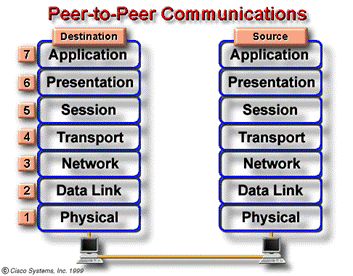
Data packets on a network originate at a source and are then sent to a destination. Each layer depends on the service function of the OSI layer below it. To provide this service, the lower layer uses encapsulation to put the PDU from the upper layer into its data field; then it adds whatever headers and trailers the layer needs to perform its function. Next, as the data moves down through the layers of the OSI model, headers and trailers are added. After Layers 7, 6, and 5 have added their information, Layer 4 adds more information. This grouping of data, the Layer 4 PDU, is called a segment. The network layer, for example, provides a service to the transport layer, and the transport layer presents data to the internetwork subsystem. The network layer has the task of moving the data through the internetwork. It accomplishes this task by encapsulating the data within a header. This header contains information required to complete the transfer, such as source and destination logical addresses. The network layer provides a service to the transport layer by encapsulating the data within a header and creating a packet (the Layer 3 PDU). The data link layer provides a service to the network layer. It encapsulates the network layer information in a frame (the Layer 2 PDU); the frame header contains information (e.g. physical addresses) required to complete the data link functions. The data link layer provides a service to the network layer by encapsulating the network layer information in a frame. The physical layer also provides a service to the data link layer. The physical layer encodes the data link frame into a pattern of 1s and 0s (bits) for transmission on the medium (usually a wire) at Layer 1. |
|
2.3.1.1. Describe the importance
of the TCP/IP model. https://www.ietf.org
https://www.ietf.cnri.reston.va.us/home.html
https://oac3.hsc.uth.tmc.edu/staff/snewton/tcp-tutorial/ |

|
2.3.2.1. Name, and describe, the
layers of the TCP/IP model. As you read about layers, keep in mind the original intent of the Internet ; it will it help explain why certain things are as they are. The TCP/IP model has four layers: the application layer, the transport layer, the Internet layer, and the network layer. Application Layer Transport Layer Internet Layer Network Layer For more TCP/IP information, visit the following website
https://tdi.uregina.ca/~ursc/internet/protocol.html
https://oac3.hsc.uth.tmc.edu/staff/snewton/tcp-tutorial/ |

|
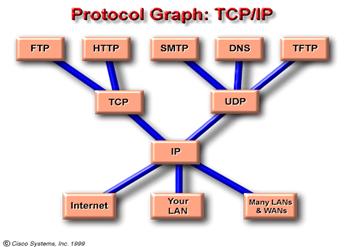
2.3.3.1. Explain the protocol
graph for TCP/IP.
The TCP/IP model emphasizes maximum flexibility, at the application layer, for developers of software. The transport layer involves two protocols - transmission control protocol (TCP) and user datagram protocol (UDP). You will examine these, in detail, later in the CCNA curriculum. The lowest layer, the network layer, refers to the particular LAN or WAN technology that is being used. In the TCP/IP model, regardless of which application requests network services, and regardless of which transport protocol is used, there is only one network protocol - internet protocol, or IP. This is a deliberate design decision. IP serves as a universal protocol that allows any computer, any where, to communicate at any time.
https://oac3.hsc.uth.tmc.edu/staff/snewton/tcp-tutorial/ |
|
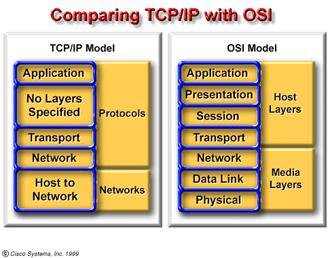
2.3.4.1. Compare the OSI model
with the TCP/IP model, layer by layer. Similarities
Differences
TCP/IP protocols are the standards around which the Internet developed, so the TCP/IP model gains credibility just because of its protocols. In contrast, no networks are built around specific OSI-related protocols, even though everyone uses the OSI model to guide their thinking.
https://oac3.hsc.uth.tmc.edu/staff/snewton/tcp-tutorial/ |
|
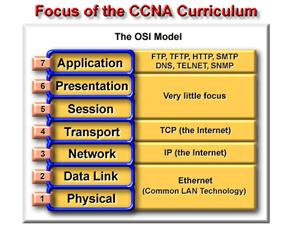
2.3.5.1. Explain why and how the
curriculum will use the OSI model as its foundation, but will also utilize
TCP/IP model.
Many networking professionals have different opinions on which model to use. You should become familiar with both. You will use the OSI model as the microscope through which to analyze networks, but you will also use the TCP/IP protocols throughout the CNAP curriculum. Remember that there is a difference between a model (i.e. layers, interfaces, and protocol specifications) and an actual protocol that is used in networking. You will use the OSI model but the TCP/IP protocols. You will focus on TCP as an OSI Layer 4 protocol, IP as
an OSI Layer 3 protocol, and Ethernet as a Layer 2 and Layer 1 technology.
The diagram shows that later in the course you will examine one particular
data link and physical layer technology out of the many choices available.
That will be Ethernet. If you want a preview of Ethernet, visit https://wwwhost.ots.utexas.edu/ethernet/ethernet-home.html
https://oac3.hsc.uth.tmc.edu/staff/snewton/tcp-tutorial/ |
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 3559
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2026 . All rights reserved