| CATEGORII DOCUMENTE |
| Bulgara | Ceha slovaca | Croata | Engleza | Estona | Finlandeza | Franceza |
| Germana | Italiana | Letona | Lituaniana | Maghiara | Olandeza | Poloneza |
| Sarba | Slovena | Spaniola | Suedeza | Turca | Ucraineana |
What is a Network?
At its most elementary level, a network consists of two computers connected to each other by a cable so that they can share data. All networking, no matter how sophisticated, stems from that simple system. While the idea of two computers connected by a cable may not seem extraordinary in retrospect, it was a major achievement in communications.
Networking arose from the need to share data in a timely fashion. Personal computers are wonderful business tools producing data, spreadsheets, graphics, and other types of information, but do not allow you to quickly share data you have produced. Without a network, the documents have to be printed out so that others can edit them or use them. At best, you give files on floppy disks to other to copy to their computers. If others make changes to the document there is no way to merge the changes. This was, and still is, called working in a stand-alone environment.
If you could connect your computer to other computers, you could the data on the other computers and the printers. A group of computers and other devices connected together is called a network, and the concept of connected computers sharing resources is called networking.
Computers that are part of a network can share the following:
Data
Messages
Graphics
Printers
Fax machines
Modems
Other hardware resources
This list is constantly growing as new ways are found to share and communicate by means of computers.
Local Area Networks
Networks started out small, with perhaps ten computers connected together with a printer. The technology limited the size of the network, including the number of computers connected as well as the physical distance that could be covered by the network. For example, in the early 1980's the most popular cabling method would allow about 30 users on a maximum cable length of just over 600 feet. Such a network might be on a single floor of a building, or within one small company. For very small companies today, this configuration is still adequate. This type of network, within a limited area, is known as Local Area Network (LAN).
Why use a Network?
Organizations implement networks primarily to share resources and enable online communication. Resources include data, applications, and peripherals. A peripheral is a device such as an external disk drive, printer, mouse, modem or Joystick. Online communication includes sending messages back and forth, or e-mail.
Problem: Before the advent of networks, people needed their own individual printers, plotters and other peripherals. Before networks existed, the only way to share a printer was for people to take turns sitting at the computer connected to the printer.
Solution: Networks now make it possible for several people to share both data and peripherals simultaneously. If many people need to use a printer, they can all use the printer available on the network.
Problem: Before network exited, people who wanted to share information were limited to:
Telling each other the information (voice communication)
Writing memos
Putting the information on a floppy disk, physically taking the disk to another computer, and they copying the data onto that computer.
Solution: Networks can reduce the need for paper communication and make nearly any type of data available to every user who needs it.
Network Communications
Network activity involves sending data from one computer to another. This complex process can be broken into discrete tasks;
Recognize the data
Divide the data into manageable chunks
Add information to each chunk of data
Determine the location of the data
Identify the receiver
Add timing and error checking information
Put the data on the network and send it on its way
The network operating system follows a strict set of procedures in performing each task. These procedures are called protocols, or rules of behavior. The protocols guide each activity to successful completion.
There arose a need for standard protocols to allow hardware and software from various vendors to communicate. The two network models that provide a framework for network communication is: the ISO/OSI reference model and TCP/IP suite.
A network model represents a common structure or protocol to accomplish between systems. A clear understanding of these models is important first step in understanding the technical aspects of how a network functions.
The ISO/OSI Model
In 1978, the International Standards Organization (ISO) released a set of specifications that described network architecture for connection dissimilar devices. The original document applied to systems that were open to each other because they could all use the same protocols and standards to exchange information.
In 1984, the ISO released a revision of this model and called it the Open Systems Interconnection (OSI) reference model. The 1984 revision has become an international standard and serves as a guide for networking.
This model is the best-known and most widely used guide to describe networking environments. Vendors' design network products based on the specifications of the OSI model. It provides a description of how network hardware work together in a layered fashion to make communications possible. It also helps with troubleshooting by providing a frame of reference that describes how components are supposed to function.
A Layered Architecture
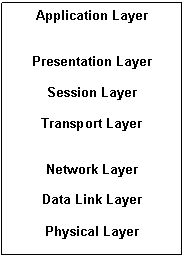
The OSI model is an architecture that divides network communication into seven layers. Each layer covers different network activities, equipments, or protocols.
![]()
![]()
![]()
![]()
![]()
![]()
The above figure represents the layered architecture of the OSI model. Layering specifies different functions and services at different levels. Each OSI layer has well-defined networking functions, and the functions of each layer communicate and work with the functions of the layers immediately above and below it. For example, the Session layer must communicate and work with the presentation and Transport layers.
The lowest layers - 1 and 2 - define the network's physical media and related tasks, such as putting data bits onto the network adapter cards and cable. The highest layers define how applications access communication services. The higher the layer, the more complex is the task.
Each layer provides some service or action that prepares the data for delivery over the network to another computer. The layers are separated from each other by boundaries called interfaces. All requests are passed from one layer, through the interface, to the next layer. Each layer builds upon the standards and activities of the layer below it.
Relationship of OSI Model Layers
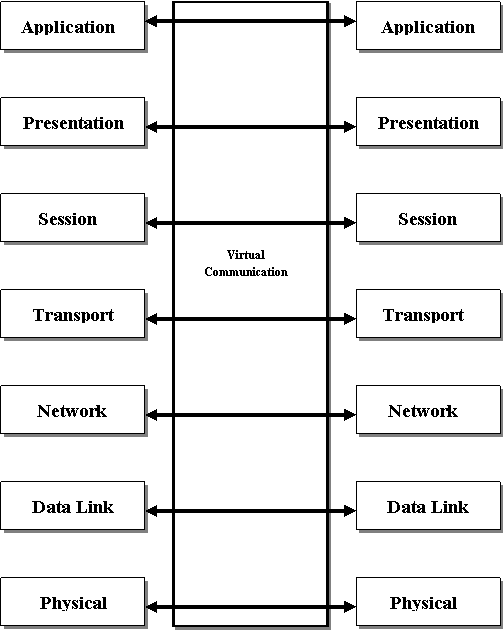
The purpose of each layer is to provide services to the next higher layer and shield the upper layer from the details of how the services are actually implemented. The layers are setup in such a way that each layer acts as if it is communicating with its associated layer on the other computer. This is a logical or virtual communication between peer layers as shown in the figure below. In reality, actual communication takes place between adjacent layers on one computer. At each layer there is software that implements certain functions according to a set of protocols.
Before data is passed from one layer to another it is broken down into packets. A packet is a unit of information transmitted as a whole from one device to another on a network. The network passes a packet from one software layer to another in the order of the layers. At each layer the software adds some additional formatting or addressing to the packet, which it needs to be successfully transmitted across the network.
AT the receiving end, the packet passes through the layers in the reverse order. Software utility at each layer reads the information on the packet, strips it away, and passes the packet up to the next layer. When the packet finally gets passes up to the Application layer, the addressing information has been stripped away and the packet is in its original form, which is readable by the receiver.
Except for the lowest layer in the networking model, no layer can pass information directly to its counterpart an another computer. Information on the sending computer must be passed through all of the lower layers. The information then moves across the networking cable to the receiving computer and up that computer's networking layers util arriving at the same level that sent the information. For example, if the Network layer sent information from computer A, it moves down through the Data Link and the Physical layers on the receiving side to its destination at the Network layer on computer B.

In a client/server environment, an example of the kind of information sent from
the Network layer on computer A to the Network layer on computer B would be a
network address and perhaps some error checking information added to the
packet.
Interaction between adjacent layers occurs through an interface. The interface defines which services the lower networking layer offers to the upper one and how those services will be accessed. In addition, each layer on one computer acts as though it is communication directly with the same layer on another computer.
The purpose of each of the seven layers of the OSI model and the services they provide to adjacent layers are discussed below:
Application Layer
Layer 7, the topmost layer of the OSI model, is the Application layer. It servers as the window for application processes to access network services. This layer represents the services that directly support user applications, such as software for file transfers, for database access, and for e-mail. The lower levels support these tasks performed at the application level. The application layer handles general network access, flow control, and error recovery.
Examples of the Application Layer are:
SMTP (Simple Mail Transfer Protocol)
FTP (File Transfer Protocol)
TELNET (Remote Terminal Protocol)
NFS
SNMP
Presentation Layer
Layer 6, the Presentation layer, determines the format used to exchange data among networked computers. It can be called the network's translator. At the sending computer, this layer translates data from a format sent down from the Application layer into a commonly recognized, intermediary format. At the receiving computer, this layer translates the intermediary format into a format useful to that computer's Application layer. The presentation layer is responsible for protocol conversion, translating the data, encrypting the data, changing or converting the character set, and expanding graphics commands. The presentation layer also manages data compression to reduce the number of bits that need to be transmitted.
A utility known as the redirector operates at this layer. The purpose of the redirector is to redirect input/output (I/O) operations to resources on a server.
This layer is implemented using XDR (External Data Representation), which balances the interpretation differences. It transforms C basic structures into XDR data structure and vice versa. Any system can communicate via the network by using XDR.
Session Layer
Layer 5, the Session layer, allows to applications on different computers to establish, use, and end a connection called a session. This layer performs name recognition and the functions, such as security, needed to allow two applications to communicate over the network.
The Session layer provides synchronization between user tasks by placing checkpoints in the data stream. This way if the network fails, only after the last data check point has to be retransmitted. This layer also implements dialog control between communicating processes regulating which side transmits, when for how long, and so on.
Transport Layer
Layer 4, the Transport layer, provides an additional connection level beneath the Session layer. The Transport layer ensures that packets are delivered error free, in sequence, and with no losses or duplications. This layer repackages message, dividing long messages into several packets and collecting small packets together in one package. This allows the packets to be transmitted efficiently over the network. At the receiving end, the Transport layer unpacks the messages, reassembles over the network. At the receiving end, the Transport layer unpacks the messages, reassembles the original messages, and typically sends an acknowledgement of receipt.
The Transport layer provides flow control, error handling, and is involved in solving problems concerned with the transmission and reception of packets.
An example of a protocol for the Transport layer is:
TP-0 to TP-4 (OSI)
Network Layer
Layer 3, the Network layer, is responsible for addressing messages and translating logical addresses and names into physical addresses. This layer also determines the route from the source to the destination computer. It determines which path the data should take based on network conditions, priority of service, and other factors. It also manages traffic problems on the network, such as packet switching, router and controlling the congesting of data.
If the network adapter on the router cannot transmit a data chunk as large as the source computer sends, the Network layer on the router compensates by breaking the data into smaller units. On the destination end, the Network layer reassembles the data.
An example of a protocol for the Network layer is:
Connectionless-mode/Connection-mode (CLIN/CONS)
Data Link Layer
Layer 2, the Data Link layer, sends data frames from the Network layer to the Physical layer. On the receiving end, it packages raw bits from the Physical layer into data frames. A data frame is on organized logical structure in which data can be placed.
In a simple data frame, the sender ID represents the address of the computer that is sending the information; the destination control information is used for frame type, routing, and segmentation information. The data is the information itself. The cyclic redundancy check (CRC) represents error correction and verification information to ensure that the data frame is received properly.
The Data Link layer is responsible for providing the error-free transfer of these data frames from one computer to another through the physical layer. This allows the Network layer to assume virtually error-free transmission over the network connection.
Generally, when the Data Link layer sends a frame, it waits for an acknowledgement from the recipient. The recipient Data Link layer detects any problems with the frame that may have occurred during transmission. Frames that were not acknowledged, or frames that were damaged during transmission, are resent.
Examples of protocols for the Data Link layer are:
LAPB (Link Access Procedure; X.25)
Ethernet V.2, Ethernet IEEE 802.3, Token Ring IEEE 802.5, and Taken Bus IEEE 802.4
Physical layer
Layer 1, the bottommost layer of the OSI model, is the Physical layer. This layer transmits the unstructured raw bit stream over a physical (such as the network cable). The Physical layer relates the electrical, optical, mechanical, and functional interfaces to the cable. The Physical layer also carries the signals that transmit data generated by all of the higher layers.
This layer defines how the cable is attached to the network adapter card. For example, it defines how many pins the connector has and each pin's function. It also defines which transmission technique will be used to send data over the network cable.
The Physical layer is responsible for transmitting bits (zeros and ones) from one computer to another. The bits themselves have no defined meaning at this level. This layer defines data encoding and bit synchronization, ensuring that when a transmitting host sends a 1 bit, it is received as a 1 bit, not a 0 bit. This layer also defines how long each bit is translated into the appropriate electrical or optical impulse for the network cable.
TCP/IP
TCP/IP stands for Transmission Control Protocol/Internet Protocol and it's an industry-standard suite of protocols designed for networks. It is a set of protocols developed to allow co-operating computers to share resources across a network. TCP/IP supports a wide range of platforms and networks.
The figure below contains the standard 'stack' diagram of TCP/IP. Rather than make protocols monolithic (which would mean ftp, telnet, and gopher would each have a full network protocol implementation, including separate copies of kernel code for the devices each protocol uses), the designers of TCP/IP broke the job of a full network protocol suite into a number of tasks. Each layer corresponds to a different facet of communication.
|
Application |
Telnet,FTP,RPC etc |
|
Transport |
TCP, UDP |
|
Network |
IP, ICMP, IGMP |
|
Link |
Network interface and devices |
The first, the link layer, is responsible for communication with the actual network hardware (e.g., the Ethernet card). Data it receives off the network wire it hands to the network layer; data it receives from the Network layer it puts on the network wire. This is where device drivers for different interface reside.
The third, the transport layer, provides data flows for the application layer. It is at the transport layer where guarantees of reliability may be mode.
The fourth, the application layer, is where users typically interact with the network. This is where telnet, ftp, email, IRC, etc. reside.
Packets are the basic unit of transmission on the Internet. They contain both data and header information. Simply put, headers generally consist of some combination of checksums, protocol identifiers, destination and source addresses, and state information. Each layer may add its own header information, so it can interpret the data the lower layer is handing it.
The Link Layer
The link layer is the simplest layer to understand. Composted of the network hardware and the device drivers, the Link layer is the lowest level of the protocol stack. When receiving data from the network, it takes packets from the network wire, strips away any link layer header information, and hands it off to the network layer. When transmitting data onto the network, it takes packets from the network layer, sticks a link layer header on them, and sends them out over the wire.
The benefit of separating out the hardware layer is that protocol implementers only have to write the Network layer once. Then they provide a common interface to the network layer by writing different device drivers for each kind of network interface.
The Network Layer
This is where the Internet Protocol (IP) and the Internet Control Message Protocol (ICMP), among others, reside. ICMP is used both to provide network reliability information and by utilities like ping and traceroute. IP is used for almost all other Internet communication. When sending packets, it is figures out how to get them to their destination; when receiving packets, it figures out where they belong. Because it does not worry about whether packets get to where they are going or whether they arrive in the order sent, its job is greatly simplified. If a packet arrives with any problems (e.g., corruption), IP silently discards it. Upper layers are responsible for insuring reliable reception of packets. We refer to IP's behavior as ''stateless '' or '' connectionless'' because the existence of previous or future packets is irrelevant when processing the current packet. We could unplug the network wire, wait a minute, plug it backs in, and IP would never know the difference.
IP is able to get packets to their destinations because every network interface on the Internet has a unique, numeric address. Oddly enough, these numbers are called IP addresses. Notice, every interface has its own address. If machine has multiple interfaces (as is the case with a router), each on has its own IP address. The InterNIC is responsible for assigning sets of addresses to organisations, thereby insuring uniqueness.
Because it's a pain to refer to machines with strings of numbers, the designers of TCP/IP allowed network administrators to associate names with IP addresses. Although this has nothing to do with the IP layer per se, we feel this is useful material. Originally, every host on the Internet maintained its own complete copy of this database (in /etc/hosts). However, as the Internet reached its current size, this soon became unwieldy -- both in terms of raw size and the administrative nightmare of updating it. And so was born the domain name system (DNS). It is a distributed database of IP addresses and their natural language names, called host names. In fact one IP address can have multiple names associated with it. When a network administrator adds a new machine to the network, the administrator is responsible for updating the organization's nameserver table. The changes quickly propagate. All communication with a machine is done via IP numeric addresses, so the hostname for a machine is only used at the beginning of a connection.
The steps IP takes to send a packet are simple: based on its IP address, figure out how to get it there and send it on its way.
The Transport Layer
There are two protocols at the transport layer; the transmission control protocol (TCP) and the user datagram protocol (UDP). TCP provides end-to-end reliable communication and UDP doesn't. UDP is as unreliable as IP, but allows people to write user level software that creates its own packet formats, which is particularly helpful if you wand to write new protocols, don't have the kernel sources, and don't want the overhead of TCP.
TCP creates a ''virtual circuit'' between two processes. It insures that packets are received in the order they are sent and that lost packets are retransmitted. We won't go into the details of how it works, but interactive programs like ftp and telnet use it.
So far we have discussed addressing on the host level -- how to identify a particular machine. But once at a machine, we need a way to identify a particular service (e.g., mail). This is the function of ports - identification numbers included with every UDP or TCP/IP ports are not hardware-based. They are a just a way of labeling packets. A process on a machine ''listens'' on the particular port. When the transport layer receives a packet, it checks the port number with the TCP/IP stack. Only one process per protocol can listen on a given port. So while a process using UDP and one using TCP can both listen on port 111, two processes that both used TCP could not. There are a number of parts, which are reserved for standard services. For example, SMTP, the mail protocol, is always on part 25, and telnetd is always on port 23. To see a list of the reserved ports look at /etc/services.
We've examined how ports work on the server end -- specific ports are reserved for set tasks. On the initiator end, port assignment is dynamic. When a telnet client on swell starts up, it gets a new port number (e.g., 1066). This is the source port which swell's TCP layer puts on every packet. This allows the telnet daemon (telnetd) on cool to responds to the correct telnet process on swell. The combination of source/destination IP addresses and ports provides a unique conversation identifier. Each conversation is called a flow.
UDP is essentially IP with port numbers (flows). It gives the user access to IP-style datagrams. The network file system (NFS) and talk are two examples of UDP-based protocols.
This has been an extremely cursory exploration of TCP and UDP. At this point, you should have a decent understanding of how the network (IP) and transport (TCP/UDP) layers interact.
The Application Layer
This is where the user interacts with the network. All network programs like telnet, ftp, mail, news, and WWW clients are at the application layer. They then user either TCP or UDP to communicate with other machines.
Peer-to-Peer Communication
Peer-to-peer communication is the ability of a specific layer to communicate with the corresponding layer on another host. When systems exchange data using the TCP/IP model, they are performing peer-to-peer communication.
At each layer, the data or message is encapsulated and header information about the corresponding protocol layer added. This information is key in the peer-to-peer communication and is used to de-encapsulate and direct the message to the appropriate application.
Care protocols, utilities, and services associated with the TCP/IP suite include:
IP (Internet Protocol) -IP provides connectionless delivery between computer systems. Since this is a connectionless protocol, there is no guarantee of proper sequencing or even arrival at the destination. Higher-level protocols are required to ensure data integrity and proper sequencing.
TCP (Transmission Control Protocol) - TCP provides acknowledged, connection-oriented communications. It also provides guaranteed delivery, proper sequencing, and data integrity checks. Should errors occur during transmission, TCP is responsible for re-transmitting the data.
ICMP (Internet Control Message Protocol) - ICMP is used to control and manage information transmitted using TCP/IP. It allows nodes to share status and error information. This information can be passed to higher-level protocols, informing transmitting stations of unreachable hosts and to help with detection and resolution of transmission problems. It also helps to re-route messages when a router is busy or has failed.
ARP/RARP (Address Resolution Protocol/Reverse Address Resolution Protocol) ARP and RARP are maintenance protocols. They are used on Local Area Networks to enable hosts to translate IP addresses to the low level MAC addresses, which are needed to communicate at the Data Link level.
ARP is used to request a station's MAC (network adapter) address when only its IP address is known. Once obtained, this information is stored in the requesting system's ARP cache for later use. Since the information can be broadcast, it can also be used to update other systems. RARP is used when the MAC address in known, but not the IP address.
UDP (User Datagram Protocol) -UDP is designed for connectionless, unacknowledged communications. Using IP as its underlying protocol carrier, UDP adds information about the source and destination socket identifiers.
TELNET - TELNET may be more accurately described as a connectivity utility. It is a simple remote terminal emulation application, allowing one host to connect to and run a session on another.
FTP (File Transfer Protocol) - FTP supports file transport between dissimilar systems. Assuming sufficient rights, directory searches and file operations are supported.
SMTP (Simple Mail Transfer Protocol) - SMTP provides a mechanism for the exchange of mail information between systems. It is not concerned with the mail format, just the means by which it is transferred. SMTP is the most widely used service on the Internet.
DNS (Domain Name System) - Through DNS, a common naming convention is provided throughout the Internet. It is implemented as a distributed database supporting a hierarchical naming system.
NFS (Network File Services) - NFS is the industry standard for UNIX environment distributed file systems. It provides a common, transparent environment in which users can share files regardless of their hardware platform.
|
Politica de confidentialitate | Termeni si conditii de utilizare |

Vizualizari: 1829
Importanta: ![]()
Termeni si conditii de utilizare | Contact
© SCRIGROUP 2025 . All rights reserved